Troubleshooting Common Docker Build Issues: A Comprehensive Guide
Introduction
Docker has revolutionized how we package and deploy applications, but the build process can sometimes be challenging, with obtuse errors and lots of troubleshooting, I’m looking at you GO dependencies. This guide will help you identify, understand, and resolve common Docker build issues.
Common Docker Build Issues and Solutions
1. Base Image Issues
-
Problem: Unavailable or Incorrect Base Images
When building a Docker image, you need to start with a base image (specified by the FROM instruction). Sometimes the build fails because the base image doesn’t exist, can’t be found, or you’ve made a typo in the image name. This is like trying to build a house on a foundation that isn’t there - it’s impossible to proceed without a valid base image.
Example of a failing Dockerfile:
FROM nonexistent:latest # Rest of Dockerfile
-
Solutions:
- Verify the base image name and tag
- Check if the image exists on Docker Hub or your private registry
- Ensure proper authentication for private registries
- Consider using official images or well-maintained alternatives
-
Practical Implementation:
# Check if image exists locally docker images | grep ubuntu # Pull and verify specific version docker pull ubuntu:22.04 docker image inspect ubuntu:22.04 # Search Docker Hub docker search ubuntu # Configure private registry docker login registry.example.com
2. Dependency Resolution Problems
-
Problem: Missing or Failed Package Installation
One of the most common issues when building Docker images is failing to install packages or dependencies correctly. This usually happens because the package manager’s database isn’t updated before trying to install packages, or because you’re trying to install packages that don’t exist. It’s similar to trying to shop at a store using an outdated catalog - you need to update your list of available items first.
Example of a failing installation:
FROM ubuntu:22.04 RUN apt-get install python3 # This will fail because apt database isn't updated
-
Solution:
Always update package managers before installing & combine run commands to reduce the amount of layers.
FROM ubuntu:22.04 RUN apt-get update && apt-get install -y \ python3 \ && rm -rf /var/lib/apt/lists/*
-
Best Practices:
- Always update package managers before installing
- Combine RUN commands to reduce layers
- Clean up package manager caches
- Use version pinning for stability
-
Practical Implementation:
# Good practice - combining updates and cleanup FROM ubuntu:22.04 # Set noninteractive installation ENV DEBIAN_FRONTEND=noninteractive # Combine commands and cleanup in single layer RUN apt-get update && \ apt-get install -y \ python3 \ python3-pip \ && rm -rf /var/lib/apt/lists/* \ && apt-get clean # Pin specific versions RUN pip3 install requests==2.28.1
3. Build Context and Cache Issues
-
Problem: Slow Builds or Unexpected Caching
Docker builds can become painfully slow or behave unexpectedly due to large build contexts (all the files Docker needs to copy into the image) or cache-related issues. Think of it like trying to send a huge email attachment when you only need a small file - the unnecessary files slow down the process. Additionally, Docker’s caching mechanism, while usually helpful, can sometimes use outdated cached layers when you actually need fresh ones.
-
Solutions:
- Use
.dockerignoreto exclude unnecessary files - Organize Dockerfile commands from least to most frequently changing
- Use multi-stage builds for complex applications
- Clear cache when needed:
docker build --no-cache
- Use
-
Practical Implementation:
# Create .dockerignore cat > .dockerignore <<EOF .git .env *.log node_modules __pycache__ *.pyc EOF # Check build context size docker build --no-cache . 2>&1 | grep "Sending build context" # Use specific build context docker build -f Dockerfile -t myapp:latest subdir/
4. Permission and Ownership Issues
-
Problem: Access Denied Errors
Permission issues occur when Docker can’t access files it needs to copy into the image, or when processes inside the container don’t have the right permissions to access files or directories. This is similar to being locked out of a room because you don’t have the right key. These issues are especially common when working with mounted volumes or when trying to run applications as non-root users.
-
Solutions:
- Set appropriate permissions before COPY
- Use
--chownflag with COPY/ADD - Consider creating and using non-root users
-
Practical Implementation:
# Create non-root user and set permissions properly FROM ubuntu:22.04 # Create user and group RUN groupadd -r appgroup && useradd -r -g appgroup appuser # Set ownership during COPY COPY --chown=appuser:appgroup ./app /app # Set permissions RUN chmod 755 /app/script.sh # Switch to non-root user USER appuser CMD ["/app/script.sh"]
5. Resource Constraints
-
Problem: Build Failures Due to Resource Exhaustion
Sometimes Docker builds fail because your system runs out of resources - memory, CPU, or disk space. This is like trying to cook in a kitchen that’s too small or with a stove that’s not powerful enough. Large builds, especially those involving compilation or processing of big datasets, can consume significant resources. When Docker runs out of resources, it may fail abruptly or become extremely slow.
-
Solutions:
- Increase Docker resource limits
- Optimize build steps to reduce resource usage
- Implement multi-stage builds to reduce final image size
- Clean up unused images and containers regularly
-
Practical Implementation:
# Set resource limits during build docker build --memory=2g --cpu-quota=150000 -t myapp . # Clean up system resources docker system prune -af --volumes # Configure buildkit resource limits export BUILDKIT_STEP_MEMORY_LIMIT=2g export BUILDKIT_STEP_TIMEOUT=3600
6. Network-Related Build Issues
-
Problem: Network Connection Failures
Network issues can prevent Docker from downloading necessary components during the build process. This commonly happens in corporate environments with proxies, when DNS resolution fails, or when you hit rate limits from package repositories. It’s similar to trying to download a file with a poor internet connection - the process fails because Docker can’t reach the resources it needs.
-
Solutions:
- Configure Docker to use proper proxy settings
# In /etc/docker/daemon.json { "dns": ["8.8.8.8", "8.8.4.4"], "http-proxy": "http://proxy.example.com:80", "https-proxy": "https://proxy.example.com:443", "no-proxy": "localhost,127.0.0.1" }- Use build arguments for flexible proxy configuration
ARG HTTP_PROXY ARG HTTPS_PROXY ENV http_proxy=$HTTP_PROXY ENV https_proxy=$HTTPS_PROXY RUN apt-get update && apt-get install -y ...
-
Practical Implementation:
# Configure system-wide proxy cat > /etc/systemd/system/docker.service.d/http-proxy.conf <<EOF [Service] Environment="HTTP_PROXY=http://proxy.example.com:80" Environment="HTTPS_PROXY=https://proxy.example.com:443" Environment="NO_PROXY=localhost,127.0.0.1" EOF systemctl daemon-reload systemctl restart docker # In Dockerfile FROM ubuntu:22.04 ARG HTTP_PROXY ARG HTTPS_PROXY ENV http_proxy=$HTTP_PROXY ENV https_proxy=$HTTPS_PROXY RUN apt-get update && apt-get install -y ...
Troubleshooting Checklist
The troubleshooting checklist is your first line of defense when Docker builds fail. Like a pilot’s pre-flight checklist, going through these items systematically helps catch common issues before they become bigger problems. Let’s look at each area we need to verify.
Build Environment
Before diving into specific issues, it’s important to verify your basic build environment. Think of this like checking if you have all your tools and workspace ready before starting a project. A proper build environment needs adequate resources, a running Docker daemon, and network connectivity to download necessary components.
- Sufficient disk space
# Check available space
df -h /var/lib/docker
# Check Docker disk usage
docker system df
# Clean up if needed
docker system prune -af --volumes
- Adequate memory and CPU
# Check system resources
free -h
# View CPU info
nproc
lscpu
# Monitor Docker resource usage
docker stats
- Docker daemon running
# Check daemon status
systemctl status docker
# Start if not running
sudo systemctl start docker
# Enable on boot
sudo systemctl enable docker
- Network connectivity
# Test Docker Hub connectivity
ping -c 3 registry.hub.docker.com
# Test Docker registry API
curl -v https://registry.hub.docker.com/v2/
# Check DNS resolution
dig registry.hub.docker.com
# Test docker pull
docker pull hello-world
-
Practical Implementation:
# Check disk space df -h /var/lib/docker # Check Docker system resources docker system df -v # Verify Docker daemon status systemctl status docker # Test network connectivity ping -c 3 registry.hub.docker.com curl -v https://registry.hub.docker.com/v2/
Dockerfile Validation
Dockerfile validation is like proofreading your recipe before cooking - it helps catch basic mistakes before they cause problems. This includes checking for syntax errors, making sure your base image exists, and verifying that your commands are in a logical order. Many build failures can be prevented by validating your Dockerfile before running the build.
- Syntax correctness
- Base image availability
- Command ordering
- Layer optimization
-
Practical Implementation:
# Test base image pull docker pull mybase:latest # Analyze layers docker history myimage:latest # Lint Dockerfile using hadolint (install first) docker run --rm -i hadolint/hadolint < DockerfileExampleof hadolint output giving us warnings.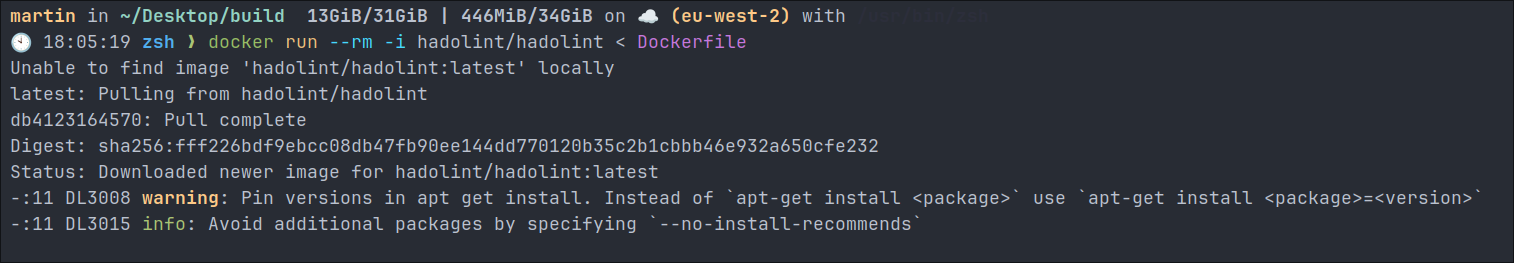
- You can also use VS Code etc which have good dockerfile linters.
Dependencies
Managing dependencies is like ensuring you have all the ingredients before starting to cook. Your application needs various packages and libraries to run, and these need to be properly specified and installed. Common issues include missing packages, version conflicts, and network problems when trying to download dependencies.
- Package manager updates
- Correct package names
- Version compatibility
- Network access to repositories
-
Practical Implementation:
# Example of proper dependency management FROM ubuntu:22.04 # Pin versions explicitly RUN apt-get update && apt-get install -y \ python3=3.10.* \ python3-pip=22.0.* \ && rm -rf /var/lib/apt/lists/* # Use requirements.txt with fixed versions COPY requirements.txt . RUN pip3 install -r requirements.txt
Permissions
Permission issues in Docker are like having the right key but not the right access level. This section helps you understand how to properly set up file ownership and access rights, both inside the container and for mounted volumes. Getting permissions wrong can lead to applications failing to start or access necessary files.
- File ownership
- Directory permissions
- User context
- Volume mounts
-
Practical Implementation:
# Check and fix host permissions chmod -R 755 ./app chown -R 1000:1000 ./app # Verify volume permissions docker run --rm -v $(pwd)/app:/app busybox ls -la /app
Debug Commands and Tools
When things go wrong, having the right debugging tools is essential. This section covers various commands and techniques for investigating build failures, inspecting images, and troubleshooting running containers. Think of these as your diagnostic tools - like a mechanic’s toolkit for Docker containers.
-
Additional Debugging Examples:
# Debug layer by layer docker build --no-cache . # Export container filesystem for inspection docker export mycontainer > container.tar # Inspect build cache docker builder prune --filter until=24h # Check build logs with timestamp docker build --no-cache . 2>&1 | while read line; do echo "[$(date '+%Y-%m-%d %H:%M:%S')] $line"; done- The last option will prepend the build output with timestamps.
- +Example Output Below+
martin in ~/Desktop/build 13GiB/31GiB | 445MiB/34GiB on ☁️ (eu-west-2) with /usr/bin/zsh 🕙 17:55:51 zsh ❯ docker build --no-cache . 2>&1 | while read line; do echo "[$(date '+%Y-%m-%d %H:%M:%S')] $line"; done [2025-03-11 17:56:18] DEPRECATED: The legacy builder is deprecated and will be removed in a future release. [2025-03-11 17:56:18] Install the buildx component to build images with BuildKit: [2025-03-11 17:56:18] https://docs.docker.com/go/buildx/ [2025-03-11 17:56:18] [2025-03-11 17:56:18] Sending build context to Docker daemon 2.56kB [2025-03-11 17:56:18] Step 1/5 : FROM ubuntu:24.04 [2025-03-11 17:56:18] ---> a04dc4851cbc [2025-03-11 17:56:18] Step 2/5 : RUN sed -i 's/# (.*multiverse$)/1/g' /etc/apt/sources.list && apt-get update && apt-get -y upgrade && apt-get install -y build-essential && apt-get install -y software-properties-common && apt-get install -y byobu curl git htop man unzip vim wget && rm -rf /var/lib/apt/lists/* [2025-03-11 17:56:18] ---> Running in 36c592ab27f1 [2025-03-11 17:56:23] Get:1 http://archive.ubuntu.com/ubuntu noble InRelease [256 kB] [2025-03-11 17:56:23] Get:2 http://security.ubuntu.com/ubuntu noble-security InRelease [126 kB] [2025-03-11 17:56:23] Get:3 http://archive.ubuntu.com/ubuntu noble-updates InRelease [126 kB] [2025-03-11 17:56:23] Get:4 http://security.ubuntu.com/ubuntu noble-security/multiverse amd64 Packages [34.0 kB] [2025-03-11 17:56:23] Get:5 http://archive.ubuntu.com/ubuntu noble-backports InRelease [126 kB]
- +Example Output Below+
- The last option will prepend the build output with timestamps.
Security Considerations During Builds
Scanning for Vulnerabilities
Security scanning is like having a security guard check your building for weaknesses. Container images can contain vulnerabilities in their packages or configurations that could be exploited. Regular scanning helps identify and fix these security issues before they become problems in production.
Best Practices
Security best practices are your guidelines for building secure containers. Just like you wouldn’t leave your house with all the windows open, you shouldn’t build containers without following security principles. This includes minimizing installed packages, using specific versions, and following the principle of least privilege.
-
Practical Implementation:
# Using Trivy scanner trivy image myimage:latest # Check for sensitive data in layers docker history --no-trunc myimage:latest # Audit image content docker run --rm -it myimage:latest find / -perm -4000 2>/dev/null
-
Practical Implementation:
# Example of secure Dockerfile practices FROM ubuntu:22.04 AS builder # Add specific user RUN groupadd -r appuser && useradd -r -g appuser appuser # Pin versions and minimize layers RUN apt-get update && apt-get install -y \ python3=3.10.* \ && rm -rf /var/lib/apt/lists/* # Use multi-stage to reduce attack surface FROM gcr.io/distroless/python3 COPY --from=builder /app /app USER nonroot ENTRYPOINT ["python3", "/app/main.py"]
Build Performance Optimization
Layer Optimization
Layer optimization is like organizing your workspace efficiently. Each layer in a Docker image adds to the final size and build time. By organizing your layers smartly and combining related commands, you can make your builds faster and your images smaller.
-
Practical Implementation:
# Example of optimized layer caching FROM node:16-slim # Cache dependencies layer COPY package*.json ./ RUN npm ci # Cache build layer COPY tsconfig.json ./ COPY src/ src/ RUN npm run build # Runtime layer FROM node:16-slim COPY --from=0 /app/dist ./dist COPY package*.json ./ RUN npm ci --only=production CMD ["node", "dist/main.js"]
BuildKit Features
BuildKit is Docker’s advanced building toolkit, offering features like better caching, parallel building, and secure secret handling. It’s like having a more sophisticated set of tools that can make your builds faster and more secure. Understanding these features can significantly improve your Docker build experience.
-
Practical Implementation:
# syntax=docker/dockerfile:1.4 FROM ubuntu:22.04 RUN --mount=type=cache,target=/var/cache/apt \ apt-get update && apt-get install -y python3
-
Additional BuildKit Examples:
# syntax=docker/dockerfile:1.4 FROM ubuntu:22.04 # Mount cache for apt RUN --mount=type=cache,target=/var/cache/apt \ --mount=type=cache,target=/var/lib/apt \ apt-get update && apt-get install -y python3 # Mount secrets RUN --mount=type=secret,id=mysecret,target=/secret.txt \ cat /secret.txt > /app/config # Mount SSH for private repos RUN --mount=type=ssh git clone [email protected]:org/repo.git