Lab 6: 2FA simple bypass:
This lab’s two-factor authentication can be bypassed. You have already obtained a valid username and password, but do not have access to the user’s 2FA verification code. To solve the lab, access Carlos’s account page.
Your credentials: wiener:peter Victim’s credentials carlos:montoya
Initial Reconnaissance/Discovery:
Looking at the application we have access to a simple web app with a login page as well as an email client.
Let’s login with our credentials to see the login process.
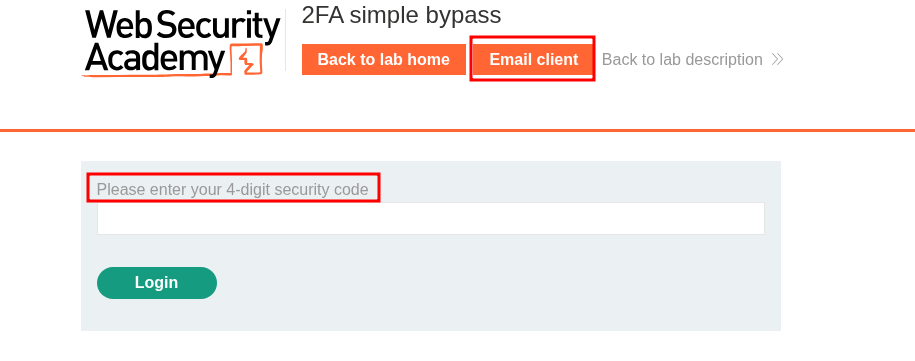
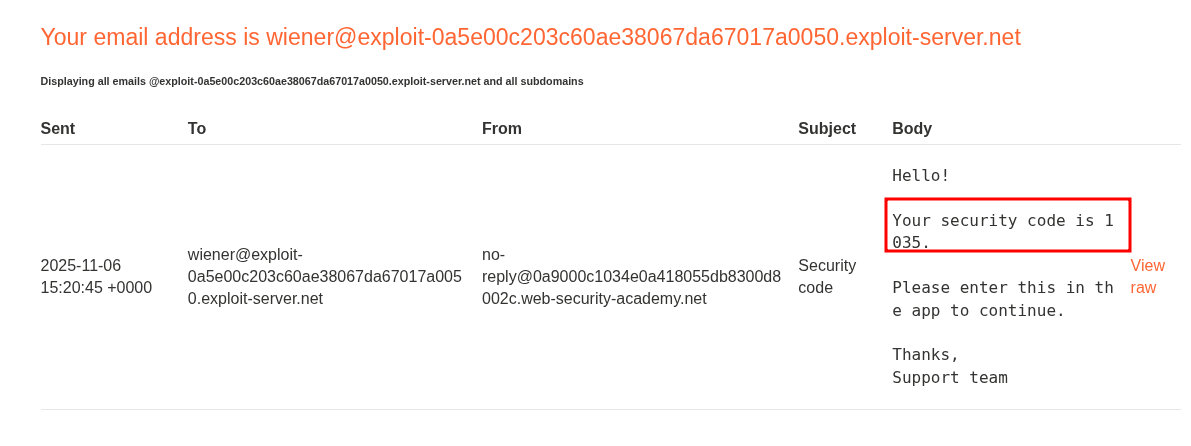
We can see that when we login we are prompted for a 2FA code. If we check out email client we can see it’s been emailed.
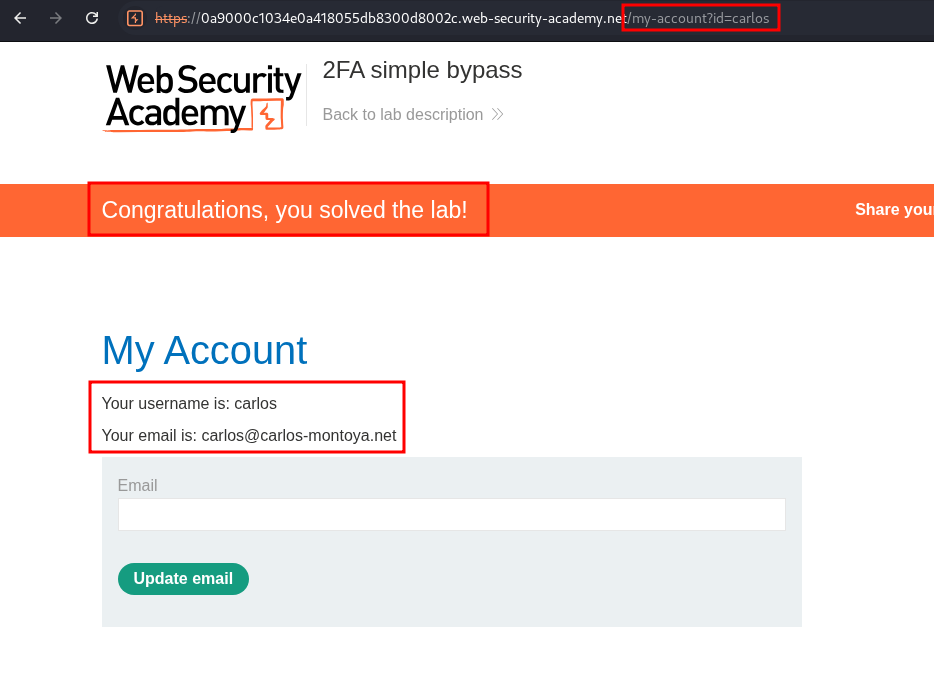
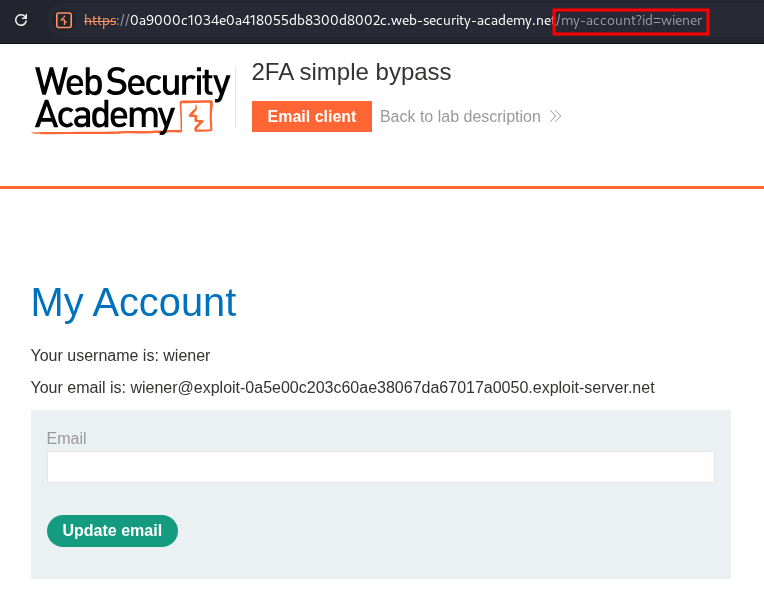
After entering the code we can see we are directed to the /my-account?id=[username] page.
Bypassing 2FA Login:
If we re-read the previous section before the lab can see it says the below.
If the user is first prompted to enter a password, and then prompted to enter a verification code on a separate page, the user is effectively in a “logged in” state before they have entered the verification code. In this case, it is worth testing to see if you can directly skip to “logged-in only” pages after completing the first authentication step. Occasionally, you will find that a website doesn’t actually check whether or not you completed the second step before loading the page.
Using this logic, let’s login as our user and then manually navigate straight to the my-account page and see if it works.
Once presented the 2FA page we can manually change the address as we are “technically” logged in as carlos already.
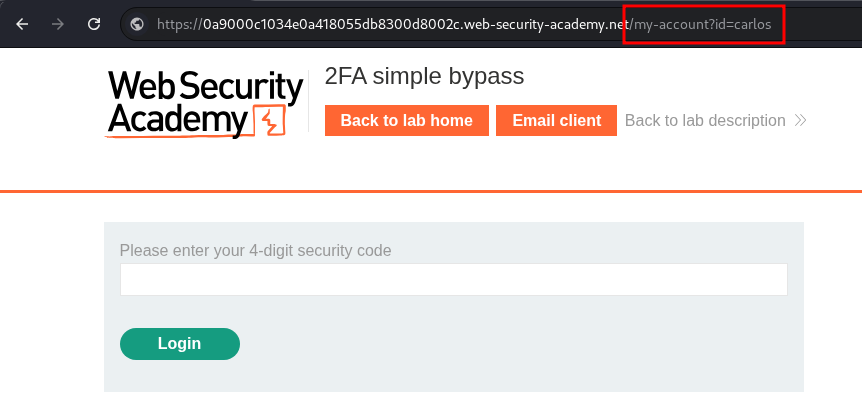
Once we do & hit enter we can see we bypass the 2FA check and are logged in as carlos.