This is part 2 of my series demonstrating my rebuild of my homelab in NixOS.
- Initial creation of the NixOSVM on Proxmox Part 1 .
- Enabling SSH access on NixOS Part 2 . (This Part)
- Mounting a secondary drive on NixOS Part 3 .
- Decrypting boot early with initrd-ssh Part 4 .
- Installing Docker on NixOS Part 5
First Login to NixOS:
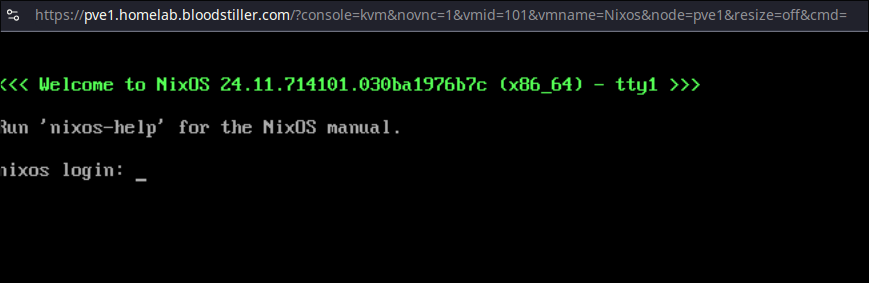
Lets start off where we left off in the last section, and we will login to the NixOS host for the first time.
As we are using Proxmox our first login will be via using the console, use the credentials you provided in the VM creation.
Making Login Easier:
As we don’t want to keep using the console in Proxmox we should add our ssh key so we can login. If you don’t have an ssh key I would recommend you follow this handy guide below, if you do please skip ahead to Enabling SSH Login On NixOS:
Creating An SSH Key:
SSH key authentication provides a more secure way to log into your servers compared to password-based authentication. This guide walks you through creating an ED25519 SSH key pair on your local machine - a modern, secure, and efficient choice for today’s authentication needs.
+Note+: This assumes your on linux.
Step 1: Generate An ED25519 SSH Key Pair
The first step is to create an SSH key pair using the ssh-keygen utility. While the default is RSA, we’ll specifically generate an ED25519 key, which offers superior security, performance, and smaller key sizes.
Run this command in your terminal:
ssh-keygen -t ed25519
You’ll see output similar to:
Generating public/private ed25519 key pair.
Enter file in which to save the key (/home/username/.ssh/id_ed25519):
Step 2: Choose A Location For Your Keys
The system will prompt you to select a location for storing your keys. By default, ED25519 SSH keys are stored in the ~/.ssh/ directory in your home folder:
- The private key will be named
id_ed25519 - The public key will be named
id_ed25519.pub
Recommendation: Press ENTER to accept the default location. This allows your SSH client to automatically find your keys when authenticating.
If you’ve previously generated ED25519 keys, you might see this warning:
/home/username/.ssh/id_ed25519 already exists.
Overwrite (y/n)?
+CAUTION+: If you choose to overwrite existing keys, you won’t be able to use the previous keys for authentication. This action cannot be reversed!
Step 3: Set A Passphrase (Recommended)
Next, you’ll be prompted to create a passphrase:
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
-
Why Use a Passphrase?
A passphrase adds an important layer of security to your key-based authentication:
- Protects your private key if your local machine is compromised
- Ensures that possession of the key file alone isn’t enough to gain access
- Prevents immediate unauthorized access if someone gains access to your computer
- Creates a two-factor authentication effect: something you have (the key) and something you know (the passphrase)
While optional, setting a strong passphrase is highly recommended. If you prefer not to use one, simply press ENTER to continue.
Step 4: Key Generation Complete
After successful generation, you’ll see output similar to:
Your identification has been saved in /home/username/.ssh/id_ed25519.
Your public key has been saved in /home/username/.ssh/id_ed25519.pub.
The key fingerprint is:
SHA256:naOuGUXEH9q5WDjVJRVl8g5VRvGFJCY4lj75mQYJ6vY username@hostname
The key's randomart image is:
+--[ED25519 256]--+
| . .... |
| o + .o . |
|. = + .. . |
| o = o o . |
|. o = o.S o |
|.+ o +.= + |
|o.+ + +.= . |
|.o + = .o.E |
|+ . . .+o. |
+----[SHA256]-----+
Congratulations! You now have a public and private ED25519 key pair. We now need to get this onto the host.
To view your public key for copying to a server, you can use:
cat ~/.ssh/id_ed25519.pub
-
Why ED25519?
ED25519 keys offer several advantages over the older RSA keys:
- Superior security: Uses modern elliptic curve cryptography
- Better performance: Faster operations for both key generation and authentication
- Smaller key size: Dramatically shorter keys (256 bits vs 3072+ bits for RSA) with equal or better security
- Resistant to side-channel attacks: More robust against certain types of cryptographic attacks
- Wide adoption: Supported by all modern SSH implementations (OpenSSH 6.5+)
The only reason to choose RSA instead would be for compatibility with very old systems that don’t support ED25519, but luckily we don’t need to worry about that.
- Additional Resources:
Understanding SSH Key Authentication Flow:
Before we configure SSH on our NixOS system, let’s understand how the SSH key authentication process works:
┌────────────────┐ ┌──────────────────┐
│ │ │ │
│ Your Machine │ │ NixOS Server │
│ │ │ │
└────────┬───────┘ └────────┬─────────┘
│ │
│ 1. Initiate SSH Connection │
│───────────────────────────────────────►│
│ │
│ 2. Send Server's Public Key │
│◄───────────────────────────────────────│
│ │
│ 3. Verify Server's Identity │
│ (First-time: Add to known_hosts) │
│ │
│ 4. Server Requests Authentication │
│◄───────────────────────────────────────│
│ │
│ 5. Client Sends "I want to use key" │
│───────────────────────────────────────►│
│ │
│ 6. Server Checks authorized_keys │
│ for Client's Public Key │
│ │
│ 7. Server Sends Encrypted Challenge │
│ (Encrypted with Client's Public Key)│
│◄───────────────────────────────────────│
│ │
│ 8. Client Decrypts Challenge │
│ with Private Key │
│ │
│ 9. Client Sends Signed Response │
│───────────────────────────────────────►│
│ │
│ 10. Server Verifies Response │
│ with Client's Public Key │
│ │
│ 11. Authentication Success! │
│◄───────────────────────────────────────│
│ │
│ 12. Encrypted SSH Session Established │
│◄═══════════════════════════════════════╡
│ │
┌────────┴───────┐ ┌────────┴─────────┐
│ │ │ │
│ Your Machine │ │ NixOS Server │
│ │ │ │
└────────────────┘ └──────────────────┘
The beauty of this process is that:
- Your private key never leaves your local machine
- Password-less, yet highly secure authentication
- The server verifies your identity cryptographically
- The entire session is encrypted after authentication
This is why we will set up SSH key authentication and disable password authentication - it’s both more convenient and more secure!
Enabling SSH Login On NixOS:
Now that you have your handy ssh key we need to copy it to the host and enable ssh login. To do this we need to edit the configuration.nix file, To do this type.
nano /etc/nixos/configuration.nix
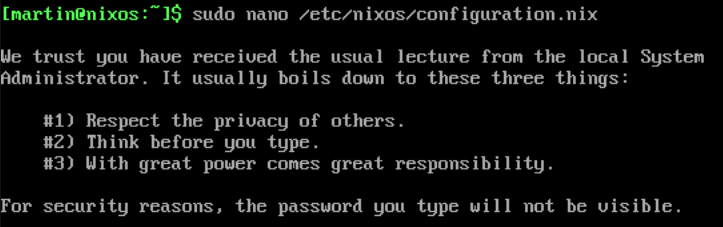
- +Note+: For this project we will do all our editing in the
configuration.nixfile.
Looking at the configuration.nix file for the first time can be overwhelming so we will make small changes as and when we need them. The first step is to get SSH enabled.
Scroll down until you see the below lines.
# Enable the OpenSSH daemon.
# services.openssh.enable = true;
We need to un-comment the second line and remove the hashtag so it reads, this way when we rebuild the SSH daemon will be enabled and we can login via ssh.
# Enable the OpenSSH daemon.
services.openssh.enable = true;
Press CTRL + X to exit, you will be prompted to save type Y and then hit ENTER
Baby’s First Rebuild:
Now we have made these changes we need to rebuild the system so the changes are reflected type the below command.
sudo nixos-rebuild switch
+Note+: You are going to get a lot of output here, this is just Nix rebuilding the system, downloading and enabling relevant packages & enabling the ssh service.
Understanding the NixOS Rebuild Process:
For those new to NixOS, the nixos-rebuild command is central to how the system works. Here’s what happens when you run it:
-
Configuration Evaluation: NixOS reads your configuration.nix file(s) and evaluates them to determine the desired system state.
-
Dependency Resolution: It calculates what packages and services need to be installed, upgraded, or configured based on changes to your configuration.
-
Build Phase:
- New packages are downloaded from binary caches (if available) or built from source
- System configuration files are generated
- Each package is stored in the Nix store with a unique hash-based path
-
Activation Phase:
- New system files are linked into place
- Services are started, restarted, or stopped as needed
- A new “generation” is created, allowing you to roll back if needed
-
Switch Action: The
switchargument tells NixOS to immediately activate the new configuration (alternatives includetestandboot)
This declarative approach ensures your system always matches exactly what’s in your configuration files - a key advantage of NixOS. Each rebuild creates a new system generation that you can roll back to from the boot menu if anything goes wrong.
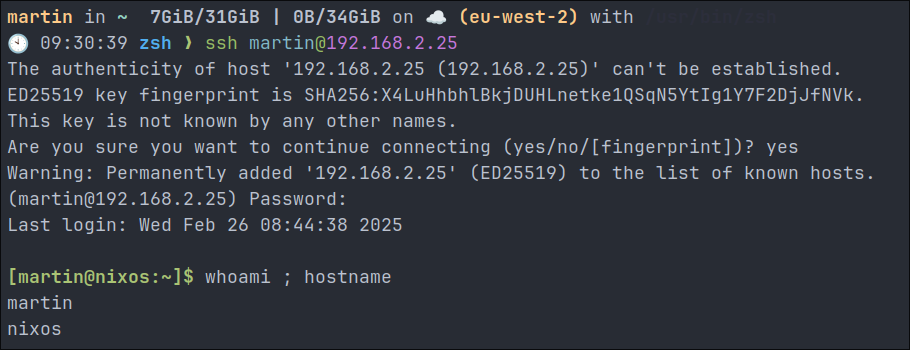
Login To The System VIA SSH & Password:
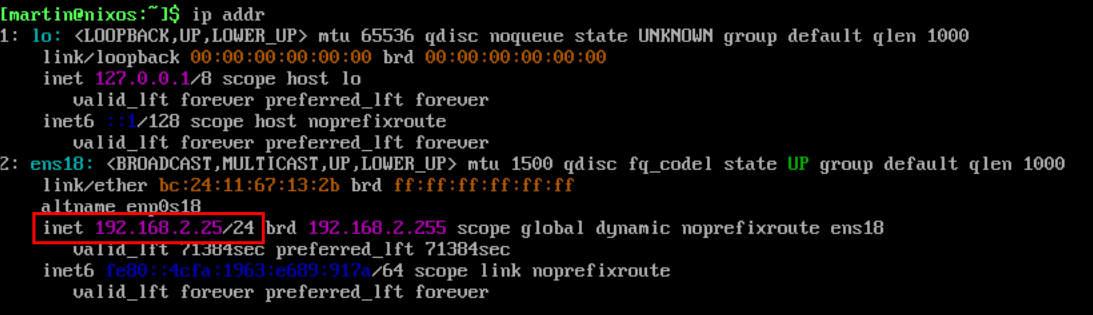
Lets grab the IP of our VM by running the below command.
ip addr
We can see the IP address of this host is 192.168.2.25, yours will be different!
Lets go to our terminal and login:
ssh [yourusername]@[yourNixOSBoxIP]
# Example
ssh [email protected]
As we can see we are prompted for our password, which at this moment is fine as we have not added our ssh key to the host.
Adding Your SSH Key To NixOS:
As we want to use our ssh keys we will now add our public key to the host & disable password authentication, we do this for security.
-
Open
configuration.nix:sudo nano /etc/nixos/configuration.nix -
Find the users section:
- Scroll down until you see the section below (note it will have your username not “martin”)
# Define a user account. Don't forget to set a password with 'passwd'. users.users.martin = { isNormalUser = true; description = "martin"; extraGroups = [ "networkmanager" "wheel" ]; packages = with pkgs; []; };
- Scroll down until you see the section below (note it will have your username not “martin”)
-
Get your public SSH key:
- We are going to add our ssh public key to this file so first we need to get the contents, on the host where you generated the key type the following.
cat ~/.ssh/id_ed25519.pub
- We are going to add our ssh public key to this file so first we need to get the contents, on the host where you generated the key type the following.
-
Add your public SSH key:
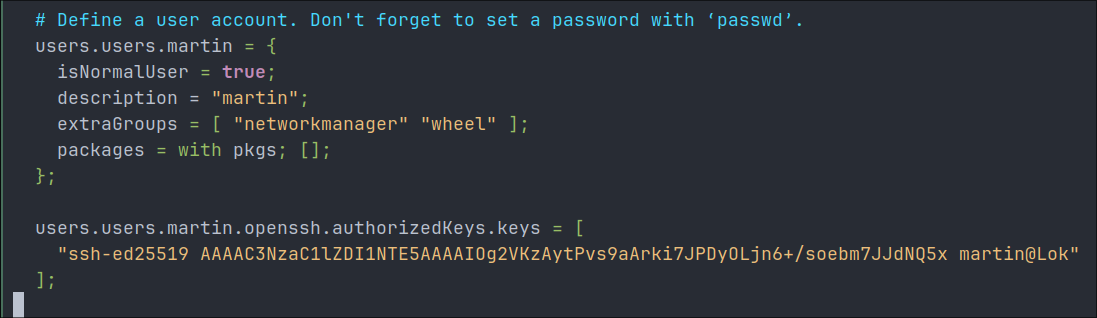
- Add the following line (adding your SSH key to the system) under the users section.
# Define a user account. Don't forget to set a password with 'passwd'. users.users.martin = { isNormalUser = true; description = "martin"; extraGroups = [ "networkmanager" "wheel" ]; packages = with pkgs; []; }; # Add this here users.users.martin.openssh.authorizedKeys.keys = [ "ssh-ed25519 YourActualSSHKEY" ]; - Here is how mines looks:
- Add the following line (adding your SSH key to the system) under the users section.
-
Disable Password Authentication and Root Login:
-
To do this lets find the original open ssh service line and we will modify it, it will look like the below.
# Enable the OpenSSH daemon. services.openssh.enable = true; -
Replace it with the below:
# SSH Server settings services.openssh = { enable = true; settings = { # Disable password authentication PasswordAuthentication = false; # Disable root login PermitRootLogin = "no"; # Only use SSH protocol version 2 Protocol = 2; }; };
-
-
Save and rebuild NixOS:
- After making these changes, save the file and rebuild your NixOS configuration:
sudo nixos-rebuild switch
- After making these changes, save the file and rebuild your NixOS configuration:
-
Test your SSH connection:
- Before closing your current session, open a new terminal and test that you can log in with your SSH key:
ssh username@your-nixos-ip - If successful, you should be able to log in without entering a password
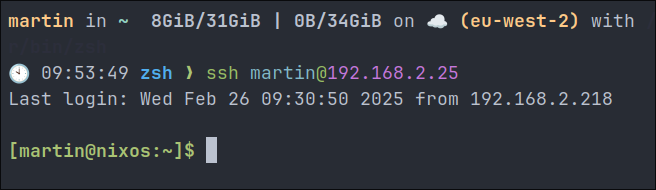
- Before closing your current session, open a new terminal and test that you can log in with your SSH key:
This post has went on long enough in the next part we will start to install packages.
Signoff:
As always hack the planet homelab!